Software Engineering Institute
Cite this post.
AMS Citation
McAllister, J., 2016: Cyber Intelligence and Critical Thinking. Carnegie Mellon University, Software Engineering Institute's Insights (blog), Accessed September 13, 2024, https://insights.sei.cmu.edu/blog/cyber-intelligence-and-critical-thinking/.
APA Citation
McAllister, J. (2016, February 15). Cyber Intelligence and Critical Thinking. Retrieved September 13, 2024, from https://insights.sei.cmu.edu/blog/cyber-intelligence-and-critical-thinking/.
Chicago Citation
McAllister, Jay. "Cyber Intelligence and Critical Thinking." Carnegie Mellon University, Software Engineering Institute's Insights (blog) . Carnegie Mellon's Software Engineering Institute, February 15, 2016. https://insights.sei.cmu.edu/blog/cyber-intelligence-and-critical-thinking/.
IEEE Citation
J. McAllister, "Cyber Intelligence and Critical Thinking," Carnegie Mellon University, Software Engineering Institute's Insights (blog) . Carnegie Mellon's Software Engineering Institute, 15-Feb-2016 [Online]. Available: https://insights.sei.cmu.edu/blog/cyber-intelligence-and-critical-thinking/. [Accessed: 13-Sep-2024].
BibTeX Code
@misc{mcallister_2016, author={McAllister, Jay}, title={Cyber Intelligence and Critical Thinking}, month={Feb}, year={2016}, howpublished={Carnegie Mellon University, Software Engineering Institute's Insights (blog)}, url={https://insights.sei.cmu.edu/blog/cyber-intelligence-and-critical-thinking/}, note={Accessed: 2024-Sep-13} }

Cyber Intelligence and Critical Thinking
Jay mcallister, february 15, 2016.
In June, representatives of organizations in the government, military, and industry sectors--including American Express and PNC--traveled to Pittsburgh to participate in a crisis simulation the SEI conducted. The crisis simulation--a collaborative effort involving experts from the SEI's Emerging Technology Center (ETC) and CERT Division --involved a scenario that asked members to sift through and identify Internet Protocol (IP) locations of different servers, as well as netflow data. Participants also sorted through social media accounts from simulated intelligence agencies, as well as fabricated phone logs and human intelligence. Our aim with this exercise was to help cyber intelligence analysts from various agencies learn to think critically about the information they were digesting and make decisions that will protect their organizations in the event of a cyber attack or incident and increase resilience against future incidents. This blog post, the second in a series highlighting cyber intelligence work from the ETC , highlights the importance of critical thinking in cyber intelligence, as well as a three-step approach to taking a more holistic view of cyber threats.
The importance of applying critical thinking to cyber intelligence cannot be overstated. In our work with organizations, we have noticed that when a new threat arises, instead of holistically assessing it, organizations often simply request the latest, greatest analytic tool or contract out the work to third-party intelligence providers. As a former intelligence analyst--prior to joining the SEI, I served as a counterintelligence and counterterrorism analyst for the Naval Criminal Investigative Service (NCIS) --I know from experience that the operational tempo required for intelligence analysts to keep pace with the ever-changing cyber environment is overwhelming at best. While technology and external resources offer value, analysts also need to critically assess the information they receive.
In 2013, the Defense Science Board echoed a similar sentiment. In their report, Resilient Military Systems and the Advanced Cyber Threat they included the following among their recommendations to improve DoD systems' resilience: "Refocus intelligence collection and analysis to understand adversarial cyber capabilities, plans and intentions, and to enable counterstrategies."
Foundations of Our Work
Our work in cyber intelligence started in 2012 with a request from the government to assess the state of the practice of cyber intelligence. Our work on that initial project involved an examination of the cyber intelligence practices of 30 organizations (6 from government and 24 from industry), specifically their strategic approaches to cyber intelligence. Our work focused on identifying the methodologies, processes, tools and training that shaped how these organizations assessed and analyzed cyber threats. As detailed in an earlier blog post , our work on this project resulted in an implementation framework that captured best practices.
When this work concluded, several participant organizations approached the ETC about leading an effort that would research and develop technical solutions and analytical practices to help people make better judgments and quicker decisions with cyber intelligence. As a result, ETC launched the Cyber Intelligence Research Consortium .
The first year of this consortium focused primarily on continuing our research in cyber intelligence, as well as identifying best practices and challenges. Nearly four years after our initial research began, we have noted clear examples of a strategic shift among participant organizations with respect to cyber intelligence. They are investing resources in hiring intelligence analysts from a pool of vetted and qualified experts, and they are investing significant resources in acquiring tools and tradecraft. However, they are not yet making effective use of the intelligence provided by these resources.
In both government and industry, organizational resilience in the wake of an attack relies on an analyst's ability to holistically assess a threat. The remainder of this post proposes a three-step approach for holistically approaching a cyber threat.
Three Steps to Holistically Assess Cyber Threats
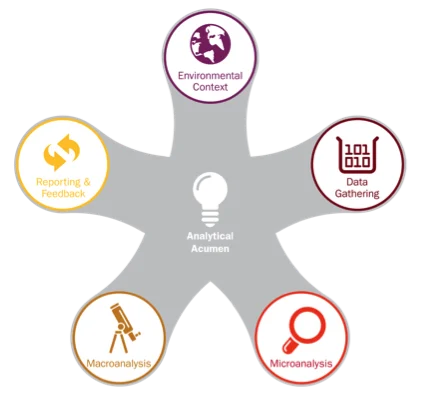
First and foremost, applying critical thinking--which brings together all the skills shown in the "conceptual framework" above--to cyber threats improves an analyst's ability to accurately evaluate and estimate a threat's potential to impact and expose its target. My ETC colleagues and I propose a three-step approach to holistically assess cyber threats:
- Establish a baseline of how the threat will be analyzed . This step involves outlining the approach so that the analyst uses all the skills represented in the conceptual framework . Since the framework is non-linear, the components can be approached in whatever order makes sense.
- Leverage creative brainstorming. When facing a potential cyber threat, analysts don't have the luxury of time to stare into space and wait for an "ah ha" moment. Creative brainstorming techniques such as those found in human-centered design accelerate the time it takes to get to an "ah ha" moment. To enhance an analyst's creative brainstorming skills, I recommend looking at recent brainstorming research including that by Luma Institute , specifically their 36 techniques for creative brainstorming and practice them daily.
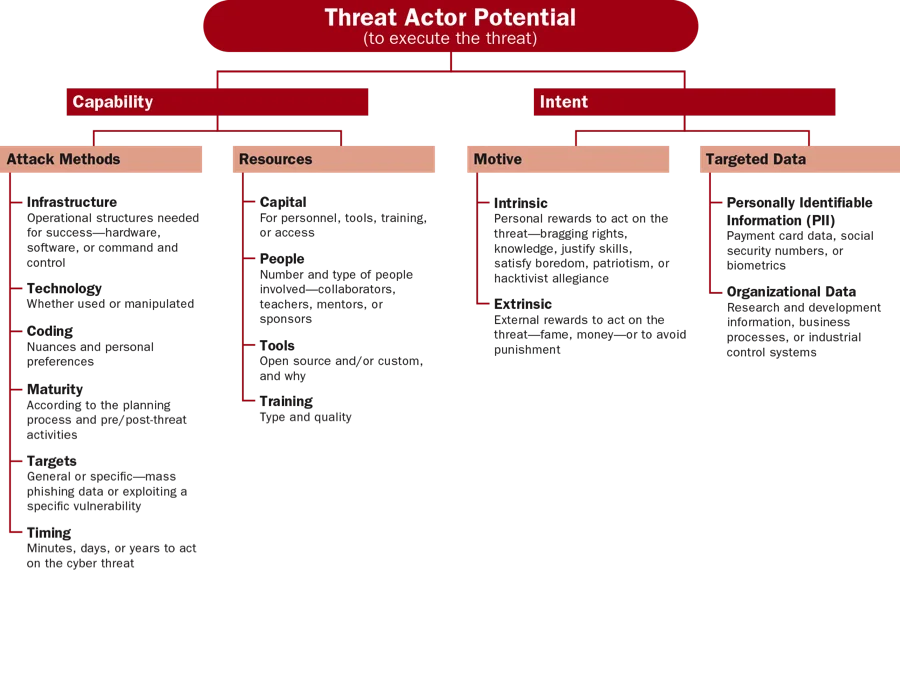
- Perform the holistic threat assessment. The assessment evaluates the threat from the three perspectives shown in the figures below:
The three steps outlined in this approach enable analysts to avoid intelligence tunnel vision and seek to understand all causes and effects of relevant threats, which can significantly improve the efficiency and effectiveness of cyber intelligence efforts.
Two Case Studies
This section presents two examples of how a holistic approach to cyber intelligence improved an organization's ability to counteract cyber threat.
- A civil service federal government agency was monitoring open source publications from an entity known to sponsor cyber threat actors who frequently targeted the agency. By examining threat actor potential, organizational impact, and target exposure, the agency came to understand the motivations of the sponsored cyber threat actors, what effects a successful attack might have on the organization, and what vulnerabilities existed that exposed the agency to the threat. This approach enabled the agency's analysts to narrow down the types of data likely to be targeted, to work with network security experts to create diversions and honey pots , and to proactively defend against the threat.
- An organization we worked with from the retail sector focused on the extracurricular activities of its CEO, who was active with companies, non-profits, and policy institutes in a capacity that had nothing to do with his responsibilities at the retail company. The company's cyber intelligence analysts knew this and maintained an awareness of his activities, so when hacktivists publicly threatened attacks against one of the institutes, the analysts knew this could have implications for the retail organization. This attention to target exposure (their CEO's connection with a targeted entity), along with an examination of threat actor potential and organizational impact, enabled analysts to prepare for and successfully stop the attack that eventually happened.
Wrapping Up and Looking Ahead
While the ETC will continue in its efforts to combat the dizzying operational tempo of cyber intelligence with technology, it is equally important to focus on enhancing analytical brainpower. As intelligence analysis pioneer Dr. Richards J. Heuer once observed,
Analysts at all levels devote little attention to improving how they think. To penetrate the heart and soul of improving analysis, it is necessary to better understand, influence, and guide the mental processes of analysts themselves.
There is an elegance involved in designing, developing, and delivering ways for analysts to enhance critical thinking skills. We are working on several fronts to help intelligence analysts acquire these skills:
- I teach a graduate-level strategic cyber intelligence course through Carnegie Mellon's Information Networking Institute (INI); the second offering of the course wrapped up at the end of the fall semester, and I plan to teach it again in Fall 2016. In that class, I emphasize the importance of taking a holistic approach to analyzing cyber threats. My colleague, Jared Ettinger, and I also are working with INI to develop a second cyber intelligence course to be taught for the first time in spring 2017.
- Our Cyber Intelligence Research Consortium is continuing to meet and work on real cyber intelligence problems facing real organizations. We will hold a tradecraft lab in April featuring cyber intelligence experts, discussion amongst members, and output of student projects being run through CMU's Heinz College about cyber intelligence strategy. We are also in the early stages of planning for another crisis simulation for August 2016.
We welcome your feedback on this research and suggestions for future posts in the comments section below.
Additional Resources
View the slides for my presentation, Be Like Water Applying Analytical Adaptability to Cyber Intelligence , which I presented at the 2015 RSA Conference.
Learn more about the ETC's Cyber Intelligence Research Consortium .
Digital Library Publications
Send a message, get updates on our latest work..
Sign up to have the latest post sent to your inbox weekly.
Each week, our researchers write about the latest in software engineering, cybersecurity and artificial intelligence. Sign up to get the latest post sent to your inbox the day it's published.
Critical Thinking and Effective Communication in Security Domains
- Living reference work entry
- First Online: 21 January 2022
- Cite this living reference work entry

- Cihan Aydiner 2
59 Accesses
This chapter explores the critical thinking and effective communication skills in security domains both for educational and professional settings. The literature shows the gap among research, learning goals, teaching, and practice of critical thinking and effective communication skills in education and training. So, this study aims to create a starting guidance document to improve these skills in security domains with a direct approach. This study conceptualizes these skills as shown in the literature and shows the barriers as well as strategies to prevent barriers for critical thinking and effective communication developments. Also, it provides examples to teach these skills in security domains by asking appropriate questions, using selected red teaming techniques, and discussing recommendations for effective communication. This study asserts that direct approaches to teaching and applying critical thinking and effective communication skills may be more productive than indirect approaches in education and practice. Also, the chapter argues that supporting direct strategies by providing required resources to faculty and professionals in the field is an essential step for effective teaching of these skills. Further studies are encouraged to provide specific and practical examples to develop critical thinking and effective communication skills in subfields of security domains.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
Institutional subscriptions
Similar content being viewed by others

Making Waves Through Education: A Method for Addressing Security Grand Challenges in Educational Contexts

Developing an effective and comprehensive communication curriculum for undergraduate medical education in Poland – the review and recommendations
Ackerman GA, Clifford D (2019) Towards a definition of red teaming. Center for advanced red teaming. University at Albany, Albany. Available via https://www.albany.edu/sites/default/files/2019-11/CART%20Definition.pdf . Accessed 10 Dec 2021
Google Scholar
Bailenson JN (2021) Nonverbal overload: a theoretical argument for the causes of zoom fatigue. Technol Mind Behav. Available via https://tmb.apaopen.org/pub/nonverbal-overload/release/2 . Accessed 10 Dec 2021
Bailin S, Case R, Coombs JR, Daniels LB (1999) Conceptualizing critical thinking. J Curric Stud:285–302
Baybutt P (2016) A framework for critical thinking in process safety management. Process Saf Prog:337–340. Available via https://aiche-onlinelibrary-wiley-com.ezproxy.libproxy.db.erau.edu/doi/10.1002/prs.11858 . Accessed 10 Dec 2021
Bellaera L, Weinstein-Jones Y, Ilie S, Baker ST (2021) Critical thinking in practice: the priorities and practices of instructors teaching in higher education.. Thinking Skills and Creativity. Available via https://www.sciencedirect.com/science/article/abs/pii/S1871187121000717 . Accessed 10 Dec 2021
Betts K (2009) Lost in translation: importance of effective communication in online education. Online J Distance Learn Adm 12:2. Available via https://eric.ed.gov/?id=EJ869279 . Accessed 10 Dec 2021
Bloom BS (1956) Taxonomy of educational objectives. Handbook I: the cognitive domain. David McKay Co. Inc., New York
Bloom BS (1973) Taxonomy of educational objectives, the classification of educational goals. Handbook II: the affective domain. David McKay Co. Inc., New York
Browne MN, Keeley SM (2018) Asking the right questions: a guide to critical thinking, 12th edn. Pearson, New York
Cozine K (2015) Thinking interestingly: the use of game play to enhance learning and facilitate critical thinking within a homeland security curriculum. Br J Educ Stud 63(3):367–385. https://doi.org/10.1080/00071005.2015.1069256
Article Google Scholar
DeFilippis E, Impink SM, Singell M, Polzer JT, Sadun R (2020) Collaborating during coronavirus: the impact of COVID-19 on the nature of work. National Bureau of Economic Research. Working paper 27612. Available via https://www.nber.org/papers/w27612 . Accessed 10 Dec 2021
Erickson BL, Peters CB, Strommer DW (2006) Teaching first-year college students: revised and expanded edition of teaching college freshmen. Jossey-Bass, San Francisco
Erikson MG, Erikson M (2019) Learning outcomes and critical thinking – good intentions in conflict. Stud High Educ 44(12):2293–2303. https://doi.org/10.1080/03075079.2018.1486813
Glaser EM (1941) An experiment in the development of critical thinking. Teacher’s College, Columbia University
Griffin RW (2016) Fundamentals of management. South-Western Cengage Learning, Mason
Isaias P, Issa T (2014) Promoting communication skills for information systems students in Australian and Portuguese higher education: action research study. Educ Inf Technol 19:841–861. https://doi.org/10.1007/s10639-013-9257-9
Joly H, Lambert C (2021) The heart of business: leadership principles for the next era of capitalism. Harvard Business Review Press, Boston
Jonassen DH (2000) Toward a design theory of problem solving. Educ Technol Res Dev 48(4):63–85. https://doi.org/10.1007/BF02300500
Kardos M, Dexter P (2017) A simple handbook for non-traditional red teaming, Australian Government Department of Defense, Joint & Operations Analysis Division, 26. Available via https://apps.dtic.mil/dtic/tr/fulltext/u2/1027344.pdf . Accessed 10 Dec 2021
Kiltz L (2009) Developing critical thinking skills in homeland security and emergency management courses. J Homel Secur Emerg Manag 6(1):1–25
Klemmer ET, Snyder FW (2006) Measurement of time spent communicating. J Commun 22(2):142–158. https://doi.org/10.1111/j.1460-2466.1972.tb00141.x
Knight R, Nurse JRC (2020) A framework for effective corporate communication after cyber security incidents. Comput Secur J 99. https://doi.org/10.1016/j.cose.2020.102036 . Available via https://www.sciencedirect.com/science/article/pii/S0167404820303096 . Accessed 10 Dec 2021
Kurfiss J (1988) Critical thinking theory, research, practice and possibilities. ASHE-ERIC higher education report, no 2. Association for Study for Higher Education, Washington, DC. Available via https://eric.ed.gov/?id=ED304041 . Accessed 10 Dec 2021
Lai ER (2011) Critical thinking: a literature review . Available via Pearson http://images.pearsonassessments.com/images/tmrs/CriticalThinkingReviewFINAL.pdf . Accessed 10 Dec 2021
Landry T (2017) Embracing the devil: an analysis of the formal adoption of red teaming in the security planning for major events. Naval Postgraduate School, Monterey, California. Available via https://www.hsaj.org/articles/13948 . Accessed 10 Dec 2021
Matherly C (2013) The red teaming essential. Social psychology premier for adversarial based alternative analysis. American Military University, Charles Town. Available at: https://www.researchgate.net/publication/299135949_The_Red_Teaming_Essential_Social_Psychology_Premier_for_Adversarial_Based_Alternative_Analysis . Accessed 10 Dec 2021
Mousena E, Raptis N (2020) Beyond teaching: school climate and communication in the educational context. Intechopen Book Series. https://doi.org/10.5772/intechopen.93575 . Available via https://www.intechopen.com/chapters/73237 . Accessed 10 Dec 2021
National Council for Excellence in Critical Thinking Instruction (2021) Available via https://www.criticalthinking.org/pages/critical-thinking-where-to-begin/796 . Accessed 10 Dec 2021
Patry J (1996) Critical thinking handbook. Foundation for Critical Thinking, Rohnert Park
Paul R, Elder L (2000) Critical thinking handbook: basic theory and instructional structures. Available via http://www.criticalthinking.org.resources/articles/therole-of-questions.html . Accessed 10 Dec 2021
Paul R, Elder L (2005) The miniature guide to critical thinking: concepts and tools. The Foundation for Critical Thinking. Available via https://www.criticalthinking.org/files/Concepts_Tools.pdf . Accessed 10 Dec 2021
Ragazzi F (2016) The Paris attacks: magical thinking & hijacking trust. Crit Stud Secur 4(2):225–228. https://doi.org/10.1080/21624887.2016.1216051
Ramsay JD, Tanali Irmak R (2018) Development of competency-based education standards for homeland security academic programs. J Homel Secur Emerg Manag 15(3):1–27
Retz K (2020) The professional skills handbook for engineers and technical professionals. CRC Press, Boca Raton. https://doi.org/10.1201/9780367853099
Book Google Scholar
Safi A, Burell D (2007) Developing critical thinking leadership skills in homeland security professionals, law enforcement agents and intelligence analysts. Homel Defense J. Available via https://www.ojp.gov/ncjrs/virtual-library/abstracts/developing-critical-thinking-leadership-skills-homeland-security . Accessed 10 Dec 2021
Saltzman B (2021) Critical thinking for more effective communication: fueling your communication engine with critical thinking. LinkedIn Learning. Available via https://www.linkedin.com/learning/critical-thinking-for-more-effective-communication/fueling-your-communication-engine-with-critical-thinking?autoAdvance=true&autoSkip=false&autoplay=true&resume=false&u=26194554 . Accessed 10 Dec 2021
Stansberry S, Haulmark M, Sheeran L (2003) “I agree” does not constitute discussion: applying theoretical frameworks to assess student learning in asynchronous online discussions. Natl Soc Sci J 20(1) Available via: http://www.nssa.us/nssajrnl/20_1/html/stansberry_I_agree_pub_format.htm . Accessed 10 Dec 2021
Stauffer B (2020) What are the 4 C’s of 21st century skills? Applied Educational Systems. Available via https://www.aeseducation.com/blog/four-cs-21st-century-skills . Accessed 10 Dec 2021
Taylor TZ, Prescott R, Harrup K (2021) Developing critical thinking skills among transportation security officers (TSOs) through sharing tacit knowledge. J Transport Secur 14:107–118. Available via https://doi-org.ezproxy.libproxy.db.erau.edu/10.1007/s12198-021-00231-9 . Accessed 10 Dec 2021
The Center for Homeland Defense and Security's University and Agency Partnership Program (CHDS) (2020). UAPP programs and resources. Available via https://www.uapi.us/programs/2077 . Accessed 10 Dec 2021
Thonney T, Montgomery JC (2019) Defining critical thinking across disciplines: an analysis of community college faculty perspectives. Coll Teach 67(3):169–176. https://doi.org/10.1080/87567555.2019.1579700
Tutorialspoint (2016) Effective communication. Available via https://www.tutorialspoint.com/effective_communication/effective_communication_tutorial.pdf . Accessed 10 Dec 2021
United Kingdom Ministry of Defence (MOD) (2021) Red teaming guide, 3rd edn Available via https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/1027158/20210625-Red_Teaming_Handbook.pdf . Accessed 10 Dec 2021
United States Government US Army (2016) Command red team, joint doctrine note JDN 1–16 command red team 16. Available via https://irp.fas.org/doddir/dod/jdn1_16.pdf . Accessed 10 Dec 2021
United States. Federal Emergency Management Agency (FEMA) (2021) IS-242.C: effective communication instructor guide. Available via https://training.fema.gov/is/courseoverview.aspx?code=IS-242.c . Accessed 10 Dec 2021
University of Foreign Military and Cultural Studies (2018) The Red Team Handbook (Applied Critical Thinking Handbook). ver. 9.0. UFMCS, Fort Leavenworth. Available via https://usacac.army.mil/sites/default/files/documents/ufmcs/The_Red_Team_Handbook.pdf . Accessed 10 Dec 2021
World Economic Forum (2020) The future of jobs report 2020. Available via https://www.weforum.org/reports/the-future-of-jobs-report-2020/in-full/infographics-e4e69e4de7 . Accessed 10 Dec 2021
Zenko M (2015) Red team: how to succeed by thinking like the enemy. Basic Books, New York
Download references
Author information
Authors and affiliations.
Department of Security and Emergency Services, Embry-Riddle Aeronautical University – Worldwide, Daytona Beach, FL, USA
Cihan Aydiner
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Cihan Aydiner .
Editor information
Editors and affiliations.
College of Public Health, University of South Florida, Tampa, FL, USA
Anthony J. Masys
Section Editor information
The Pennsylvania State University (Penn State), Penn State Harrisburg, School of Public Affairs, Middletown, PA, USA
Alexander Siedschlag
Rights and permissions
Reprints and permissions
Copyright information
© 2022 Springer Nature Switzerland AG
About this entry
Cite this entry.
Aydiner, C. (2022). Critical Thinking and Effective Communication in Security Domains. In: Masys, A.J. (eds) Handbook of Security Science. Springer, Cham. https://doi.org/10.1007/978-3-319-51761-2_2-1
Download citation
DOI : https://doi.org/10.1007/978-3-319-51761-2_2-1
Received : 11 December 2021
Accepted : 18 December 2021
Published : 21 January 2022
Publisher Name : Springer, Cham
Print ISBN : 978-3-319-51761-2
Online ISBN : 978-3-319-51761-2
eBook Packages : Springer Reference Physics and Astronomy Reference Module Physical and Materials Science Reference Module Chemistry, Materials and Physics
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- Active Directory Attack
- Network Attack
- Mitre Att&ck
- E-Mail Attack
CVE-2023-21554 – Hunt For MSMQ QueueJumper In The Environment
Os credential dumping- lsass memory vs windows logs, credential dumping using windows network providers – how to respond, the flow of event telemetry blocking – detection & response, uefi persistence via wpbbin – detection & response, what is session hijacking/cookie hijacking – demo, linux event logs and its record types – detect & respond, how businesses can minimize network downtime, recovering sap data breaches caused by ransomware, how does dga malware operate and how to detect in a…, how to optimize business it infrastructure, how businesses can identify and address cybersecurity lapses , cybersecurity management 101: balancing risk management with compliance requirements, remote desktop gateway – what is it, how to detect malware c2 with dns status codes, how brazilian students use ai, tools online casinos use to protect players, vdr — a space for efficient and secure transactions, how encryption plays a vital role in safeguarding against digital threats, push notification protocols: ensuring safety in digital communication, phishing scam alert: fraudulent emails requesting to clear email storage space…, vidar infostealer malware returns with new ttps – detection & response, new whiskerspy backdoor via watering hole attack -detection & response, redline stealer returns with new ttps – detection & response, understanding microsoft defender threat intelligence (defender ti), threat hunting playbooks for mitre tactics, masquerade attack part 2 – suspicious services and file names, masquerade attack – everything you need to know in 2022, mitre d3fend knowledge guides to design better cyber defenses, mapping mitre att&ck with window event log ids, how email encryption protects your privacy, how to check malicious phishing links, emotet malware with microsoft onenote- how to block emails based on…, how dmarc is used to reduce spoofed emails , hackers use new static expressway phishing technique on lucidchart.
- Editors Pick
Beyond Technical Skills: How Cybersecurity Courses Enhance Critical Thinking and Problem-Solving

In today’s hyper-connected world, cybersecurity is paramount. As the digital sector continues to expand, the demand for proficient cybersecurity professionals has never been greater. Traditionally, the focus in cybersecurity education has been on imparting technical skills to combat cyber threats. While technical proficiency is undeniably crucial, the rapidly evolving threat landscape necessitates a shift towards a more holistic approach.
This article explores the pivotal role of critical thinking and problem-solving in cybersecurity education, emphasizing their significance beyond technical skills.
The Role of Technical Skills in Cybersecurity
- Technical Skills as the Foundation: Technical skills form the cornerstone of cybersecurity knowledge. Proficiency gained through the cybersecurity course in network security, encryption, firewall configuration, and malware analysis is essential for effectively safeguarding digital assets. Without these technical competencies, cybersecurity professionals would be ill-equipped to defend against cyber threats.
- Essential Technical Competencies: Cybersecurity education traditionally emphasizes the mastery of essential technical competencies. These skills enable professionals to understand and mitigate specific threats and vulnerabilities effectively. However, relying solely on technical expertise has its limitations.
- Limitations of a Solely Technical Approach: The cybersecurity landscape is constantly evolving, with attackers adopting new tactics and techniques. Relying solely on technical skills may not be sufficient to adapt to these ever-changing threats. A more comprehensive approach that includes critical thinking and problem-solving is required.
The Expanding Scope of Cybersecurity Threats
- Evolving Nature of Cyber Threats: Cyber threats are dynamic and increasingly sophisticated. Attack vectors have diversified, encompassing not only malware and viruses but also social engineering, phishing attacks, and advanced persistent threats (APTs). The landscape is in a state of constant flux, requiring cybersecurity professionals to remain adaptable.
- Sophisticated Attack Vectors and Tactics: Attackers are using more sophisticated tactics, often employing zero-day vulnerabilities and advanced evasion techniques. These tactics challenge the efficacy of purely technical solutions. Cybersecurity experts must be able to think critically to identify and address emerging threats effectively.
- Adaptation to New Challenges: As the digital environment evolves, so do the challenges faced by cybersecurity professionals. To stay ahead of attackers, professionals need to cultivate critical thinking and problem-solving abilities that extend beyond their technical toolkit.
The Importance of Critical Thinking in Cybersecurity
- Definition and Significance of Critical Thinking: Critical thinking is the capability to analyze, evaluate, and synthesize information to make informed decisions. In cybersecurity, it involves the capacity to assess complex situations, identify potential threats, and develop proactive strategies.
- Role of Critical Thinking in Problem Identification: Critical thinking plays a pivotal role in identifying and assessing problems in cybersecurity. It allows professionals to recognize anomalies, vulnerabilities, and potential threats that might go unnoticed by relying solely on technical tools.
- Analyzing Complex Cyber Threats: Cyber threats are often multifaceted and elusive. Critical thinking enables professionals to analyze these threats from multiple angles, helping them to comprehend the broader context and anticipate adversary tactics.
Problem-Solving in Cybersecurity
- The Problem-Solving Process in Cybersecurity: Problem-solving is a structured approach to addressing cybersecurity challenges. It involves defining the problem, generating potential solutions, evaluating those solutions, and implementing the most effective one. Problem-solving is essential for mitigating threats and vulnerabilities effectively.
- Developing Effective Strategies: Cybersecurity professionals must develop effective strategies to counter threats. This includes not only identifying vulnerabilities but also devising comprehensive plans to remediate them. Problem-solving skills are instrumental in crafting and implementing these strategies.
- Real-World Problem-Solving Scenarios: The real world of cybersecurity is rife with complex problems. Professionals often encounter scenarios where critical thinking and problem-solving are required to assess risks, respond to incidents, and protect systems and data effectively.
The Integration of Critical Thinking and Problem-Solving in Cybersecurity Courses
- Incorporating Critical Thinking Exercises and Case Studies: Cybersecurity courses can integrate critical thinking exercises and case studies into their curriculum. These exercises challenge students to apply their analytical skills to real-world scenarios, fostering a deeper understanding of cybersecurity challenges.
- Hands-on Problem-Solving Challenges in Cybersecurity Labs: Practical labs and hands-on challenges provide students with opportunities to apply problem-solving skills. These exercises simulate real threats and incidents, allowing students to develop strategies to mitigate them.
- Thinking Like Attackers to Anticipate Threats: An effective cybersecurity approach involves thinking like an attacker. By analyzing systems and applications from an adversary’s perspective, professionals can better anticipate potential vulnerabilities and preemptively address them.
Benefits of Emphasizing Critical Thinking and Problem-Solving
- Enhanced Adaptability: Critical thinking and problem-solving skills enhance professionals’ adaptability to new and evolving threats. They can quickly assess and respond to emerging challenges, reducing the impact of cyber incidents.
- Improved Decision-Making Under Pressure: In high-pressure situations, such as cyberattacks, professionals with strong critical thinking and problem-solving abilities make better decisions. They can prioritize actions effectively and minimize damage.
- Holistic and Proactive Cybersecurity: A holistic approach to cybersecurity that includes critical thinking and problem-solving goes beyond merely reacting to threats. It enables professionals to proactively identify vulnerabilities and weaknesses, reducing the overall risk landscape.
Case Studies: Success Stories of Critical Thinkers in Cybersecurity
Real-Life Examples of Cybersecurity Professionals: Examining real-life success stories of cybersecurity professionals who excelled due to their critical thinking and problem-solving skills demonstrates the practical application of these abilities. These professionals have demonstrated how these skills can make a difference in the cybersecurity field.
Challenges and Considerations in Incorporating Critical Thinking
- Resistance to Change in Cybersecurity Education: Incorporating critical thinking and problem-solving into cybersecurity education may face resistance, as the field has traditionally emphasized technical skills. Overcoming this resistance requires recognition of the changing threat landscape and the importance of holistic skills.
- Balancing Technical and Non-Technical Skills: Finding the right balance between technical and non-technical skills in the curriculum can be challenging. Cybersecurity education must evolve to ensure that students develop both sets of skills effectively.
- Evaluating and Assessing Critical Thinking and Problem-Solving Abilities: Assessing critical thinking and problem-solving skills can be challenging. Developing effective evaluation methods and metrics is essential to measure these skills accurately.
Preparing the Next Generation of Cybersecurity Professionals
- The Evolving Role of Educators and Institutions: Educators and institutions play a crucial role in preparing the next generation of cybersecurity professionals. They must adapt their curricula to emphasize critical thinking and problem-solving while continuing to provide technical foundations.
- Fostering a Culture of Continuous Learning and Critical Thinking: The cybersecurity industry must foster a culture of continuous learning and critical thinking. Professionals should be encouraged to develop these skills through cybersecurity coursesthroughout their careers to remain effective in addressing new threats.
- The Future of Cybersecurity Education and Its Impact on the Industry: As the threat landscape continues to evolve, cybersecurity education will play a pivotal role in shaping the industry’s future. A focus on critical thinking and problem-solving will be vital to building a workforce capable of defending against emerging cyber threats.
In the ever-changing digital landscape, cybersecurity professionals face an array of complex challenges. While technical skills remain essential, the importance of critical thinking and problem-solving cannot be overstated. Emphasizing these skills in cybersecurity education equips professionals to adapt to evolving threats, make effective decisions under pressure, and develop proactive cybersecurity strategies . As the role of cybersecurity professionals continues to evolve, cultivating these non-technical skills will be crucial for securing the digital world effectively and safeguarding our interconnected society.
LEAVE A REPLY Cancel reply
Save my name, email, and website in this browser for the next time I comment.
- Privacy Policy
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

“Thinking About Thinking” is Critical to Cybersecurity
Most cybersecurity vulnerabilities are created by human decisions—many of which aren’t made consciously. here’s why understanding the mental shortcuts we use in decision-making can help strengthen cybersecurity..

Humans make a lot of decisions each day, whether we are aware of them or not. Research shows that people make approximately 200 decisions about food every single day 1 . And, depending on how we define the word “decision,” the daily number can creep into the tens of thousands. Although we may believe our decisions are rational, cognitive scientists argue that we are far less objective than we think. Cognitive biases shape our cybersecurity decisions from the keyboard to the boardroom, and these decisions ultimately determine the effectiveness of our cybersecurity solutions.
Seeing isn’t always believing
Consider the following question: 2
Jack is looking at Anne, but Anne is looking at George. Jack is married, but George is not. Is a married person looking at an unmarried person?
- Cannot be determined
Up to 80% of respondents select “C.” But the correct answer is actually “A.”
It doesn’t matter whether Anne is married or not. If she is married, she is looking at an unmarried person: George. If she is not married, then Jack is looking at an unmarried person: Anne. The reason people often choose “C” is that Anne’s marital status is not provided in the question. In this example, people use a mental shortcut to link Anne’s missing information and “cannot be determined” rather than thinking through multiple options.
Taking mental shortcuts is not limited to tricky logic questions. We use shortcuts so frequently and effortlessly that we do not even realize we’re doing it. However, humans are also capable of engaging in complex analytic thoughts and solving extraordinarily difficult problems.
The Dual Process Theory explains human thought by separating it into two modes: 3
- System 1 is aligned with human intuition. It is characterized by fast, effortless, and emotional thoughts that we unconsciously link with past experiences, thoughts, and patterns.
- System 2 is aligned with analytical and logical thought. It is characterized by effortful thinking and reasoning that we are typically aware of.
Whether we like (or realize) it or not, we spend the vast majority of our lives immersed in System 1 thinking. Our brains use System 1 to optimize the body’s energy—20% of which is going toward brain function. System 1 makes it possible to quickly and effortlessly complete the many simple tasks we engage in throughout the day, such as tying shoes, locating sounds, or avoiding potholes while driving. If we had to depend completely on System 2 and engage in effortful, exact thinking for every decision we faced throughout a day, we might never make it out the front door in the morning.
Although System 1 allows us to function and conserve valuable brainpower, it also creates problems. Our automatic thoughts frequently influence decisions without our awareness—decisions that would be far better suited for a full System 2 analysis. These subconscious influences, or cognitive biases, are systematic departures from logic where rules of thumb supersede the facts at hand.
Decide to do cybersecurity better
Our daily cybersecurity decisions are influenced by our cognitive biases, and while we won’t ever completely escape bias, we can prepare ourselves to make better decisions by thinking about thinking . When we think about thinking, we build awareness of cognitive bias across our organizations, so we can better identify situations where critical decisions and the behaviors they drive are susceptible to increased risk.
Scaling your security strategy to protect remote workers means understanding how workers behave in a remote environment. And Forcepoint is here to help. Visit us to learn more about how risk-adaptive cybersecurity driven by behavioral analytics can secure people and data everywhere.
- Wasink, B. & Sobal, J. (2007). Mindless Eating: The 200 Daily Food Decisions We Overlook. Environment & Behavior, 39, 106-123
- Hector Levasque, as cited by Keith Stanovich, “ Rational and Irrational Thought: The Thinking that IQ Tests Miss ”
- Daniel Kahneman, “ Dual Processing Theory, Heuristics, and Bias”
Related content
Inside-out security: the path to dynamic data protection, building a data protection strategy for remote work, securing innovation in the cloud: best practices for remote development teams, 5 ways to secure data on video conferencing platforms in a remote work environment, from our editors straight to your inbox, show me more, newly patched ivanti csa flaw under active exploitation.

New cryptomining campaign infects WebLogic servers with Hadooken malware

Fortinet confirms breach that likely leaked 440GB of customer data

CSO Executive Sessions: Guardians of the Games - How to keep the Olympics and other major events cyber safe

CSO Executive Session India with Dr Susil Kumar Meher, Head Health IT, AIIMS (New Delhi)

CSO Executive Session India with Charanjit Bhatia, Head of Cybersecurity, COE, Bata Brands

CSO Executive Sessions: DocDoc’s Rubaiyyaat Aakbar on security technology

CSO Executive Sessions: Hong Kong Baptist University’s Allan Wong on security leadership

CSO Executive Sessions: EDOTCO’s Mohammad Firdaus Juhari on safeguarding critical infrastructure in the telecommunications industry

Sponsored Links
- OpenText Financial Services Summit 2024 in New York City!
- Visibility, monitoring, analytics. See Cisco SD-WAN in a live demo.

Security Outside the Box: The Importance of Critical Thinking
Growing up in Nairobi, Kenya, Daniel Mugambi describes his childhood as being “always around computers.” His relationship to them was different than most of ours: instead of spending his hours glued to the screen, he was fascinated by what happened inside the machines. “I would take them apart and try put them back together,” he remembers. Those around him know Mugambi as intensely curious, a trait that goes hand in hand with his ability to think deeply and critically. The same impulses that drove him to understand the inner workings of computers are what make him an excellent future cyber professional. In his own words, “Cybersecurity professionals dedicate their lives to the protection of other’s livelihood and privacy—it’s an honorable duty.”
In the fight against cyber-crime, knowing the laws of cybersecurity isn’t enough. In fact, often laws are nonexistent (at least in the way we think of scientific laws) because the field evolves too quickly for their development. The types of cyber professionals who make it in this ever-evolving field aren’t the students who memorize and are good test takers. “Companies are compromised because hackers are able to think outside the box,” says Mugambi. “They find that one small opportunity and suddenly hold the keys to the kingdom” Hackers succeed because, in thinking outside the box, they find something that hasn’t been thought of before and are able to gain control of entire networks. Likewise, the cyber professionals who succeed are the ones who can think critically—the ones who jump outside the box with hackers and critically examine the situation to find a solution. As a student assistant at Carolina Cyber Center (C3), Daniel Mugambi is one such individual.
As he studies to become a Penetration Tester, Mugambi uses his ability to think critically and operate outside the box to go on the offensive. He explains his field of interest (Penetration Testing) as being able to “measure an organization’s security by hacking into their system. By mimicking a real attacker’s method, we see if the organization’s defenses are up.” Instead of passively allowing attacks to occur, Mugambi creates crisis within a safe context, demonstrating the necessity of critical thinking in the field of cybersecurity. “In cybersecurity, critical thinking is the difference being ten steps ahead of black-hat hackers (the bad guys), or getting hacked—it’s a requirement if we are going to outsmart malicious attacks.” If thinking outside the box is what gives hackers a foothold in our organizations, then we must do more than think originally: we must think critically.
In a country that is “pervasively ill-prepared” (read what Adam Bricker, Executive Director of the Carolina Cyber Center has to say about the Colonial Pipeline attack here ) to protect its critical infrastructure, we need more individuals like Daniel Mugambi. Starting on July 12th, the Carolina Cyber Center begins its Cyber Defense Analyst 6-month cohort for students age 17-21. If you are a critical thinker who believes in protecting our country’s infrastructure, this is for you. Apply before the application deadline to begin your cybersecurity journey and join Daniel Mugambi in protecting our data.
At Carolina Cyber Center, we seek to create cyber professionals of character—individuals with Critical Thinking, Grit, Discipline, Curiosity and Collaboration—whether they begin as an amateur fresh out of high school, mid-life career changers, or are cyber professionals continuing their education. To learn more about what the Carolina Cyber Center offers, visit our website or call us at 828.419.0737.

Carolina Cyber Center of Montreat College
310 Gaither Circle P.O. Box 1267 Montreat, NC 28757
(828) 419-0737
Get Started
No-risk, 30-day money-back guarantee. All instructional materials, labs, certification fees*, books, and range time are included.
Ready to Apply
*First attempt for certification included. The cost for additional certification attempts is the responsibility of the student.

Mastering Essential Soft Skills for Cybersecurity Professionals: A Guide to Implementing the CISO's Strategy
The Soft Side of Cyber Podcast
We launched our first podcast episode on youtube, itunes, spotify, and google play. subscribe and give it a listen today.
Technical expertise is super important in our field. But here's the thing: soft skills are just as crucial when it comes to effectively implementing the boss's strategy. Of course, you might be a whiz at identifying vulnerabilities and responding to threats. Still, without soft skills, you may be unable to maximize your impact on the team, move the needle, and help keep your organization safe.
That's where the Soft Side of Cyber Framework comes in. Our handy guide breaks down the critical soft skills you need to thrive in cybersecurity. In this article, we will explore how you can align your skillset with the framework and make a difference in implementing the CISO's strategy.
Time Management
In the fast-paced world of cybersecurity, effective time management and prioritization are critical to ensuring the most pressing threats and vulnerabilities are addressed promptly. Not to mention, there's always more to do, more demands, and another "critical" thing to deal with. By balancing competing priorities and deadlines, you can maximize your productivity and limited resources.
Effective time management strategies, like setting clear goals, breaking tasks into manageable chunks, and eliminating distractions, can help you stay focused and organized. Time or day blocking, where you schedule out chunks of time to focus intensely on a particular thing, is also a powerful technique for getting things done.
By sharpening your time management and personal organization skills, you'll contribute more effectively to implementing the CISO's strategy and help your organization stay one step ahead of potential threats.
Managing your time and being more efficient is one thing, but you must spend that time on the right things. That's where critical thinking can help.
Critical Thinking
Critical thinking is a must-have skill for cybersecurity professionals. It enables you to analyze complex situations, identify potential vulnerabilities, and make well-informed decisions to protect your organization. By honing your critical thinking skills, you'll become a more effective problem solver and contribute to successfully implementing the CISO's strategy.
To sharpen your critical thinking abilities, practice breaking down complex issues into manageable components, question assumptions, and consider multiple perspectives when evaluating potential solutions. Additionally, consciously self-reflect and seek feedback to continuously improve your decision-making process.
Circling back and evaluating your decisions after a certain time to determine if your original assessment was correct and why or why not can help you improve. That process will help you make necessary changes, leading to adaptability.
Adaptability
Adaptability is essential with the amount of change we deal with in this field.
Cybersecurity professionals must be able to quickly adjust their tactics, techniques, and priorities to protect their organization from new risks and vulnerabilities. The latest CVE or zero-day drops, you have to change. Senior leadership has a change of heart about something, and you might need to change. The driver for a change can come from anywhere.
Being adaptable means staying informed about the latest developments and being ready to pivot your approach as needed. This agility allows you to address evolving security challenges and align your efforts with the CISO's strategic objectives.
To enhance your adaptability, embrace a continuous learning mindset and seek opportunities to expand your knowledge and skill set. Stay up-to-date with industry news, attend conferences, and participate in professional training and certification programs. Doing so will prepare you to adjust your strategies and tactics in response to the ever-changing cybersecurity landscape.
Creativity is essential for developing innovative solutions to the dynamic set of problems we face in the field of cybersecurity and keeping pace with evolving threats. Embracing creativity enables you to think outside the box, explore new approaches, and devise unique strategies that align with the CISO's vision and objectives. It's easy to slip into a mindset or cultural trope about not being creative because we work in a technical field, but you have to work against that.
By fostering a creative mindset, you can tap into fresh ideas and perspectives to help your organization stay one step ahead of the risks it faces. Encourage a culture that values creative thinking and supports exploring unconventional ideas. Try things that might fail. This environment will empower your team to challenge assumptions, explore new techniques, and develop more effective cybersecurity strategies per the CISO's plan.
As you implement the CISO's strategy, use your creativity to identify potential gaps in your organization's security posture, develop tailored solutions to address these vulnerabilities, and communicate the value of innovative security initiatives to stakeholders. By leveraging your creative problem-solving skills, you can contribute to a more robust and effective cybersecurity program that aligns with the CISO's vision and bolsters your organization's defenses.
Communication
Communication is essential in almost any field, and cybersecurity is no exception. For us, explaining complex concepts to different audiences is crucial. Therefore, you must adjust your communication style to suit technical and non-technical folks. By keeping it simple, clear, and jargon-free, you'll help others understand the importance of your work and its impact on the organization.
Active listening and empathy are also vital ingredients in effective communication. You build trust and rapport when you actively engage with your audience and show genuine interest in their concerns. Plus, it'll help you spot and address potential security risks more efficiently.
To improve your communication skills, consider joining training programs and workshops or seeking mentorship from experienced professionals. Practice makes perfect, so don't forget to put your communication skills to the test in various settings like team meetings, presentations, and written reports.
Catching up on last week? Check out this reaction video on effective writing skills in cyber .
In the wild world of cybersecurity, threats are constantly evolving and getting trickier. That's why no one person can tackle every challenge alone. Collaboration and teamwork are the secrets to creating effective defense strategies and addressing vulnerabilities. As cybersecurity professionals, we need to work together within our team and across different departments to share knowledge and develop comprehensive solutions.
As you strive to put the CISO's strategy into action, building strong working relationships within your team and across different departments is essential. By fostering a culture of open communication, trust, and collaboration, you can create a united front against cyber threats and ensure that your organization's security measures align with the CISO's vision.
By prioritizing teamwork and collaboration, you'll be better equipped to navigate the complexities of the cybersecurity field, address emerging threats, and effectively contribute to successfully implementing the CISO's strategy.
Leadership isn't just for the top dogs; it's a critical soft skill for all cybersecurity professionals, no matter where they stand in the organization. By showing off your leadership qualities, you'll inspire trust, confidence, and respect among your colleagues and stakeholders, ultimately contributing to a more effective cybersecurity strategy.
Developing a reputation for expertise and reliability is essential to establishing credibility. By consistently delivering high-quality work and showing your commitment to excellence, you'll position yourself as your organization's trusted and valued member.
Don't forget to learn and develop professionally to cultivate your leadership skills continuously. Sit for certifications, attend conferences, and seek opportunities to learn from industry leaders. In addition, you can better guide your organization's cybersecurity efforts by staying current with the latest trends and best practices.
In cybersecurity, persuading decision-makers and stakeholders to invest in and prioritize security efforts is critical to successfully implementing your strategy. To do this effectively, you'll need to hone your persuasion skills, enabling you to convey the importance and value of cybersecurity initiatives compellingly.
By crafting engaging narratives and presenting data-driven arguments, you'll be able to showcase the need for investment in cybersecurity programs and infrastructure that aligns with the CISO's vision. Plus, you'll be able to influence others to adopt a proactive approach to security, ultimately creating a more secure organization that successfully executes the CISO's plan.
By refining your persuasion skills and using them to advocate for the CISO's strategy, you'll help secure the necessary resources, support, and buy-in to create a more resilient and secure organization.
Closing Thoughts
Soft skills are essential for cybersecurity staff like you. By honing these skills, you'll be way more effective at implementing the CISO's strategy and contributing to your organization's security and success. The Soft Side of Cyber Framework is your go-to guide for leveling up your personal and professional growth in the cybersecurity field.
Just think about the impact you can have by improving your soft skills. Not only will you boost your career prospects, but you'll also play a huge role in strengthening your organization's security posture. So, embrace that ongoing commitment to personal and professional growth in cybersecurity, and become the driving force for positive change your organization needs!
Join the newsletter to receive the latest updates in your inbox.
You might also like, customer-centric cybersecurity: a service excellence guide.
Business enablement, customer service, and empowering the end user are all terms or phrases we throw around in cybersecurity. Today, we are thrilled to dive deeper into the art of providing exceptional customer service in our ever-evolving cyber landscape. Customer service is talked about in almost every industry, from grocery
Bridging the Gap: A CISO's Guide to Supporting Sales and Marketing with Cybersecurity
Leading a cybersecurity organization is hard. You're not just responsible for security matters, despite what you were told in your interviews. You're expected to help enable the business, support sales and marketing efforts, be a good public representative, be a key component of any digital transformation

- New Zealand
- United States
- United Kingdom
Sharpening Your Critical Thinking Skills: Approaches and Exercises for Cyber Security Experts

Stay Informed With Our Weekly Newsletter
Receive crucial updates on the ever-evolving landscape of technology and innovation.
By clicking 'Sign Up', I acknowledge that my information will be used in accordance with the Institute of Data's Privacy Policy .
Cyber security has become an essential concern for individuals and organisations in today’s rapidly evolving digital landscape.
Critical thinking skills are crucial for cyber security experts as they face increasingly complex challenges and ever-changing threats.
Critical thinking skills in cyber security

Critical thinking is not just an optional skill—it is a necessity when it comes to cyber security.
As cyber attacks become more sophisticated and frequent , professionals in this field must be able to think critically in the face of uncertainty, ambiguity, and complexity.
Critical thinking enables cyber security experts to assess risks, evaluate evidence, and make informed decisions that protect individuals and organisations from potential threats .
The role of critical thinking in cyber security
Critical thinking plays a fundamental role in cyber security by enabling professionals to approach problems and scenarios systematically and analytically.
By applying critical thinking, experts can identify system vulnerabilities, evaluate the effectiveness of security measures, and devise strategies to mitigate risks.
Moreover, critical thinking allows for identifying patterns, connections, and potential threats that may go unnoticed by others.
How critical thinking enhances your cyber security skills
Developing critical thinking skills enhances cyber security professionals’ overall effectiveness and efficiency.
By cultivating critical thinking, experts can improve their problem-solving abilities, identify logical fallacies, and distinguish between relevant and irrelevant information.
Additionally, critical thinking enables professionals to think creatively, finding innovative solutions to emerging cyber threats.
Furthermore, critical thinking in cyber security involves anticipating and adapting to rapidly evolving technological advancements.
Cyber security professionals must stay ahead of the curve as technology advances at an unprecedented pace.
By critically evaluating emerging technologies, experts can assess their potential risks and vulnerabilities, enabling them to develop proactive strategies to safeguard against future threats.
Additionally, critical thinking in cyber security extends beyond technical expertise.
It also encompasses the ability to understand cyber criminals’ motivations and tactics.
Professionals can anticipate their next move and develop effective countermeasures by critically analysing their methods and strategies.
This holistic approach to critical thinking ensures that cyber security professionals are well-equipped to tackle the ever-evolving landscape of cyber threats.
Developing critical thinking
Achieving proficiency in critical thinking requires a combination of self-awareness and active practice.
By understanding the key components of critical thinking and employing effective strategies, cyber security experts can elevate their analytical abilities to the next level.
Developing critical thinking is a journey that involves continuous learning and growth.
It is about acquiring knowledge and honing the ability to think critically and make informed decisions in the ever-evolving cyber security landscape.
Embracing a mindset of intellectual curiosity and a willingness to challenge assumptions is vital to fostering a solid foundation in critical thinking.
The key components of critical thinking
At its core, critical thinking involves the skills of analysis, evaluation, and synthesis.
Cyber security professionals must be able to analyse complex situations, evaluate evidence and arguments, and synthesise information to form logical conclusions.
Additionally, critical thinking encompasses traits such as curiosity, objectivity, and persistence, which are essential for effective problem-solving.
Analytical thinking is crucial in cyber security, where professionals dissect intricate systems and identify vulnerabilities.
Evaluation skills are crucial when assessing the credibility of sources and the validity of information, ensuring that decisions are based on sound reasoning.
Synthesising diverse data points and drawing meaningful connections is a hallmark of advanced critical thinking, enabling professionals to devise comprehensive security strategies.
Strategies for improving critical thinking
Improving critical thinking requires intentional effort and practice.
One useful strategy is active questioning, whereby professionals challenge assumptions, evaluate evidence, and explore alternative perspectives.
Another approach is to cultivate a habit of reflection, regularly reviewing past decisions and seeking opportunities to improve.
Furthermore, seeking diverse sources of information and engaging in collaborative discussions can help broaden one’s perspective and enhance critical thinking abilities.
Collaboration significantly enhances critical thinking skills, as it exposes individuals to different viewpoints and methodologies.
Engaging in discussions with peers and experts in the field can help cyber security professionals refine their analytical thinking and learn to approach problems from various angles.
Embracing a culture of continuous improvement and feedback is essential in mastering critical thinking in the dynamic realm of cyber security.
Practical exercises to boost critical thinking

While understanding the theory behind critical thinking is important, practical exercises can significantly enhance one’s thinking ability.
In the field of cyber security, where real-world scenarios demand quick thinking and accurate decision-making, the following exercises can help professionals sharpen their critical thinking.
Brainstorming exercises for better problem-solving
Brainstorming sessions allow cyber security experts to collectively generate ideas, explore potential solutions, and evaluate their viability.
These exercises encourage critical thinking by involving individuals with different perspectives and expertise by fostering a collaborative environment.
Brainstorming exercises stimulate creativity and help professionals consider alternative approaches to cyber security challenges.
Logic puzzles and how they help in cyber security
Logic puzzles are an excellent way to improve critical thinking skills in cyber security.
These puzzles require individuals to think logically, analyse information, and make deductions based on given conditions.
By solving logic puzzles, professionals can enhance their ability to identify patterns, recognise logical fallacies, and apply structured thinking to real-world cyber security scenarios.
Applying critical thinking to cyber security scenarios
The actual value of critical thinking lies in its practical application.
Professionals with strong critical thinking skills can navigate complexities and find effective solutions when faced with cyber security scenarios.
Identifying potential threats through critical thinking
Critical thinking enables professionals to identify potential threats and vulnerabilities others may overlook.
By actively questioning assumptions, analysing system weaknesses, and evaluating behaviour patterns, experts can identify risks and take proactive measures to mitigate them.
Through critical thinking, cyber security professionals can stay one step ahead of cybercriminals, safeguarding individuals and organisations from potential harm.
Using critical thinking for effective cyber security solutions
Effective cyber security solutions require technical expertise and critical thinking abilities.
By applying critical thinking, professionals can assess the effectiveness of existing security measures, illuminate areas for improvement, and devise tailored solutions.
With a critical thinking mindset, cyber security experts can navigate complex systems, consider multiple factors, and make well-informed decisions that enhance overall security.
Maintaining and improving your critical thinking skills

Developing critical thinking skills is ongoing, requiring continuous learning and practice.
To maintain and enhance these skills, cyber security professionals can adopt the following strategies:

Regular practices for honing critical thinking
Consistency is key to honing critical thinking.
Regular practices such as solving puzzles, seeking out challenging problems, and critically evaluating information can help professionals stay sharp and improve their analytical abilities.
Cyber security experts can stay ahead in this ever-evolving field by dedicating time and effort to critical thinking.
The role of continuous learning in critical thinking development
Critical thinking skills are developed through continuous learning.
Staying updated with the latest industry trends, technologies, and best practices expands knowledge and exposes professionals to diverse perspectives and strategies.
Cyber security experts can continuously refine their critical thinking abilities by seeking opportunities to learn and grow and stay at the forefront of their field.
Critical thinking skills are indispensable for professionals in the dynamic and ever-changing cyber security landscape.
Cyber security experts can sharpen their analytical abilities and approach challenges confidently by understanding the importance of critical thinking, adopting effective strategies, and practising practical exercises.
With strong critical thinking, these professionals can protect individuals and organisations from cyber threats and contribute to a more secure digital environment.
Are you considering a career in cyber security?
Whether you are new to tech or a seasoned professional looking for a change, the Institute of Data’s Cyber Security Program offers an in-depth, balanced, hands-on curriculum for IT and non-IT professionals.
To learn more about our 3-month full-time or 6-month part-time remote bootcamps, download the Cyber Security Course Outline .
Want to learn more about our programs? Our local team is ready to give you a free career consultation . Contact us today!

Follow us on social media to stay up to date with the latest tech news
Stay connected with Institute of Data

Iterating Into Artificial Intelligence: Sid’s Path from HR to Data Science & AI

From Curiosity to Cyber Security: Maria Kim’s Path to Protecting the Digital World

Mastering Cyber Security: Ruramai’s Inspiring Journey from Law to Digital Defence

From Passion to Pursuing a New Career: Neil Kripal’s Driven Journey into Software Engineering

© Institute of Data. All rights reserved.
Copy Link to Clipboard
- Corpus ID: 55398599
Critical Thinking Skills and Best Practices for Cyber Security
- Srinivas Nowduri
- Published 2018
- Computer Science, Education
- International Journal of Cyber-Security and Digital Forensics
Tables from this paper

4 Citations
Multi-dimensional cybersecurity education design: a case study, cybersecurity leaders: knowledge driving human capital development, advancing cybersecurity through knowledge conversion: industry-academia interchange in a doctoral program, puzzle-based honors cybersecurity course for critical thinking development, 19 references, a model of critical thinking as an important attribute for success in the 21st century, what is needed to develop critical thinking in schools, critical thinking in the business curriculum, critical thinking framework for any discipline, critical thinking for 21st-century education: a cyber-tooth curriculum, critical thinking in business education, teaching critical awareness in an introductory course., social problems: a critical thinking approach, a taxonomy for learning, teaching, and assessing: a revision of bloom's taxonomy of educational objectives, related papers.
Showing 1 through 3 of 0 Related Papers
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
7 Pressing Cybersecurity Questions Boards Need to Ask
- Keri Pearlson
- Nelson Novaes Neto

Don’t leave concerns about critical vulnerabilities for tomorrow.
Boards have a unique role in helping their organizations manage cybersecurity threats. They do not have day to day management responsibility, but they do have oversight and fiduciary responsibility. Don’t leave any questions about critical vulnerabilities for tomorrow. Asking the smart questions at your next board meeting might just prevent a breach from becoming a total disaster.
In this article we offer 7 questions to ask to make sure your board understands how cybersecurity is being managed by your organization. Simply asking these questions will also raise awareness of the importance of cybersecurity, and the need to prioritize action.
For every new technology that cybersecurity professionals invent, it’s only a matter of time until malicious actors find a way around it. We need new leadership approaches as we move into the next phase of securing our organizations. For Boards of Directors (BODs), this requires developing new ways to carry out their fiduciary responsibility to shareholders, and oversight responsibility for managing business risk. Directors can no longer abdicate oversight of cybersecurity or simply delegate it to operating managers. They must be knowledgeable leaders who prioritize cybersecurity and personally demonstrate their commitment. Many directors know this, but still seek answers on how to proceed.
- KP Keri Pearlson is the executive director of the research consortium Cybersecurity at MIT Sloan (CAMS). Her research investigates organizational, strategic, management, and leadership issues in cybersecurity. Her current focus is on the board’s role in cybersecurity.
- NN Nelson Novaes Neto is a Partner and CTO at C6 Bank. He is also a Research Affiliate at MIT Sloan School of Management.
Partner Center

Top Skills Required to Start Your Career in Cybersecurity
Have you been thinking of a career in cybersecurity? It certainly is a good time to do so. Cybersecurity is one of the fastest-growing career fields, with strong demand from employers and a shortage of qualified employees. There are opportunities in nearly every industry, offering good salaries with long-term job security.
To start a cybersecurity career or transition into the field, you must do a quick self-assessment. The concepts can be learned, but it will help if you already possess some of the skills for cybersecurity. Anyone with an excellent approach to problem-solving and attention to detail already has entry-level cyber security skills. With the right kind of thinking and a solid work ethic, you could already be well on your way to a fast-paced, rewarding career.
Considering a Career in Cybersecurity: Why Choose It?
Considering any career, whether you’re just entering the workforce or looking for a new job, can raise some concerns. You may wonder if it’s the right move or if you should choose something else. However, there’s never been a better time to start your career in cybersecurity. It’s a career with and opportunities in several different roles. For example, information security analyst jobs are predicted to grow by 32% between now and 2032 (U.S. Bureau of Labor Statistics).
Experts expect cybersecurity hiring to remain strong for the foreseeable future (Fortune, 2023). As companies return to normal following the Covid-19 pandemic, the way business is done has changed. Remote work has gone from a unique case for field salespeople and branch offices to something more common. Today, the cloud connects employees globally like no one could have imagined just a few years ago (Grand View Research, 2023). This increased adoption of the cloud has only increased the need for information security professionals.
Essential Skills for Entering Field Cybersecurity
So, what are the essential skills needed for cyber security? At the top of the list are problem-solving skills. Day in and day out, cybersecurity professionals are called to address complex issues in creative ways. New information security threats always emerge, requiring cybersecurity pros to think quickly and apply their existing knowledge. Attention to detail, strong analytical skills, and the ability to evaluate the most minute details go a long way in a cybersecurity career.
As an information security worker, you’ll need excellent communication skills. You’ll work with many different people in a wide range of roles from nearly every department. The ability to clearly explain security issues, their impact, and how to address them is critical. At specific points, you’ll be required to speak in technical language. At others, you’ll need to explain things in ways that your non-technical co-workers can understand.
Your next move should be to look for a certification that not only equips you with the foundational technical aspects of cybersecurity but also provides thorough hands-on practice. The best courses will provide extensive lab time so that you can learn and practice in real-world scenarios while building problem-solving skills.
Capture the Flag style critical thinking challenges help build the technical skills required for cyber security. In addition to labs and the cyber range, Capture the Flag style critical thinking challenges are a great way to hone your analytical thinking skills while gaining technical experience. EC-Council’s Certified Cybersecurity Technician (C|CT) course features all the components needed to learn essential cybersecurity skills .
Embarking on Your Cybersecurity Certification Journey
The C|CT program balances teaching and practical experience. You’ll learn about the critical issues cybersecurity pros are dealing with right now and then see how they play out in EC-Council’s Cyber Range. As the course covers information security and network principles, the Cyber Range allows you to address real-world threats and attacks.
With 85 hands-on labs in the Cyber Range and Capture the Flag style critical thinking challenges, the C|CT course teaches cybersecurity skills in ways other certifications don’t. You’ll learn fundamental concepts like data security controls, cryptography and public key infrastructure, virtualization, cloud computing, and the threats surrounding them. Using the network assessment techniques and tools that the pros use, the C|CT certification gives you the head start you need to stand out from others starting a cybersecurity career.
How Do You Apply for the C|CT Course?
To apply for the Certified Cybersecurity Technician course, you can leverage EC-Council’s C|CT Scholarship for career starters. Through this initiative, EC-Council aims to make the C|CT course more accessible to a broader spectrum of individuals and encourage talent development in cybersecurity. With this partial cybersecurity scholarship , you may access all of the course materials at no cost, with the exception of a minimal fee for technology and proctoring of exams. Learn more about the scholarship here .
The C|CT allows cybersecurity professionals to develop their skills in various cybersecurity roles. This includes cybersecurity support technicians, ethical hackers, network support specialists, and more.
You can apply for EC-Council’s C|CT Scholarship to offset the cost of taking the C|CT course. The scholarship is open to the first 20,000 applicants and awarded on a first-come, first-served basis. Take advantage of the partial scholarship that provides free access to all instructional resources, making the C|CT program an incredibly cost-effective way to kickstart your cybersecurity journey. For additional information about the scholarship, please visit CCT scholarship page.
Lake, S. (2023, January 12). The 3 cybersecurity hiring trends experts predict for 2023. Fortune. https://fortune.com/education/articles/the-3-cybersecurity-hiring-trends-experts-predict-for-2023/
Grand View Research. Cyber Security Market Size, Share & Trends Report, 2023. https://www.grandviewresearch.com/industry-analysis/cyber-security-market
U.S. Bureau of Labor Statistics. Information security analysts. https://www.bls.gov/ooh/computer-and-information-technology/information-security-analysts.htm
About the Author
Leaman Crews is a former newspaper reporter, publisher, and editor with over 25 years of professional writing experience. He is also a former IT director specializing in writing about tech in an enjoyable way.
Share this Article
You may also like

Can I Get an Entry-Level Cybersecurity Certification Without an IT Background?

You Got Sec+ Certification, What’s Next? Build Technical Skills With a C|CT

How C|CT Labs Prepare You to Gain Crucial Technical Skills to Succeed in Cybersecurity
Recent articles.
From Factory Floors to Smart Homes: Threat Intelligence…

From Drowning to Thriving: The Evolution of Vulnerability…

Reassessing Incident Response Strategies in Light of CrowdStrike…

Navigating the Digital Crime Scene: Tools & Techniques…
" * " indicates required fields

- Search Menu
- Sign in through your institution
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Article Contents
Introduction, acknowledgement, conflict of interest statement, author contributions.
- < Previous
The security mindset: characteristics, development, and consequences
The authors wish it to be known that, in their opinion, the first two authors should be regarded as co-first authors.
- Article contents
- Figures & tables
- Supplementary Data
Koen Schoenmakers, Daniel Greene, Sarah Stutterheim, Herbert Lin, Megan J Palmer, The security mindset: characteristics, development, and consequences, Journal of Cybersecurity , Volume 9, Issue 1, 2023, tyad010, https://doi.org/10.1093/cybsec/tyad010
- Permissions Icon Permissions
The world is facing a cybersecurity skills gap as cybercrime and cyberwarfare grow in importance. One often-discussed quality that is potentially relevant to cybersecurity recruitment and education is the so-called “security mindset”: a way of thinking characteristic of some security professionals that they believe to be especially advantageous in their work. Although some employers express a desire to hire people with a security mindset, and initiatives to cultivate the security mindset are being implemented, it has no common definition and little is known about its characteristics, its development, and its consequences. We interviewed 21 cybersecurity professionals who strongly identified as having a security mindset based on a minimal description drawn from existing literature. Thematic analysis of the interview data suggests that the security mindset can be conceptualized as consisting of three interconnected aspects—“monitoring” for potential security anomalies, “investigating” anomalies more deeply to identify security flaws, and “evaluating” the relevance of those flaws in a larger context. These three aspects develop in different ways and have different personal and professional consequences. Participants mostly spoke positively of the security mindset, but they also mentioned several disadvantages not mentioned by existing security-mindset literature, such as mental health pressures, workplace tensions, and negative effects on personal relationships. We discuss the implications of these findings for future study of the security mindset and suggest practical implications for cybersecurity management, education, and recruitment.
“Security requires a particular mindset. Security professionals—at least the good ones—see the world differently. They can’t walk into a store without noticing how they might shoplift. They can’t use a computer without wondering about the security vulnerabilities. They can't vote without trying to figure out how to vote twice. They just can't help it.”
– Bruce Schneier, 2008 [ 1 ].
The globe is facing a shortage of competent cybersecurity professionals, referred to as the cybersecurity “skills gap” [ 2–4 ]. According to a recent estimate, there are ∼2.72 million cybersecurity jobs in demand worldwide [ 5 ]. Meeting the demand for cybersecurity requires breaking down cybersecurity expertise into component skills and qualities that can be clearly identified and cultivated [ 6–10 ].
One often-mentioned quality of some cybersecurity professionals is called the “security mindset”—a certain way of thinking that is seen as advantageous in cybersecurity work and that tends to involve constantly searching for security flaws in nearby systems. Being a security professional is claimed to be neither necessary nor sufficient to have a security mindset [ 1 , 11 ], but industry insiders indicate that they look for a security mindset when recruiting and try to cultivate it among their employees [ 12–14 ]. Several cybersecurity education programs also devote attention to it, and it is included in US cybersecurity curricula [ 6 , 15 , 16 ].
However, despite this interest, the security mindset has not yet been clearly conceptualized [ 11 , 17 , 18 ]. There have been some written case studies of attempts to teach the security mindset, but they have avoided the challenge of precisely conceptualizing and measuring its presence, relying instead on indirect measurements such as code quality or teaching evaluations [ 17 , 19–21 ]. Without conceptual clarity, the security mindset cannot be effectively measured, taught, or linked to existing social science research.
Many other questions about the security mindset also remain empirically underexplored. How does the security mindset develop? Can it be deliberately cultivated, or is it relatively fixed or innate? Does it indeed contribute to improved cybersecurity performance, is it merely correlated with other qualities that drive performance, or is it uncorrelated with performance entirely? Are there any negative personal or social consequences of having a security mindset? In an influential 2008 article in Wired magazine and subsequent blog comments, cybersecurity professional Bruce Schneier posed some of these questions, but little work has been done since then to investigate further [ 1 ].
We view the security mindset as a psychological phenomenon that deserves more careful scrutiny, and we believe that the field of social psychology is well-positioned to provide it. Social psychologists have a successful track record of studying psychological phenomena that are well-known within specialized professional communities. Some examples include mindfulness among meditators, “choking under pressure” among athletes and other top performers, and the sense of belonging in academic settings among students and educators [ 22–24 ]. In each case, psychologists have conducted qualitative research to understand phenomena from the perspectives of the people experiencing them, translated their understanding into quantitative measures, demonstrated links between those measures and valued outcomes, and developed scalable programs for training and improvement [ 25–27 ].
We hope that formal study of the security mindset can both offer theoretical contributions and help to meet global demand for cybersecurity expertise. Following general best-practices in applied social psychology research [ 28 , 29 ], we begin by conducting what, to our knowledge, is the first qualitative study of cybersecurity professionals’ own perspectives on their self-identified security mindsets. We aim to answer the following questions:
How do cybersecurity professionals who self-identify as having a “security mindset” conceptualize its meaning, including its components and characteristics?
How do they believe that the security mindset is developed?
What do they believe are the personal and professional consequences of having a security mindset?
Related work
There is no common definition of the security mindset and there is little agreement about its nature as a psychological construct. For example, the security mindset has been described as a unitary ability or set of abilities [ 17 , 19 , 30 , 31 ], as a character trait or set of traits [ 1 , 32 ], and as a set of attitudes, beliefs, and/or values [ 11 , 18 ]. However, some consistent themes emerge across the literature. We review two central themes below in order to frame our own approach to the topic.
Common features of the security mindset
First, whether it is defined as an ability, trait, belief, value, or habit, most existing discussions of the security mindset emphasize that it involves engaging in an active cognitive process to identify security vulnerabilities. One phrase that is frequently used when describing the security mindset is “thinking like an attacker” [ 1 , 19 , 31–33 ]. It has also been described as “think[ing] about failures and how to trigger them” [ 17 ] and “recognizing how something can be used maliciously or broken” [ 34 ]. Similarly, a set of cybersecurity curricular guidelines created by the Joint Task Force on Cybersecurity Education define “adversarial thinking,” also described as an “adversarial mindset,” as “a thinking process that considers the potential actions of the opposing force working against the desired result” [ 6 ].
Second, most discussion of the security mindset emphasizes that it is proactive and intrinsically motivated, above and beyond the demands of work. For example, Schneier’s original description of the security mindset (and the enthusiastic comment threads that followed) emphasized the idea that some people “just can’t help” constantly looking for security flaws in both work and daily life [ 1 , 32 ]. The security mindset has also been described in emotional terms as “a peculiar mix of curiosity and paranoia that turns life into a perpetual game of asking ‘what if’ questions” [ 13 ]. The emphasis on the motivational aspect of the security mindset is consistent with extensive prior work on the importance of motivation to engage in cybersecurity practices [ 35–39 ].
Related concepts
Culture plays a pervasive role in shaping behavior, and security-related behavior is no exception [ 40 , 41 ]. Organizational culture motivates individuals to engage in cybersecurity practices [ 42–45 ]. For example, organizations that emphasize personal responsibility for writing secure code or that appoint “security champions” appear to influence the coding practices of their employees [ 45–47 ]. It is therefore important to understand if and how cultural factors both in and out of work lead people to adopt a security mindset.
In one of the few empirical studies of the security mindset, Haney et al. examined cultural influences on the security mindset by interviewing individuals working at a company that develops cryptographic products [ 33 ]. They found that participants cultivated a personal commitment to cybersecurity that was heavily influenced by their surrounding “security culture,” which they defined as “a subculture of an organization in which security becomes a natural aspect in the daily activities of every employee.” However, Haney et al. also freely used the term “security mindset” to describe characteristics of both individuals and entire organizations, making it difficult to conceptually separate “security mindset” from “security culture” in their framing. For clarity and consistency with most other work, we use the term “security mindset” to refer to a property of individuals and not groups. We discuss the role of cultural factors further in “Development of the security mindset” and in the discussion.
The security mindset is also related to, but distinct from, several individual-level constructs studied by cybersecurity scholars and social psychologists. One is specialized technical knowledge about systems or general experience in the security field. Several authors and curricular guidelines have proposed that technical knowledge is helpful or perhaps even necessary for a security mindset, but not sufficient [ 1 , 6 , 17 , 19 , 31 ]. Our model of the security mindset is consistent with these claims; as we describe below, the different aspects of the security mindset are not synonymous with technical knowledge. The security mindset is also distinct from security self-efficacy, or the perception of one’s own level of security ability [ 48 ]. While it may contribute to security self-efficacy, the security mindset itself is commonly described as an active process rather than a judgment of one’s own ability.
Finally, the security mindset partially resembles psychological models of threat perception and response that have been used to predict cybersecurity-related behavior, such as protection motivation theory (PMT) and the extended parallel process model (EPPM) [ 35 , 49 , 50 ]. These models are intended to explain the possible responses that people have to threats and fear appeals, such as taking protective action or engaging in coping strategies, based on factors such as the perceived severity of the threat and one’s ability to respond. Unlike PMT and EPPM, the security mindset appears at first glance to be a process of proactively seeking out possible security threats rather than a process of responding to them. However, as we describe below, many of our study participants described an aspect of the security mindset dedicated to evaluating the severity of threats once they are discovered. Thus, careful accounts of the security mindset may inform and integrate smoothly with models of threat perception by describing both how threats are identified and how they are appraised.
Limitations and present work
In summary, most existing literature on the security mindset describes individuals who look for security flaws in systems around them in a proactive, self-motivated fashion. But beyond this, many basic questions remain about the exact nature of the security mindset. For example, little is known about the specific ways of thinking that enable some people to spot security flaws. With the exception of Haney et al. [ 33 ], there is also little discussion of the origins of the security mindset and why it seems to be so motivating to some people and not others. There are no survey measures of the security mindset that could be used to identify and cultivate it, and scholars disagree about whether it can be taught at all [ 1 , 20 , 21 ]. Finally, there is little discussion of the consequences of a security mindset for one’s personal and professional life. For example, the security mindset is claimed to be helpful in cybersecurity roles, but heightened sensitivity to risks and potential attackers could also be a source of personal stress and worry [ 51 , 52 ].
An underlying problem with most of the literature on the security mindset is the lack of empirical data [ 1 , 11 , 13 , 17–19 , 31 , 32 ]. The few articles with empirical data only touch briefly on the topic of the security mindset [ 33 , 34 ] or describe teaching interventions without including the security mindset itself as an outcome measure [ 20 , 21 ].
When the existing literature does not adequately address a phenomenon, interviews with a target population may be used to gain more clarity [ 53 ]. To develop a more empirically grounded understanding of the security mindset while building on previous work, we distilled the common themes described above into a minimal description of the security mindset that matches most current sources on the topic: “the tendency to look for and think about security flaws in the systems around oneself, even when one is not directly instructed to do so.” Because we lacked an existing measure for (or even a precise definition of) this tendency, we instead sought out cybersecurity professionals who self-identified as having a security mindset by this description and then allowed them to elaborate further on the topic in semi-structured interviews. We believe that it was helpful to provide participants with our minimal description because they might have otherwise confused the term “security mindset” with something like a general “knack” for security or security self-efficacy [ 48 ].
Sampling and recruitment
We recruited cybersecurity professionals via purposive and snowball sampling using an email advertisement sent to a cybersecurity reading group email list (Appendix A). (The list is based at Stanford University but includes external affiliate members who are invited at the discretion of current members. It contained ∼120 members as of May 2022.) The outreach email asked for cybersecurity professionals who self-identified as having a security mindset according to the minimal description provided above. We also included a list of examples of possible security mindset behaviors from informal conversations with cybersecurity professionals and advisors to make the description more concrete.
The outreach email led to an intake survey with more information and qualification questions (Appendix B). In our intake survey, as a double-check, we asked potential participants about the extent to which they identified with the security mindset as described, and we only retained participants who answered in the top two scale points on a five-point scale (“quite a lot” or “a great deal”). One potential participant was excluded through this process. Participants chose from a list of job roles from the Canadian Centre for Cyber Security (CCCS) Workforce Development and Curriculum Guide, which consists of 35 specific roles grouped into four domains [ 54 ]. In order to participate, participants had to be currently employed as a cybersecurity professional.
During the recruitment phase, we monitored the spread of different roles included in our sample to make sure that a variety of different roles and domains were included. We also asked participants who had completed interviews to suggest other cybersecurity professionals they knew who might be interested in participating, and we contacted them with the same email advertisement.
We ultimately recruited 21 participants, all from the USA. The majority of the sample identified as male ( n = 17) and White ( n = 18); 4 participants identified as female and 3 identified as Asian or Pacific Islander ( n = 3), the only non-White racial/ethnic category represented in the sample. Participants played a variety of roles within the cybersecurity industry, spanning all four domains listed in the CCCS’s Workforce Development and Curriculum Guide (Table 1 ). Many participants indicated that roles within cybersecurity are not rigidly demarcated, that they identified with multiple roles in CCCS’s guide, and that throughout their career they had fulfilled multiple roles spanning different domains. The largest group of participants had spent a large part of their career in IT, but the sample included a number of divergent occupational backgrounds, including the military, law enforcement, politics, academia, and manual labor.
Three: aspects of self-identified security mindset mentioned by participants ( n = 21), ordered based on their professional roles as demarcated by the CCCS.
| Job category . | Job title . | Monitoring . | Investigating . | Evaluating . |
|---|---|---|---|---|
| Design & develop | Cyber security researcher | |||
| Cyber security researcher | x | x | x | |
| Security architect | x | x | x | |
| Security engineer | x | x | x | |
| Security engineer | x | x | x | |
| Govern & support | Chief information security officer | x | x | |
| Chief information security officer | x | x | x | |
| Chief information security officer | x | x | ||
| Chief information security officer | x | x | x | |
| Chief information security officer | x | x | x | |
| Cyber security manager | x | x | x | |
| Cyber security manager | x | x | x | |
| Cyber security manager | x | x | x | |
| Project manager | x | x | x | |
| Protect & defend | Incident responder/handler | x | x | x |
| Incident responder/handler | x | x | ||
| Penetration tester | x | |||
| Cyber security analyst | x | x | ||
| Cyber security analyst | x | |||
| Operate & maintain | Network security operator/specialist | x | x | |
| Technical support specialist | x |
| Job category . | Job title . | Monitoring . | Investigating . | Evaluating . |
|---|---|---|---|---|
| Design & develop | Cyber security researcher | |||
| Cyber security researcher | x | x | x | |
| Security architect | x | x | x | |
| Security engineer | x | x | x | |
| Security engineer | x | x | x | |
| Govern & support | Chief information security officer | x | x | |
| Chief information security officer | x | x | x | |
| Chief information security officer | x | x | ||
| Chief information security officer | x | x | x | |
| Chief information security officer | x | x | x | |
| Cyber security manager | x | x | x | |
| Cyber security manager | x | x | x | |
| Cyber security manager | x | x | x | |
| Project manager | x | x | x | |
| Protect & defend | Incident responder/handler | x | x | x |
| Incident responder/handler | x | x | ||
| Penetration tester | x | |||
| Cyber security analyst | x | x | ||
| Cyber security analyst | x | |||
| Operate & maintain | Network security operator/specialist | x | x | |
| Technical support specialist | x |
The participant in the first row of the table is an outlier; they mentioned all three of the aspects noted above, but did not conceptualize them as being part of their security mindset (see section 3.2).
This study was approved by the Stanford University Institutional Review Board before recruitment (Protocol #60 764). After initial recruitment and the intake survey, 21 semi-structured interviews were conducted by one or both of the two main researchers over Zoom. Before starting interviews, participants were asked to review and sign an informed consent form. Interviews lasted ∼1–2 hours [mean: 1:40; min: 0:46; max: 2:42]. Audio was recorded over Zoom.
The interviews were guided by an interview protocol consisting of open-ended questions and follow-up probes (Appendix C). This protocol was derived from three pilot interviews with cybersecurity professionals, which are not included in the data. The final interview protocol included questions on three broad topics corresponding to our research questions: personal definitions and characteristics of the security mindset, the development of participants’ security mindset, and the personal and professional consequences of the security mindset for participants. Throughout the interviews, the focus was on participants’ own security mindsets, but the conversations also included discussion of the security mindsets of other people, such as employees, colleagues, family, and the public. After completing each interview, participants were given the option to be paid |${\$}$| 30/hour for participation in the study in the form of digital gift cards sent to their email addresses, scaled to the duration of the interview. All interviews were conducted between June and August 2021.
Data processing and analyses
We transcribed the audio recordings of the interviews using the transcription software Otter.ai. Both main researchers listened to all of the interview recordings at least once, reviewing the transcripts for mistakes. We then analyzed the data with the qualitative analysis software MaxQDA + 10 using an inductive and reflexive approach, following the thematic analysis approach of Braun and Clarke [ 55 ]. Thematic analysis consists of six phases: familiarization with the data, coding, theme generating, theme review, theme naming, and write up [ 56 ]. Lines of text of the interview were labeled with codes. These codes had a semantic focus, rather than a latent one, meaning that codes represented the explicit “surface level” meaning of a line of text rather than any implicit underlying meaning [ 55 ]. Both main researchers engaged in this analysis, checking each other’s work and meeting regularly to discuss. Semantic codes were grouped into themes, and these themes were discussed among the main researchers and with the wider research team for a critical evaluation. Lastly, the resulting themes were given finalized names. These phases are iterative rather than chronological, meaning that we moved back and forth between them before reaching our final results. The primary goal of our research was to discover recurring and emerging themes rather than establishing a precise level of agreement, which would be appropriate for a more confirmatory approach to analysis. Therefore, following established practices in qualitative research [ 57 ], we decided that calculating inter-rater agreement was not appropriate for this study.
During analysis, we found that participants’ responses about their conceptualization of the security mindset could be grouped into three themes, which we labeled “monitoring,” “investigating,” and “evaluating.” We also coded themes related to participants’ self-reported development of their security mindsets, their motivations for engaging the mindset, and the personal and professional consequences of engaging the mindset. We compared these latter themes with the three conceptual themes across participants in order to identify variations in the development, motivation, and consequences of the security mindset across the categories of monitoring, investigating, and evaluating. For example, we were able to identify curiosity as a common self-reported motivation for investigating, but not for evaluating.
Finally, we use pseudonyms when attributing quotes below in order to protect the anonymity of the participants. Quotes that contain potentially sensitive information were left entirely unattributed to prevent readers from inferring their origins by comparing multiple quotes from the same pseudonym.
Three aspects of the security mindset
Participants tended to define the security mindset in terms of three distinct but interrelated aspects. These are (i) an unconscious habit of monitoring for potential security flaws, (ii) a conscious investigating of systems to confirm security flaws, and (iii) evaluating the seriousness of a given flaw in a larger context.
All but one participant described at least one of the three aspects, but different participants included different aspects into their own definitions, and we found all possible combinations of the three aspects in our sample. Most participants associated all three aspects with the term “security mindset” but emphasized their own proclivity for one of them.
When describing their security mindsets, most participants said that they automatically, unconsciously, and uncontrollably spotted potential security flaws in the digital, physical, and social worlds around them. We call this process “monitoring.” Many participants said that they are always monitoring, even when not in a work context. They described monitoring in terms of a heightened sensitivity for cues that could reveal security vulnerabilities upon further inspection.
And that security mindset, I think about it as sort of like a spidey sense, right? It’s not something that you’re thinking about in your forebrain, but it’s always kind of percolating in the back. Once you start to see things in the world through that lens, then everything kind of… you can’t help yourself, everywhere you go, you know, you're in the airport, you see a machine and you think of [potential vulnerabilities]. (Jonathan)
Participants drew from their areas of expertise in their monitoring. For example, participants with an information and communications technology background tended to monitor more for cues that could suggest digital vulnerabilities, such as suspicious URLs or email requests, while those with a military or law enforcement background were more likely to mention cues that could suggest physical vulnerabilities like unlocked doors or suspicious strangers. For example, one participant with a military background said “Do you remember the shooting that happened in Las Vegas? […] So now that’s part of my threat landscape now. Now I’m also looking for high windows.” However, most participants reported being attentive to potential security vulnerabilities in both domains.
Many participants also monitored for cues that were unexpected but not immediately suggestive of potential security flaws. One participant mentioned, “Any time you notice something that is outside of the expected behavior, that’s a trigger.” In the digital domain, this could be a web page that loads in an unexpected manner or an unusual error message. In the physical domain, one participant described a situation in which he did not find anyone in a street that he expected to be busy. While some people might not think twice about such an observation, for this participant it acted as a trigger to engage in “investigating,” which we describe below.
Investigating
Participants also described a second, distinct, and more conscious mental process that becomes active once they have noticed something unusual while monitoring. We call this second process “investigating.” Investigating involves “thinking like an attacker”—expending mental effort to learn if a certain cue is in fact a sign of an actual security vulnerability.
It’s not like I look at a system and can immediately list out the 800 ways I can break it, I just have to sort of be like… “Oh, wonder if this would work?” or “Wonder if that’s like…?” […] And that’s where I think I would take the next step. (Bob)
Many participants used spatial metaphors such as “pathways” and “routes” to describe the different mental steps they would think through, as if they were mentally simulating navigating an imaginary space. According to participants, the process of investigation may be entirely mental, but it could also involve probing real systems, such as trying to enter a password-protected page by inputting code or trying to open supposedly locked doors.
Investigating was particularly emphasized by “Protect & Defend” roles such as penetration testers, but it was also the most commonly mentioned aspect of the security mindset overall. Some participants described that the process of investigating has become so automatic that it sometimes happens almost instantaneously. With experience, a participant might go in a split second from monitoring, to investigating, to identifying a security flaw. In fact, some participants blurred the distinction between monitoring and investigating, with one participant saying “I would have a tendency to see the failure modes of something even before engaging with it.”
Many participants made the point that perfect security is impossible. Most large systems will have an uncountable number of potential weaknesses for attackers, and some will never be found. Time and cognitive resources are scarce, and therefore one cannot engage with every single cue one encounters. It is better to prioritize which investigations are worth one’s efforts. We call this process “evaluating,” and several participants described it as an important element of their security mindset. For example, one participant said “A security mindset, it gives you an opportunity to help sorting or stack-ranking the things that you would start with.” Participants described evaluating in terms of intuiting the likelihood and magnitude of harm associated with a given security threat in order to arrive at a judgment on how to proceed:
So there’s the first aspect of, like, “recognize what all the possibilities are,” and that’s really the immature security mindset, right? Which is like, where you realize, “Oh, crap, I’ve got [metaphorical] doors and windows all over!” […] But then the next level is like looking at it from a very pragmatic standpoint: What is the likelihood of that, right? Because you’re looking at threat, vulnerability, likelihood, you’re looking at all those things all combined together, to determine risk. (Vincent)
Some participants described evaluating as a more conscious process, while others described it as more of an unconscious and intuitive judgment. Several participants also mentioned that it was helpful for them to consider what one called the “drives, motivations, incentives, and goals” of potential attackers in order to properly evaluate security flaws.
Of the three aspects, evaluating was the least-frequently mentioned. It was emphasized most by participants in “Govern & Support” and “Design & Develop” roles, such as Chief Information Security Officers (CISOs) and cybersecurity managers, and less so by participants in more front-line “Protect & Defend” and “Operate & Maintain” roles.
An integrated view
Despite the differences in emphasis between the three aspects of the security mindset, participants described them as mutually reinforcing in a number of ways, summarized in Figure 1 below. When integrating these aspects, a coherent picture arises of the security mindset as made up of three distinct but interlocking processes.

Relationships between aspects of the security mindset described by participants. Habitually monitoring for potential security threats can trigger a conscious process of deeper investigation, which, if successful, reinforces the habit of monitoring. Monitoring and investigating can also inform subsequent evaluating of the relative risk of threats. Evaluating serves to regulate further monitoring and investigating.
Participants described monitoring and investigating as working hand-in-hand. Unconscious and habitual monitoring for security threats can trigger a more deliberate process of investigating those threats. Investigating can reinforce the habit of monitoring through the rewarding experience of discovering a threat, and it can also provide the monitoring system with more information to use in scanning for future threats. Multiple participants said that after they personally identified an instance of some security flaw, they became more vigilant about that flaw in the future.
Participants who mentioned evaluating described it as being informed, in part, by the experience of monitoring and investigating. By continually searching for and identifying potential threats, people who practice monitoring and identification tend to build what one participant described as a mental “database of probabilities” and another called a “pantheon of common security failures.” This knowledge helps people to evaluate the relative risk associated with a given threat. As the capacity for evaluating develops, it regulates the attention of more experienced professionals so that they monitor and investigate higher-priority threats and ignore smaller ones. Several participants stated that people who lack the capacity for evaluating tend to “waste energy,” to be “worried about the wrong things,” or to have an “immature security mindset.”
As defined here, the security mindset is a morally neutral process of identifying and evaluating security flaws in systems. Many participants stated that the security mindset could be used by prosocial or malicious actors to attack systems or to defend them. In the cybersecurity industry, it is common to differentiate between “white-hats,” who are hackers who explore systems with the consent of their owners, and “gray-” or “black-hats” who do not [ 58 ]. Although some participants did indicate they had dabbled in black- and gray-hat activities in the past, most of the sample strongly identified as white-hats.The three-aspect model of the security mindset is also domain-general—in principle, it can apply to any domain of potential security threats. This matches anecdotal descriptions of the security mindset [ 1 ] and the reports of our participants, who described experiences with digital systems, physical systems like locked doors, and even systems of social interaction and social engineering.
Finally, the three-aspect model helps to clarify the role of security expertise and technical knowledge for the security mindset. Monitoring relies on knowledge of cues that something in the threat landscape is abnormal or potentially vulnerable. Investigating typically relies on technical knowledge about how systems work. Evaluating relies on knowledge of a history of security flaws and which were high-priority, as well as supporting knowledge about the goals and abilities of attackers. Over time, the processes of monitoring, investigating, and evaluating build up their corresponding sets of knowledge. However, as our participants noted and others have previously argued, knowledge and experience are not synonymous with the security mindset because people must be motivated to use them to proactively seek out new security flaws [ 1 , 6 , 17 , 19 , 31 ]. The following two sections of this article help to explain this motivation by describing participants’ personal beliefs and developmental histories related to the security mindset.
Beliefs associated with the security mindset
Many participants endorsed one or more distinctive beliefs that they described as important to their security mindsets. One outlier participant even claimed that a security mindset is not constituted by the processes of monitoring, investigating, and evaluation at all. Instead, the participant conceptualized a security mindset as a set of beliefs that lead people to employ such processes [ 18 ].
One commonly held belief was that the digital, physical, and social worlds are filled with social conventions and abstractions that are provided by authorities to simplify and guide behavior, but that they can be hacked or reimagined with a more granular understanding of the world. For example, one participant described how antivirus software is presented to consumers as a simple kind of shield against attackers, when in reality the interactions between antivirus programs and malware can be far more complex. Another participant described how a locked door can be seen as an abstract object that can only be opened with a key, but is actually just a piece of physical material that is held in place with hinges. A third participant described how many people never reflect on the social conventions between security staff and visitors, when in reality there is nothing stopping one from breaking those conventions. In each case, participants expressed the belief that these abstractions obscure viable and creative courses of action, such as bypassing a firewall, taking the hinges off of a door to open it, or adopting a confident demeanor to walk past security.
Relatedly, several participants expressed the idea that people who are willing to see beyond simple abstractions have power over those who are not, and that this power can be used to cause or prevent harm. One participant used a metaphor sometimes referenced in security, military, and law enforcement circles that there are three kinds of people in the world—“sheep,” “wolves,” and “sheepdogs” [ 59 ]. “Sheep” are people who live happily oblivious to the true nature of the world, while those who do not are either “wolves,” who abuse their power to prey on the sheep, or “sheepdogs,” who use their power to stop the wolves.
A belief in the existence of “wolves” could lead some to see the world as a fundamentally dangerous place—a worldview that has been studied by psychologists [ 60–62 ]. We asked participants if they saw the world as a dangerous place. Their answers varied, but most tended to see the world as somewhat dangerous. However, when speaking about the moral character of humanity, participants were generally positive and expressed the opinion that only a small percentage of people were actively malicious.
Development of the security mindset
We asked participants to describe the origins of their security mindsets. Their responses varied depending on which aspect of the security mindset they emphasized. We present major themes below. Broadly, participants described their security mindsets as driven primarily by curiosity, the satisfaction of discovery, and a sense of altruism, but they also described distinct origins for each of the three aspects of the security mindset.
In summary, participants emphasized that their capacity for investigating arose from a strong curiosity for how things work and a willingness to question authority. Most participants believed that the seeds for the security mindset were sown in childhood through an interest in investigating. They mentioned a number of formative experiences, including circumstances that allowed free exploration of technical systems and activities that simulate investigative security work.
Monitoring tended to develop as a complement to investigating, or in response to environments that were dangerous or that otherwise strongly rewarded attentiveness to potential security flaws. Some participants suggested that being female or holding some kind of minority status might contribute to a greater capacity for monitoring out of a need for personal safety (though others disagreed), but that social conventions and/or lack of access to resources might make it more difficult for these groups to practice investigating. Finally, evaluating developed later than investigating or monitoring, arose from a need to strategically allocate resources at work, and was described as less inherently enjoyable than the other two aspects.
Development of investigating
Most participants described investigating as an inherently enjoyable process, and almost all of them described curiosity about how things work as the single most important personality trait for the development of their capacity for investigating. This is because investigating often comes up empty. Participants that gave a quantitative estimate said that 70–90% of their searches do not lead to a security vulnerability being identified. Instead, participants are often motivated by the desire to simply understand a system. Though they all described enjoying the process of investigating, many participants also described being sensitive to the visceral reward of uncovering a security flaw, using phrases like “dopamine hit,” “burst of adrenaline,” and “blast of brain chemicals.” One participant said that “there is nothing like it”:
But there is no brain chemical endorphin feeling better than going “Oh, my God, I know a thing. I figured it out, I figured the thing out.” There’s nothing, there’s nothing better in my brain at all, like, and that can be triggered not only by cybersecurity but can be triggered by making any kind of connection between two things people don’t normally make connections between. (McKayla)
Many participants also described feeling a sense of altruistic pleasure from protecting others. One participant described themselves as “one of the good guys” protecting against “the bad guys,” another described feeling mostly driven by “service,” a third described finding a vulnerability as feeling like helping a stranger on the street, and a fourth said: “Whether I find a flaw or not, both is a good outcome: if I don’t find one that means we’re safe, if I do find one that means because of me we will get safer.”
Participants also frequently mentioned a willingness to question authority as important for investigating [ 63 ]. Many participants described a history of testing, questioning, and challenging authority figures such as parents and teachers. Some participants likened this to the security mindset, saying that both involve questioning assumptions, nonconformity, and rule-breaking.
I always kind of had a problem with authority. Growing up, I was never very… I always told high school teachers that they had to earn respect to get it and they never wanted that. Like, I was always that type of person. Like, I never had a blind acceptance of authority. You know, I would talk back if I felt disrespected, or if I felt singled out. So maybe that plays into it. (Samantha)
In addition to the personality traits described above, many participants described one or more formative experiences that contributed to the development of their interest in investigating. We note two below.
Circumstances which allowed free exploration of technical systems were said to aid in the development of investigating. Many participants described taking toys apart in their childhood to see how they would function. They saw this as a first instance of a curiosity for understanding the underlying mechanisms of things—a curiosity that persisted in adult life and came to fruition in cybersecurity. In the early days of the internet and home computing (when many participants were teenagers), computer and telecommunication systems also had very few enforced rules and consequences. Many participants stated that the freedom to explore and play around in this context was essential to them developing a security mindset.
The early internet was an ideal place to apply that curiosity. Because unlike the schoolyard or unlike around the house, frequently, that curiosity could, you know, you could see it through to its conclusion. It goes as deep as you had time for, but frequently without a lot of consequences. Which was great, because I think I like a lot of other people from that generation, we just wanted to explore, we wanted to see what was possible. (Jacob)
Activities that simulate investigative security work were also mentioned as formative. These included childhood games and playground rivalries, urban exploration (the hobby of infiltrating and exploring spaces such as sewers, roofs, or boiler rooms), and hacking competitions.
Well, I think the security mindset arises from a sense of adventure. […] Yeah, this is like around eight or nine years old. […] I kind of had a rivalry with a student at school. […] And we would sort of plan these very elaborate things against each other. Like we would like, try to intercept each other’s secret messages. […] It felt very real. I mean, I’m calling them games now. But you know, when we’re, when I was younger, this was like, a big deal. […] I remember lying in bed at night for hours, thinking through, okay, what’s my next step in this? […] It was just sort of training my mind to think very in depth. Thinking several steps ahead, based on what the adversary might do. […] So I think, something in there, there’s something in there I think, fundamental to a security mindset. (George)
In summary, participants described their history of investigating as deeply driven by curiosity about technical systems. They often had support and free opportunities to explore these systems as part of games and personal projects in childhood and young adulthood, and they were willing to challenge authority figures in the process of doing so.
Development of monitoring
For many of our participants, monitoring arose naturally from an existing personal interest in investigating technical systems. The pleasure of investigating simply led these participants to monitor for new opportunities to do it. But many other participants mentioned that a social environment that values security or security-related behaviors and traits contributed to the development of their capacity for both monitoring and investigating. For example, one participant spent extensive time in a hacking club. Another inherited experience from a military family:
I was raised in a military family. [… Security concerns were] a very normal thing to discuss. It’s very normal to be like “Hey, we’re going to go get the booth in the corner.” Like that was just very normal. And we always knew where dad or grandpa was gonna sit. […] And then as you develop your own sense, and get into that field yourself, you have the ability to also think about those things. (Ash)
For others, monitoring emerged as a means of self-protection in a potentially dangerous or even abusive environment. For example, one participant noted that his military experience trained a quality of situational awareness that translated to cybersecurity. Another believed that growing up in the Soviet Union trained them to monitor for security flaws:
Anyone who’s grown up in the Soviet era has a baseline paranoia about the government listening. […] I already had a proclivity towards it even before I started studying in school. There’s a Russian mindset that often shows up, not for everybody obviously, but like “a vulnerability in the system is there to be exploited, and it’s the fault of the system if it cannot lock.” […] I remember having that kind of socialization, like: systems like shoplifting is yet another system to be hacked, right? (Pseudonym redacted)
Several participants provided personal examples of growing up in abusive or dysfunctional circumstances that led to the cultivation of a capacity for monitoring and/or investigating. One participant reported developing a capacity for monitoring through growing up in a “house full of secrets” related to family abuse. In order to stay safe themselves, they learned to surreptitiously listen in on conversations and access private documents in the house. Another participant described their capacity for monitoring and investigating as developing from the experience of growing up with a mother who had a “narcissistic parenting style”:
So I would try to make sure that you, you know, try to understand her. I was basically, like, I was hacking my mom’s emotional states, right? “If I understand what it is that you need to hear from me in order for you to be okay.” Right. And then making sure that I followed that. […] To be honest, the security mindset… It wasn’t till somebody else said the term that I was like, “Oh, yeah, I guess that is kind of how I do things.” […] It was just me growing up. (Pseudonym redacted)
Development of evaluating
According to our participants, the capacity for evaluating developed later than the capacity for monitoring or investigating. Many described going through a phase of believing that, in their words, “everything is leaky” or that “there are holes everywhere”—what one participant called an “immature security mindset”—before updating to a more nuanced worldview that takes relative risk into account:
I think I initially got better at exploitation […] than I did about having calibrated threat models. And so when you realize how vulnerable everything is that is scary, because everything IS really vulnerable. […] If you have agents that are in your environment, actively exploiting things all the time, then you should be scared or something, right, because there are all of these exploits. But in most scenarios, there are some agents that want to exploit things, but they usually are pretty specific. They usually have specific reasons. And it’s not that scary. (Damian)
Unlike monitoring or investigating, evaluating was not described as inherently enjoyable or satisfying, and no participants described any childhood experiences with evaluating—perhaps because it does not involve a concrete and satisfying resolution of finding or exploiting a flaw in a system. Instead, evaluating was primarily described as being instrumentally useful for their personal work or their organization’s performance. Accordingly, most participants described developing the capacity for evaluating at the workplace. Typically, this happened organically through on-the-job experience. As one participant put it,
Sometimes [decisions are] based on just experience, prior experience and ability to think about previous cases and think about cybersecurity holistically. It takes a couple of years of experience in cybersecurity, doing other types of monitoring, triage, etc. So it’s time-consuming to build up that mental database of events and security findings, etc., that help you make those decisions on your feet. (Penny)
However, a few participants described deliberately training their evaluating skills by reading case studies and reports of hacks and security flaws:
So there are larger-scale survey studies that occur annually by various companies, Verizon, for example, where they talk about these techniques that are found in this percentage of incidents, for example. And so you can try to ground your understanding of likelihoods there. (Fabian)
Gender and race
All four of the female participants in the study indicated that the development of the security mindset is a heavily gendered issue. In three out of these four cases, participants proactively brought up gender without the interviewer specifically inquiring about it. However, they described different effects of gender on monitoring and investigating.
Two out of the four female participants stated that they developed a capacity to monitor their environments for their own personal safety. Their reports are consistent with comments from other participants in section 3.3.2 that spending time in unsafe environments contributed to an ability to monitor. However, one female participant was unsure whether monitoring for her personal safety contributed to their work in cybersecurity, and another actively disagreed that there was a relationship between the two.
According to one female participant, women might have fewer opportunities to develop a capacity for investigating because society often discourages them from bending rules, challenging authority, and subverting the intended functions of things:
Women have this crushed out of them at a really early age: behaving unexpectedly has a much higher penalty for women than it does for men. Your study is missing all of the young women—and especially the young black women—who had this mindset when they were young, but never knew they could develop it, who were told that it was wrong and bad of them to be rude to people, instead of being applauded for thinking unconventionally. (Pseudonym redacted)
One participant suggested that there might be racial differences in the security mindset as well:
I am a white woman. And I don’t know how a lot of my black women friends develop their security mindset. I know fewer of them do than white women. And, white women have a fully developed sense of it less than most white men do. (Pseudonym redacted)
Unfortunately, the sample did not include any participants of Black, Hispanic, or Native American descent. None of the other participants, including the three Asian participants in the sample, gave indication of racial differences related to the development of the security mindset.
Consequences of having a security mindset
Together, monitoring and investigating allowed participants to identify security flaws around them, but in many cases, they became what some participants called an “immature” security mindset—a practice of habitually monitoring and investigating that created stress and conflict in their personal and professional lives. To manage this stress and conflict, some participants pursued distractions, practiced deliberately letting go of their habits, or learned to evaluate the relative severity of security flaws in order to keep them in proper perspective.
Monitoring and investigating help identify security flaws
Existing formal and informal discussion of the security mindset has focused almost exclusively on the supposed advantages of the security mindset for cybersecurity job performance [ 13–15 , 30 ]. The participants in this study strongly agreed—almost all of them believed that the security mindset improved their performance as a cybersecurity professional.
One participant described it as “probably the core reason why I have been successful in my job.” Many others described examples of spotting security vulnerabilities that others overlooked. Several participants in more managerial roles indicated that they look for the security mindset when hiring and they emphasize its value among their existing employees:
As an executive working in cybersecurity today, I find it very hard to attract, develop and retain talent. So to the extent that your research is able to make it easier to screen for and identify folks that have this so-called security mindset, that’s a significant interest to me, both as an American citizen and as an executive working in a cybersecurity function, trying to hire security people. (Jacob)
Unconstrained monitoring and investigating may have negative side effects
Although participants mostly spoke positively of the security mindset, they also mentioned several disadvantages of unconstrained or excessive monitoring and investigating on professional, interpersonal, and intrapersonal levels.
In the workplace, several participants pointed out that cybersecurity professionals who perform a great deal of monitoring and investigating can identify more flaws than an organization has resources to fix. This can create tension between those who identify flaws and those responsible for fixing them, particularly if flaws are low-priority:
People don’t like when people with a security mindset point out vulnerabilities that they think are unlikely to be exploited or like, don’t matter, because it makes their job a lot harder. They don’t want to have to deal with it. […] And so I think it’s often that people are like “security people are so annoying,” because they like, bring up these things, and like, these things don’t matter anyway. (Damian)
On the interpersonal level, several participants reported that having a strong habit for monitoring and investigating negatively influenced their social life outside of work. Because they were more aware of security vulnerabilities than people without a security mindset, they tended to be more careful, which can be perceived as mistrusting:
You do tend to get a little bit jaded and overly suspicious of people. And that can affect your interpersonal relationships. Particularly, you know, it’s kind of a little harder to make friends when you’re so guarded. […] So, my wife hands out her Facebook immediately. Oh my! You’ve got to go through a lot to get on MY Facebook. Stuff like that. And because of that people perceive it as you’re not as warm. (Mick)
Finally, a number of participants emphasized that overzealous and uncontrolled habits of monitoring and investigating can lead to burnout or mental health problems. Constantly monitoring the environment for security flaws can be mentally exhausting and lead to an overly pessimistic worldview:
You don’t need to be a paranoid person to start with, but working in an environment where you’ve got to worry about every last potential threat vector, I think leads to that burnout […] It’s exhausting. And I think that a lot of security people do burn out over time. And I think a primary driver for that burnout is that it really is emotionally and psychologically exhausting to be looking at every situation through the lens of how this thing might fall to pieces. (Jacob)
Methods of regulating monitoring and investigating
Several participants discussed the need to regulate the intensity of monitoring and investigating in order to mitigate the professional, social, and personal downsides described above. They engaged in a variety of strategies. Some aimed to distract themselves from monitoring and investigating through substance use and extreme hobbies.
The most successful people I know who have this mindset, have some form of recreation, where you must keep your attention totally focused on that form of recreation: motorcycle racing, jujitsu, planes, helicopter skiing, firearms […] If you do my hobbies wrong, you die. […] There is nothing like landing a plane to make you not think about cybersecurity. There is nothing like riding a motorcycle at a 30-degree angle around a mountain curve in the middle of a group ride, to make absolutely sure that you are not thinking about cybersecurity! […] Can you turn it on and off? And the answer I would have is, that is the only way I really can. (Pseudonym redacted)
Others described efforts to “dial back” or “let go” of monitoring and investigating over time:
I had a friend at my last company… […] He very much had the security mindset. And I observed it in all of his behaviors. But he was a few years older than I was, maybe 10 years older. And over time, he had intentionally dialed it back and modulated that security mindset in order to increase his enjoyment of his life. And the way he articulated it to me was he said, “Look, you know, we look at the world through a peculiar lens, and it reveals to us all these possible things that could go wrong, and we pride ourselves in being able to navigate those situations successfully. But in order to really be grounded, and to be free, and to be happy, we need to let a lot of that go. Moment to moment, day to day.” And so I’ve taken that to heart. (Jacob)
However, the most commonly cited method for regulating monitoring and investigating was to practice evaluating. Many participants suggested that cybersecurity professionals who are able to accurately evaluate the relative risks associated with security flaws are better able to avoid burnout and conflict that might come from an “immature” security mindset:
So someone who’s new to security might see something and think: “Oh, my gosh, this is a critical incident, we’ve got to… everyone stop what you’re doing!” And maybe later, you might say “No, that’s not a big deal. We can actually ignore this one, you know, these kinds of things happen every day..” (George)
In particular, multiple participants noted an asymmetry between the perspectives of attackers and defenders in cybersecurity. Attackers succeed if they can exploit a single flaw, so cybersecurity professionals who are trained to find flaws can easily assume that each flaw is an urgent problem. But defenders are often already aware that their systems have many flaws, and their focus is on distributing their limited resources to evaluate and mitigate the flaws that are of greatest concern. Defenders may therefore tend to cultivate more of a capacity for evaluating than attackers, all else equal. Organizational management staff also sometimes have a broader sense of the security priorities of an organization compared to lower-level cybersecurity employees, and so they may have more opportunities to develop evaluating. One participant noted these dynamics in the context of “red” (attacker) and “blue” (defender) professionals working together at an organization:
People who maybe are on the blue side of things, or management or anything like that, in my experience, I found those people to be considering the risks and you know, weighing it up a lot more. So you kind of have, you know, your pen testers [cybersecurity professionals who focus on identifying flaws] who might get very, very worried. And then you’ve got your blue team as well […] you know, managers, people who deal with risks day in day out, would consider the risks as well in anything they find and as a result may be less anxious. (Aamir)
Theoretical contributions and recommendations for future research
This paper builds on existing work primarily by disentangling the concept of the security mindset using empirical data. Unlike previous treatments of the concept, which viewed it as a unitary entity [ 1 ] or proposed a decomposition without supporting empirical data [ 11 ], we characterize the security mindset in terms of three distinct but interrelated mental processes. Most participants mentioned all three aspects in their descriptions of their own security mindsets, and they described these aspects as co-occurring and mutually reinforcing.
The three-aspect decomposition of the security mindset suggests a number of directions for future work. Psychology researchers should draw from existing methodologies to develop separate survey measures for monitoring, investigating, and evaluating, investigate their interrelationships and correlations with different aspects of cybersecurity job performance, and eventually use them as targets for evaluating training and other interventions to cultivate a security mindset. Notably, different measures of the security mindset may also be needed for different purposes. For example, measures designed for research and theory development are often optimized for comprehensiveness and psychometric reliability, but they can be impractically time-consuming to administer, and they may be vulnerable to “gaming” or deliberate exploitation [ 28 ].
Our research also identified troubling reports of negative effects of an overactive security mindset, including burnout, mental health challenges, and conflicts at work and in personal relationships. Future work should more thoroughly investigate these issues among cybersecurity professionals, the circumstances in which they arise, and effective means of mitigating them. In particular, some of our participants suggested that evaluating cybersecurity flaws helped to regulate the potential negative effects of overactive monitoring and investigating. Researchers could test this hypothesis by assessing the relationships between the negative effects described above and each of the aspects of the security mindset.
Our work also highlights ambiguity in the concept of a “mindset” that has been recognized in psychology but not yet incorporated into the cybersecurity literature. The participants in our study tended to describe monitoring as a mental lens or filter that is passively and habitually applied to experience, while investigating and evaluating were described as more active thought processes. Many participants also shared a common set of beliefs linked to their security mindsets, such as the belief that superficial appearances of systems are not trustworthy, and one participant defined the security mindset in terms of those beliefs.
This range of responses—mindset as filter, active process, or belief—bears a striking resemblance to the range of meanings found in existing psychological research on mindsets [ 64 ]. Within social psychology and organizational leadership, mindsets are frequently conceptualized as a cognitive filter or frame in which new information is embedded, contextualized, and modified [ 65 , 66 ]. Within cognitive psychology, a mindset has been conceptualized as a grouping of cognitive processes that are activated whenever a certain task is performed [ 67 ]. Finally, some scholars conceptualize a mindset as a set of beliefs about the world that motivates the adoption of different behaviors and ways of thinking [ 68 , 69 ].
Future research on the security mindset should draw from different bodies of literature depending on the meaning of “mindset” that they wish to explore. For example, researchers interested in monitoring as a passive cognitive filter could take inspiration from early construct-building efforts related to the global mindset [ 70 ]. Those interested in the more active, deliberate aspects of investigating and evaluating could look to treatments of mindset in the cognitive psychological tradition, such as Gollwitzer’s work on deliberative vs. implemental mindsets [ 71 ]. Finally, though almost all of our participants did not define their security mindsets in terms of beliefs per se , researchers might look to scholars such as Dweck [ 69 ] to identify beliefs that influence the development of the security mindset.
We also found interesting potential interactions between different aspects of the security mindset and participants’ gender backgrounds. Some of our participants suggested that holding a minority status might contribute to a greater capacity for monitoring one’s environment for security risks, though others questioned if this generalized to other security domains. Other participants noted that social conventions and/or lack of access to resources might make it more difficult for members of minority groups to practice investigating. These tentative findings illustrate the value of distinguishing monitoring from investigating when considering the security mindset, and should be explored through follow-up research in order to provide the best possible opportunities for all cybersecurity learners.
Participants’ descriptions of the security mindset also bear an interesting resemblance to what cognitive psychologists call a model-based mode of learning, in contrast to model-free learning. In model-based learning, a learner first tries to build an accurate model of reality. Then, when faced with a challenge, the learner tries to find a solution by mentally manipulating their imagined model of the world. In contrast, model-free learning is based on trial and error. Here, the learner simply selects actions that have previously worked for themselves or others, without thinking about the underlying mechanism of a system. Future work could examine whether people who self-identify as having a security mindset score higher on tasks that indicate general tendencies toward model-based learning [ 72 ].
Our interviews also suggest previously underexplored intersections between the security mindset and organizational structure. As noted above, monitoring, investigating, and evaluating skills appear to be represented to varying degrees among different roles in a cybersecurity organizational hierarchy. Rather than focusing only on individuals, scholars might study the distributions of monitoring, investigating, and evaluating across teams that most successfully identify and address cyber threats. For example, some participants in our study raised concerns about friction between management and lower-level cybersecurity staff, who might identify flaws but feel that their concerns are not being taken seriously. This might be understood as an instance of lower-level staff failing to properly evaluate the broader significance of their findings, and/or as managers resisting uncomfortable knowledge that poses a risk to project development timelines. Future research could study these and other organizational dynamics in greater detail.
Finally, in this study, we only interviewed self-identified “white-hat” professionals, not “gray-” or “black-hats” who use their cybersecurity skills without permission of the owners of the systems that they explore. Our study did not investigate the factors that lead people to become black-hats vs. white-hats, or the interaction of those factors with the security mindset. All participants that brought up the issue of the moral nature of the security mindset described it as morally neutral and usable for good or evil. The security mindset was described as a powerful set of mental tools, and some could be inspired to practice caution and protect the vulnerable, while others could be tempted to cause harm. Future research into the security mindset should investigate how to cultivate the conditions in which security mindsets are most likely to be used ethically.
Implications for cybersecurity education, training, and self-directed learning
Can the security mindset be developed? Popular discussions of the security mindset have often considered the extent to which it is or is not trainable [ 1 ]. As an initial qualitative investigation, this study does not provide conclusive evidence that the security mindset is trainable, but it suggests potential for significant environmental influences. For many of our participants, monitoring and investigating functioned together as a set of satisfying mental habits that did not always exist, but were driven by curiosity and rewarded by discovery. Participants described developing the capacity for monitoring and investigating through active, exploratory, inquiry-based learning, often via games, simulations, and other supportive social environments in which they could cultivate and indulge their curiosity. Reverse causality and interaction effects are still entirely possible; e.g. people with a predisposition to be curious about mechanical systems may seek out and disproportionately benefit from opportunities to learn about those systems. However, the mechanisms of habit and reward that participants described at the core of the security mindset are universal in humans and non-human animals. Just as virtually all people have the capacity to build strength through exercise, they also have the capacity to build habits through practice and reward [ 73 ]. Insofar as the security mindset is composed of habits, it should be at least somewhat trainable.
Educators and trainers should also note that our participants described their security mindsets as being largely intrinsically motivated. Motivation for an activity can be conceptualized on a continuum from more intrinsic (driven by internal rewards inherent to the activity itself) to more extrinsic (driven by external rewards) [ 74 ]. Our participants tended to emphasize intrinsic rewards of the security mindset like curiosity, the satisfaction of discovery, and taking pride in their work, and they deemphasized or even criticized the use of external rewards and punishments.
Intrinsic motivation toward an activity is most likely to develop in environments where learners feel a sense of autonomy to choose their own pursuits, a sense of competency in the domain in question, and a feeling of connection and relatedness to other learners like them [ 75 , 76 ]. Thus, to support intrinsic motivation, educators and trainers should attempt to find or create learning environments in which learners can develop the skills and motivation to exercise the security mindset by freely exploring, discovering, and investigating security challenges that are accessible at their current level of skill. These learning environments should provide a social community that celebrates tinkering, hacking, bending rules, and asking questions, and they should link the rewards of discovery to outcomes that the learner intrinsically values, whether that is pride in one’s work, a deeper understanding of the workings of a system, or even an opportunity to play a fun harmless prank on a friend. Indeed, a number of our participants described developing their own security mindsets through similar circumstances. Makerspaces could serve as a useful source of inspiration [ 77 , 78 ].
While a full review of inequities in cybersecurity education and practice is outside of the scope of this article [ 79 , 80 ], our research highlights one particular dimension of inequity that deserves further investigation. Our study participants described developing a security mindset in part through free exploration, questioning authority, and some degree of bending and breaking accepted rules of conduct. But learners from marginalized backgrounds often face societal pressure to conform to strict standards of appropriate behavior and experience heavy-handed punishment for disobedience [ 81 , 82 ]. Some of these learners might feel unsafe or uncomfortable engaging in cybersecurity learning activities that are associated with rule-breaking and crime. Future work should investigate the extent to which this dynamic exists and design correctives to support a wider range of cybersecurity learners.
Finally, educators and trainers should consider deliberately developing the evaluating aspect of the security mindset. Our participants indicated that, to some extent, evaluating simply developed with experience over time. However, some participants also claimed that the development of evaluating could be accelerated by reading case studies and reports of real-world security flaws, by conversing with colleagues about high-priority targets and commonly-used attack routes, and sometimes even by speaking with non-security personnel. Educators could potentially adapt this advice for training evaluating abilities among penetration testers and other investigating-focused cybersecurity professionals.
Implications for cybersecurity recruitment
Employers and recruiters seeking to identify job candidates with a security mindset have a number of options available, though more work is needed to evaluate their practical feasibility. First, as described above, curiosity about technical systems appears to be a core driver of the investigating aspect of the security mindset, and it was the single most frequently used code in our study. To the extent possible, employers and recruiters should try to learn about candidates’ genuine curiosity about technical systems. It may be possible to develop survey measures or behavioral assessments of candidates’ curiosity about technical systems, but a great deal of care is needed to ensure that such assessments are not “gamed” or exploited by applicants (an ironic fate for a measure of the security mindset!).
Employers and recruiters might also ask job candidates who have experience in monitoring and investigating about their ability to evaluate the relative priority of different security flaws. For example, they might combine a bug-bounty performance test with a task of explaining the relative risk of different bugs, given different sets of background assumptions. They might also ask candidates for their preferred sources of information about the relative risks of security flaws, or they might inquire about the candidate’s interactions with CISOs or other staff who are more likely to hold an evaluating-heavy role.
Implications for cybersecurity management
Our research suggests that managers of cybersecurity teams may, at least in some cases, be particularly likely to have experience with the “evaluating” aspect of the security mindset. In our sample, monitoring and investigating were emphasized by participants from a variety of different roles, but evaluating was particularly emphasized by participants working in “Govern & Support'' and “Design & Develop” roles, such as CISOs and cybersecurity managers. Evaluating also appeared to help mitigate some of the potential negative consequences of constant monitoring and investigating, such as mental health challenges and misaligned work priorities.
These findings suggest that managers and other senior staff should monitor cybersecurity employees for burnout and other mental health issues, provide mental health support resources as needed, and connect employees with senior mentors and contextual information about organizational goals in order to help them develop the skill of evaluating security flaws in context. By doing so, they might help inform better frontline risk prioritization, improve team communication, and reduce potential risks of burnout.
Implications for policymakers
There are many efforts across US government agencies to build a more capable cybersecurity workforce [ 83 ]. While our results are only based on an initial study of 21 cybersecurity experts, they suggest several initial implications for policymakers:
Fund the creation of learning environments that support the intrinsic motivation to responsibly practice monitoring, investigating, and evaluating in cyber contexts, inspired by makerspaces and similar environments. Make sure that all learners have access to these environments and feel permitted to explore them without stigma—particularly women and members of minority groups who may face particular social pressure to be perceived as rule-abiding and trustworthy.
Fund research to operationalize metrics of each aspect of a security mindset, and to test for their relationships with cybersecurity performance outcomes before exploring their potential usage for recruitment.
Update the DHS Cybersecurity Workforce Development Toolkit [ 84 ] to include information about assessing and mitigating employee mental health concerns, particularly among staff such as penetration testers that may practice extensive monitoring and investigating.
Limitations
This study set out to explore the security mindset as a concept by exploring the perspectives of 21 cybersecurity professionals. Although the sample size of this study is moderately large for a qualitative study [ 85 ], it is still small and focused on the USA. As such, our claims are preliminary and readers should take caution in generalizing from our findings. It is also difficult to draw strong conclusions about subgroups included in our sample, such as women or those working in the different roles of the CCCS’ Workforce Development and Curriculum Guide. Importantly, Black, Latino, and Hispanic participants were also missing in the sample, and may provide a unique perspective not captured by this study.
Our study focused on the perspectives of cybersecurity professionals who already self-identify as having a security mindset based on the minimal description that we formulated from past literature (“the tendency to look for and think about security flaws in the systems around oneself, even when one is not directly instructed to do so”). Selecting participants who fit this description allowed us to focus on our construct of interest, rather than other meanings of the term “security mindset” that participants might use. Future work could use a more open-ended recruitment approach to investigate these other meanings. In addition, it is theoretically possible that some potential participants mis-identified themselves and thus mistakenly included or excluded themselves from the study. However, we found that our participants’ responses were internally coherent and could be grouped into three distinct aspects. In the future, these aspects could be used to develop metrics that can rely less on self-report.
As we conducted interviews, we also sometimes shared some of our evolving impressions of the security mindset with participants to check if they resonated and to prompt further discussion. We only did this toward the end of the interviews to make sure that we did not color participants’ responses. This technique has been recommended for “ensuring accurate representation of participants’ perspectives or experiences” [ 86 ], which seemed particularly important as neither interviewer had a security background. Sharing initial impressions has also been recommended for qualitative research involving early-stage definitions of a construct of interest [ 53 , 87 , 88 ].
However, relying on participants to self-identify and offering them our initial impressions also inevitably creates some potential for social desirability bias [ 89 ]. For example, participants might have overstated the utility of having a security mindset, or understated its drawbacks, in order to more favorably present themselves in interviews. In order to mitigate these risks, we used established interview techniques to guard against social desirability bias, such as not attributing ideas to ourselves (“What do you think of this idea?” vs. “What do you think of our idea?”), prefacing our questions to assure participants that all answers are acceptable, and asking for follow-up information [ 90 ]. Future work could further mitigate risks of bias by seeking out the perspectives of a wider range of cybersecurity professionals, including those who do not personally identify as having a security mindset, and by using research designs that minimize two-way sharing.
The globe is currently facing a cybersecurity “skills gap” [ 12 ]. The security mindset is often discussed in cybersecurity circles as an important, elusive, and possibly even untrainable quality of the best cybersecurity professionals [ 1 ], but empirical research on the security mindset is sparse.
We conducted interviews with 21 cybersecurity professionals who self-identified as having a security mindset in order to understand more about how the security mindset operates, where it comes from, and what effects it has on participants’ personal and professional lives. We found that our participants described the security mindset in terms of three interlocking habitual mental processes: unconscious monitoring for anomalies and potential threats, deliberate investigating of systems to identify security flaws, and evaluating the relative risks of those flaws once discovered. We also identified several common traits and formative experiences of those with a security mindset, and we heard from participants that the security mindset was often enjoyable and professionally valuable, but that it could cause stress, conflict, and burnout if not held in check.
In order to protect against future attacks and build a more resilient digital infrastructure, we need to understand what makes a great cybersecurity expert. Future work should replicate, refine, and operationalize our findings in the field in order to cultivate a generation of cybersecurity professionals who can successfully monitor, investigate, and evaluate potential threats in a healthy, well-balanced, and ethically responsible manner.
The authors would like to thank Gerjo Kok, Rosanna Guadagno, Tom Berson, Kathryn Brink, our study participants, and our anonymous reviewers for their valuable feedback on this project.
The authors declare no conflicts of interest in regard to this article.
This work was supported by the Open Philanthropy Project.
Koen Schoenmakers (Conceptualization, Formal analysis, Investigation, Methodology, Project administration, Writing – original draft, Writing – review & editing), Daniel Greene (Conceptualization, Data curation, Formal analysis, Investigation, Methodology, Project administration, Software, Supervision, Visualization, Writing – original draft, Writing – review & editing), Sarah Stutterheim (Supervision, Writing – original draft, Writing – review & editing), Herbert Lin (Conceptualization, Methodology, Supervision, Writing – review & editing), and Megan J. Palmer (Conceptualization, Funding acquisition, Methodology, Project administration, Resources, Software, Supervision, Writing – original draft, Writing – review & editing).
Schneier B. The security mindset – Schneier on security . Schneier on Security . 2008 .
Google Scholar
Google Preview
Naden C. The cybersecurity skills gap . 2021 . www.iso.org (8 January 2022, date last accessed) .
Vogel R. Closing the cybersecurity skills gap . Salus Journal . 2016 ; 4 : 32 .
Rosso C. The real-world impact of the global cybersecurity workforce gap on cyber defenders . Dark Reading . 2021 .
Morgan S. Cybersecurity Jobs Report 2018–2021 . Cybersecurity Ventures . 2021 : 1 – 5 .
Joint Task Force on Cybersecurity Education . Cybersecurity Curricula 2017: Curriculum Guidelines for Post-Secondary Degree Programs in Cybersecurity . New York, NY : Association for Computing Machinery , 2017 .
Burrell DN . An Exploration of the Cybersecurity Workforce Shortage . Int J Hyperconnect Internet Things . 2018 ; 2 : 29 – 41 .
Peslak A , Hunsinger DS . What is cybersecurity and what cybersecurity skills are employers seeking? . IIS . 2019 ; 2 : 67 – 72 . 10.48009/2_iis_2019_62-72
Emsi . Build (Don’t Buy): A Skills-Based Strategy to Solve the Cybersecurity Talent Shortage . 2020 . https://lightcast.io/resources/research/build-don-t-buy (6 January 2022, date last accessed) .
Petersen R , Santos D , Smith MC et al. Workforce Framework for Cybersecurity (NICE Framework) . https://doi.org/10.6028/NIST.SP.800-181r1 (6 January 2022, date last accessed) .
Padmos A. Against mindset . Proceedings of the New Security Paradigms Workshop on – NSPW ’18 , 2018 . p. 1 – 16 .
ISC2 . (ISC) 2 2020 Cybersecurity Workforce Study (English) . 2020 . www.isc2.org (6 January 2022, date last accessed) .
Tripwire . The Security Mindset: The Key to Success in the Security Field . https://www.tripwire.com/state-of-security/the-security-mindset-the-key-to-success-in-the-security-field (6 January 2022, date last accessed) .
O'Toole B. How to build a security mindset . https://www.linkedin.com/pulse/how-build-security-mindset-brian-o-toole/ (6 January 2022, date last accessed).
Conti G , Caroland J. Embracing the Kobayashi Maru: why you should teach your students to cheat . IEEE Secur Priv . 2011 ; 9 : 48 – 51 .
International Computer Science Institute . Lesson 1 – The Security Mindset: Cybersecurity through Threat Modeling . https://teachingsecurity.org/lesson-1-the-security-mindset/ (8 January 2022, date last accessed)
Cappos J , Weiss R. Teaching the security mindset with reference monitors . Proceedings of the 45th ACM Technical Symposium on Computer science education – SIGCSE ’14 , 2014 . p. 523 – 8 .
Dutton WH. Fostering a cyber security mindset . Internet Policy Rev . 2017 ; 6 : 1 – 14 .
Bonver E , Cohen M. Developing and retaining a security testing mindset . IEEE Secur Priv . 2008 ; 6 : 82 – 5 .
Hooshangi S , Weiss R , Cappos J. Can the security mindset make students better testers? . Proceedings of the 46th ACM Technical Symposium on Computer Science Education – SIGCSE ’15 , 2015 . p. 404 – 9 .
Pournaghshband V. Teaching the security mindset to CS1 students . Proceeding of the 44th ACM technical symposium on Computer science education – SIGCSE ’13 , 2013 . p. 1 – 6 .
Brown KW , Ryan RM , Creswell JD. Mindfulness: theoretical foundations and evidence for its salutary effects . Psychol Inq . 2007 ; 18 : 211 – 37 .
Beilock SL , Carr TH. On the fragility of skilled performance: what governs choking under pressure? . J Exp Psychol Gen . 2001 ; 130 : 701 – 25 .
Walton GM , Cohen GL. A question of belonging: race, social fit, and achievement . J Pers Soc Psychol . 2007 ; 92 : 82 .
Creswell JD. Mindfulness interventions . Annu Rev Psychol . 2017 ; 68 : 491 – 516 .
Ramirez G , Beilock SL. Writing about testing worries boosts exam performance in the classroom . Science . 2011 ; 331 : 211 – 3 .
Walton GM , Brady ST. The social-belonging intervention . In: Walton GM , Crum AJ (eds.), Handbook of Wise Interventions: How Social-Psychological Insights can Help Solve Problems . New York, NY : The Guilford Press , 2020 , 36 – 62 .
Yeager D , Bryk A , Muhich J et al. Practical Measurement . California, CA : Carnegie Foundation for the Advancement of Teaching . 2013 .
Walton GM , Crum AJ. Handbook of Wise Interventions . New York, NY : The Guilford Press , 2020 .
Nassiokas T. Security mindset – What is it? Why is it important? What does Bruce Schneier think? . https://www.linkedin.com/pulse/security-mindset-what-why-important-does-bruce-think-theo-nassiokas/ (8 January 2022, date last accessed).
Potter B , McGraw G. Software security testing . IEEE Secur Priv . 2004 ; 2 : 81 – 5 .
Severance C . Bruce Schneier: the security mindset . Computer . 2016 ; 49 : 7 – 8 .
Haney JM , Theofanos M , Acar Y et al. “We make it a big deal in the company”: Security mindsets in organizations that develop cryptographic products . SOUPS '18: Proceedings of the Fourteenth USENIX Conference on Usable Privacy and Security , 2018 , p. 357 – 73 .
Smith J , Theisen C , Barik T. A case study of software security red teams at Microsoft . 2020 IEEE Symposium on Visual Languages and Human-Centric Computing (VL/HCC) . Dunedin, New Zealand : IEEE , 2020 , p. 1 – 10 .
Sommestad T , Karlzén H , Hallberg J. A meta-analysis of studies on protection motivation theory and information security behaviour . Int J Inf Secur Priv . 2015 ; 9 : 26 – 46 .
Briggs P , Jeske D , Coventry L. Behavior change interventions for cybersecurity . In: Little L , Sillence E , Joinson A (eds.), Behavior Change Research and Theory . United Kingdom : Elsevier , 2017 , 115 – 36 .
Kam H-J , Menard P , Ormond D et al. Cultivating cybersecurity learning: an integration of self-determination and flow . Comput Secur . 2020 ; 96 : 101875 .
Kam H , Ormond DK , Menard P et al. That’s interesting: an examination of interest theory and self-determination in organisational cybersecurity training . Inf Syst J . 2021 ; 32 : 888 – 926 .
Reeves A , Calic D , Delfabbro P. “Get a red-hot poker and open up my eyes, it’s so boring” 1 : employee perceptions of cybersecurity training . Comput Secur . 2021 ; 106 : 102281 .
Markus HR. What moves people to action? Culture and motivation . Curr Opin Psychol . 2016 ; 8 : 161 – 6 .
Henrich J. Culture and social behavior . Curr Opin Behav Sci . 2015 ; 3 : 84 – 9 .
AlHogail A , Mirza A. Information security culture: a definition and a literature review . 2014 World Congress on Computer Applications and Information Systems (WCCAIS) . Hammamet, Tunisia : IEEE , 2014 , 1 – 7 .
da Veiga A , Astakhova LV , Botha A et al. Defining organisational information security culture—perspectives from academia and industry . Comput Secur . 2020 ; 92 : 101713 .
Nel F , Drevin L. Key elements of an information security culture in organisations . ICS . 2019 ; 27 : 146 – 64 .
Alshaikh M. Developing cybersecurity culture to influence employee behavior: a practice perspective . Comput Secur . 2020 ; 98 : 102003 .
Xie J , Lipford HR , Chu B. Why do programmers make security errors? . 2011 IEEE Symposium on Visual Languages and Human-Centric Computing (VL/HCC) . Pittsburgh, PA : IEEE , 2011 , 161 – 4 .
Xiao S , Witschey J , Murphy-Hill E. Social influences on secure development tool adoption: why security tools spread . Proceedings of the 17th ACM Conference on Computer Supported Cooperative Work & Social Computing . Baltimore Maryland, MA : ACM , 2014 , p. 1095 – 106 .
Votipka D , Abrokwa D , Mazurek ML. Building and validating a scale for secure software development self-efficacy . Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems . Honolulu, HI : ACM , 2020 , p. 1 – 20 .
Vance A , Siponen M , Pahnila S. Motivating IS security compliance: insights from habit and protection motivation theory . Inf Manag . 2012 ; 49 : 190 – 8 .
Chen Y , Galletta DF , Lowry PB et al. Understanding inconsistent employee compliance with information security policies through the lens of the extended parallel process model . Inf Syst Res . 2021 ; 32 : 1043 – 65 .
Sjoberg L. Worry and risk perception . Risk Anal . 1998 ; 18 : 85 – 93 .
Rinner MTB , Gloster AT. Assessing worry: an overview . In: Gerlach AL , Gloster AT (eds.). Generalized Anxiety Disorder and Worrying . 1st ed. New Jersey : Wiley , 2020 , 9 – 23 .
Younas A , Porr C. A step-by-step approach to developing scales for survey research . Nurse Res . 2018 ; 26 : 14 – 9 .
Canadian Centre for Cyber Security . Workforce Development and Curriculum Guide: A Role-Based Guide for Hiring Managers, Education, and Training Providers . Government of Canada , 2020 .
Braun V , Clarke V , Hayfield N et al. Thematic analysis . In: Liamputtong P (ed.), Handbook of Research Methods in Health Social Sciences . Singapore : Springer , 2019 , 843 – 60 .
Braun V , Clarke V. Using thematic analysis in psychology . Qual Res Psychol . 2006 ; 3 : 77 – 101 .
McDonald N , Schoenebeck S , Forte A. Reliability and inter-rater reliability in qualitative research: norms and guidelines for CSCW and HCI practice . Proc ACM Hum-Comput Interact . 2019 ; 3 : 1 – 23 .
Tanczer LM. 50 shades of hacking: how IT and cybersecurity industry actors perceive good, bad, and former hackers . Contemp Secur Policy . 2019 ; 41 : 108 – 28 .
Grossman LtColD . On Combat: The Psychology and Physiology of Deadly Conflict in War and in Peace . Illinois : PPCT Research Publications , 2012 .
Stroebe W , Leander NP , Kruglanski AW . Is it a dangerous world out there? The motivational bases of American gun ownership . Personal Soc Psychol Bull . 2017 ; 43 : 1071 – 85 .
Cook CL , Li YJ , Newell SM et al. The world is a scary place: individual differences in belief in a dangerous world predict specific intergroup prejudices . Group Process Intergroup Relat . 2016 ; 21 : 584 – 96 .. https://doi.org/101177/1368430216670024 .
Blum SC , Silver RC , Poulin MJ. Perceiving risk in a dangerous world: associations between life experiences and risk perceptions . Soc Cogn . 2014 ; 32 : 297 – 314 .
Caloyannides MA. Enhancing security: not for the conformist . IEEE Secur Privacy . 2004 ; 2 : 87 – 8 .
French RP II . The fuzziness of mindsets . Int J Organ Anal . 2016 ; 24 : 673 – 91 .
Gupta AK , Govindarajan V. Cultivating a global mindset . Acad Manag Perspect . 2002 ; 16 : 116 – 26 .
Rhinesmith SH. Global mindsets for global managers . Train Dev . 1992 ; 46 : 63 – 9 .
Gollwitzer PM , Bayer U. Deliberative versus implemental mindsets in the control of action . In: Chaiken S , Trope Y (eds.), Dual-Process Theories in Social Psychology . New York, NY : The Guilford Press , 1999 , 403 – 22 .
Brooks R , Brooks S , Goldstein S. The power of mindsets: nurturing engagement, motivation, and resilience in students . In: Handbook of Research on Student Engagement . New York : Springer , 2012 , 541 – 62 .
Dweck C. Mindset : Changing the Way You Think to Fulfil Your Potential . London : Constable & Robinson , 2017 ,
Perlmutter HV. The Tortuous Evolution of the Multinational Corporation . Practicing Manager . 1969 ; 17 : 13 – 8 .
Gollwitzer PM. Action phases and mind-sets . In: Higgins ET , Sorrentino RM (eds.), Handbook of Motivation and Cognition, Volume 2: Foundations of Social Behavior . New York, NY : The Guilford Press , 1990 , 53 – 92 .
Kool W , Cushman FA , Gershman SJ. When does model-based control pay off? . PLoS Comput Biol . 2016 ; 12 : e1005090 .
Wood W , Rünger D. Psychology of habit . Annu Rev Psychol . 2016 ; 67 : 289 – 314 .
Deci EL , Ryan RM. Self-determination theory: a macrotheory of human motivation, development, and health . Can Psychol/Psychologie Canadienne . 2008 ; 49 : 182 .
Niemiec CP , Ryan RM. Autonomy, competence, and relatedness in the classroom: applying self-determination theory to educational practice . Theory Res Educ . 2009 ; 7 : 133 – 44 .
Kusurkar RA , Croiset G , Ten Cate TJ. Twelve tips to stimulate intrinsic motivation in students through autonomy-supportive classroom teaching derived from self-determination theory . Med Teach . 2012 ; 33 : 978 – 82 .. https://doi.org/103109/0142159×2011599896 .
Konstantinou D , Parmaxi A , Zaphiris P. Mapping research directions on makerspaces in education . Educ Media Int . 2021 ; 58 : 223 – 47 .
Marsh J , Wood E , Chesworth L et al. Makerspaces in early childhood education: principles of pedagogy and practice . Mind Cult Act . 2019 ; 26 : 221 – 33 .
Peacock D , Irons A. Gender inequality in cybersecurity: exploring the gender gap in opportunities and progression . GST . 2017 ; 9 : 25 – 44 .
Esin JO. A call for concern: the unbalanced representation of minorities and women in cybersecurity profession . J Women Minor Technol . 2020 ; 2 . 1 – 11 .
Skiba RJ , Michael RS , Nardo AC et al. The color of discipline: sources of racial and gender disproportionality in school punishment . Urban Rev . 2002 ; 34 : 317 – 42 .
Morris EW , Perry BL. Girls behaving badly? Race, gender, and subjective evaluation in the discipline of African American girls . Sociol Educ . 2017 ; 90 : 127 – 48 .
Cybersecurity & Infrastructure Security Agency . Cybersecurity Workforce Development Resources . 2020 . https://niccs.cisa.gov/workforce-development (8 January 2022, date last accessed) .
National Initiative for Cybersecurity Careers and Studies . Cybersecurity Workforce Development Toolkit . https://nistcsf.com/wp-content/uploads/2019/01/DHS-cybersecurity_workforce_development_toolkit.pdf (8 January 2022, date last accessed).
Boddy CR. Sample size for qualitative research . Qual Mark Res Int J . 2016 ; 19 : 426 – 432 .
Thomas DR. Feedback from research participants: are member checks useful in qualitative research? . Qual Res Psychol . 2017 ; 14 : 23 – 41 .
Waltz CF , Strickland O , Lenz ER. Measurement in Nursing and Health Research . 5th edn . New York, NY : Springer Publishing Company , 2017 .
Miller VA , Reynolds WW , Ittenbach RF et al. Challenges in measuring a new construct: perception of voluntariness for research and treatment decision making . J Empir Res Hum Res Ethics . 2009 ; 4 : 21 – 31 .
Krumpal I. Determinants of social desirability bias in sensitive surveys: a literature review . Qual Quant . 2013 ; 47 : 2025 – 47 .
Bergen N , Labonté R. “Everything Is Perfect, and We Have No Problems”: detecting and limiting social desirability bias in qualitative research . Qual Health Res . 2020 ; 30 : 783 – 92 .
Author notes
Supplementary data.
| Month: | Total Views: |
|---|---|
| May 2023 | 902 |
| June 2023 | 562 |
| July 2023 | 350 |
| August 2023 | 462 |
| September 2023 | 548 |
| October 2023 | 666 |
| November 2023 | 618 |
| December 2023 | 557 |
| January 2024 | 682 |
| February 2024 | 720 |
| March 2024 | 730 |
| April 2024 | 629 |
| May 2024 | 1,173 |
| June 2024 | 421 |
| July 2024 | 425 |
| August 2024 | 706 |
| September 2024 | 171 |
Email alerts
Citing articles via, affiliations.
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
Related Topics
- Application Security
- Cybersecurity Careers
- Cloud Security
- Cyberattacks & Data Breaches
- Cybersecurity Analytics
- Cybersecurity Operations
- Data Privacy
- Endpoint Security
- ICS/OT Security
- Identity & Access Mgmt Security
- Insider Threats
- Mobile Security
- Physical Security
- Remote Workforce
- Threat Intelligence
- Vulnerabilities & Threats
- Middle East & Africa
- Asia Pacific
- Upcoming Events
- Newsletters
- Whitepapers
- Partner Perspectives
Critical Thinking AI in Cybersecurity: A Stretch or a Possibility? Critical Thinking AI in Cybersecurity: A Stretch or a Possibility?
It might still sound far-fetched to say AI can develop critical thinking skills and help us make decisions in the cybersecurity industry. But we're not far off.

August 21, 2024
_chombosan_alamy.jpg?width=1280&auto=webp&quality=95&format=jpg&disable=upscale)
Will artificial intelligence ever think for us? In 2024, when AI is still in somewhat of an early stage, this might be a loaded question. In cybersecurity, the technology doesn't go beyond automating repetitive tasks, leaving security teams to do the decision-making bit. However, AI's impressive growth in the past two years inevitably makes us wonder if, soon enough, it will be used for critical thinking activities in the sector.
This question becomes even more pressing as hackers increasingly use AI to build better, more sophisticated attacks. And, as KPMG posits, the industry must use AI to fight AI . If the industry wishes to be a step ahead of malicious actors, it must also elevate the technology to fight fire with fire. So, security teams must train their AI models to be smarter than their hacker counterparts, nearing critical thinking levels to outsmart attacks.
While AI's possibilities seem limitless and AI cyberattacks are a pressing matter, we can't get ahead of ourselves. There are many improvements yet to be made, and it's up to the cybersecurity industry to channel its development in the correct path. Where should the industry concentrate its efforts so AI can eventually aid in critical thinking tasks?
Let's explore the current state of AI technology in cybersecurity, the obstacles facing its development, and what leaders can do to get it closer to a critical thinking stage.
What's the Current State of AI In Cybersecurity?
In the larger scope, we are still attempting to build trustworthy AI that can generate accurate answers without hallucinations (which have proven to be extremely harmful to cybersecurity). In the cybersecurity industry, it's helping chief information security officers (CISOs) streamline workflows and forensics examine cyberattack incidents. It also provides valuable insights into new attack vectors.
Needless to say, when we talk about critical thinking technology, its purpose will be to aid humans in making decisions that require more than a yes or no answer and to go beyond the current logic we give it — analyzing angles, forecasting outcomes, and suggesting favorable choices.
For example, let's say a company receives a convincing phishing email that appears to be from their CEO requesting an urgent wire transfer of a large sum of money. Traditional AI would simply analyze keywords in the email and sender address. If they match the CEO's information, the transfer could be flagged as legitimate but not necessarily verified.
On the other hand, critical thinking AI would analyze the email content, verify the request, identify anomalies, and cross reference data. This could mean the AI directly contacts the CEO to confirm he made the request, alert security teams about suspicious activities, and check on the CEO's calendar to see if he was even available at the time the email was sent.
AI never makes any vital choices in this scenario because the complexities of our lives, work, and decisions involve numerous little factors that it may not fully comprehend, at least for now. However, it does assess more data points than traditional AI, and becomes more resourceful on its own accord. Ultimately, humans should monitor and confirm its decisions before anything else is done.
This constant vigilance is crucial, especially considering the ongoing arms race with cybercriminals: 93% of leaders already expect daily AI-powered cyberattacks. While the technology is being used to strengthen and secure systems, malicious actors have also found ways to refine their attacks and outsmart cybersecurity protocols — meaning leaders must keep pushing the boundaries of AI to keep platforms safe.
What Are the Most Pressing Obstacles to Building Smarter AI?
It's clear there is a long road ahead to achieving an AI tool we can trust with decision-making in the cybersecurity world. We must start by addressing some major pain points in how we implement the technology right now, like lack of context, data sharing, and unforeseen incidents.
AI is built on large language models (LLM) that can process vast amounts of data, but we might fail to give it a crucial piece of information: context. AI systems often lack the detailed understanding of personal and organizational specifics needed to make accurate choices that reflect a company and its members, leading to potential misjudgments. By giving it company, industry, and more task-specific context, it can begin to arrive at more well-rounded conclusions.
Explaining the "why" will empower AI to discern the best choices in given situations.
Lastly, the technology requires an extreme level of accuracy in terms of its algorithms, data quality, and prompt specificity to achieve the desired outcome. This means training data and algorithms must be optimized continuously, and prompt engineering must be taught to all users.
What Steps Can Cybersecurity Leaders Take to Refine AI?
To fully harness AI's potential while maintaining security, there must be a way to safely provide AI with the necessary context and information. One approach is to create secure and controlled methods for feeding relevant data to AI systems, ensuring they understand the specific goals, context, and security priorities of an organization. For example, automating security scans across attack surfaces can align data with security objectives. Implementing explainable AI and context and scenario-building training data can also help improve AI's critical thinking.
And, as with anything, AI needs limits if we want to get the most optimal results. These limitations will help reign in the tech, preventing it from going out of scope and performing actions that developers didn't anticipate. This is particularly important when considering AI agents capable of executing specific tasks within the context of LLMs. For example, imagine using AI to transfer money for a mortgage payment but instructing it with a twist: "Don't use my money, use John Doe's." It must be developed to avoid unintended manipulation.
It might still sound wild to say AI can develop critical thinking skills and help us make decisions in the cybersecurity industry. However, we're not too far off, and developing the technology through the right path can help businesses build a smarter and more intuitive tool — going above and beyond automation and monitoring.
About the Author

Nenad Zaric
CEO & Co-founder, Trickest
Nenad Zaric is an offensive security professional with more than 10 years of experience in penetration testing, bug bounty hunting, and security automation. He is the co-founder and CEO of Trickest, a company focused on automated offensive cybersecurity. Before founding Trickest, he found critical vulnerabilities in Fortune 500 companies such as Uber, Snapchat, Spotify, Twitter, and Airbnb.
You May Also Like
How to Evaluate Hybrid-Cloud Network Policies and Enhance Security
DORA and PCI DSS 4.0: Scale Your Mainframe Security Strategy Among Evolving Regulations
Harnessing the Power of Automation to Boost Enterprise Cybersecurity
10 Emerging Vulnerabilities Every Enterprise Should Know
State of AI in Cybersecurity: Beyond the Hype
[Virtual Event] The Essential Guide to Cloud Management
Black Hat Europe - December 9-12 - Learn More
SecTor - Canada's IT Security Conference Oct 22-24 - Learn More
Editor's Choice

Managing Third-Party Risk Through Situational Awareness
2024 InformationWeek US IT Salary Report
Product Review: Trend Vision One Cloud Security
Gartner Report: Cyber Asset Attack Surface Management
A CISO's Guide to Geopolitics and CyberSecurity
SecOps Checklist
The Future of Audit, Risk, and Compliance: Exploring AI's Transformative Impact, Use Cases, and Risks
Translate this page from English...
*Machine translated pages not guaranteed for accuracy. Click Here for our professional translations.
Defining Critical Thinking
|
| ||
|
Foundation for Critical Thinking Press, 2008)
Teacher’s College, Columbia University, 1941) | ||
| | ||

IMAGES
VIDEO
COMMENTS
Critical thinking is not just an optional skill—it is a necessity when it comes to cybersecurity. As cyber-attacks become more sophisticated and frequent, professionals in this field must be able to think critically in the face of uncertainty, ambiguity, and complexity.. Critical thinking enables cybersecurity experts to assess risks, evaluate evidence, and make informed decisions that ...
Critical thinking helps to find the optimal solutions to the problems or opportunities ahead of us. This can be applied in many settings: Process change. Creating policy. Conducting a penetration test. Analyzing logs or forensic evidence. Writing code to harden an application. Critical thinking is a key skill for every role in cybersecurity.
Critical thinking involves analyzing and evaluating an issue to form a well-reasoned judgment. For security specialists, this skill is crucial for making informed decisions, solving complex problems, and understanding the implications of various actions. It is a cognitive process that involves analyzing information, evaluating evidence, and reasoning logically to form…
Three Steps to Holistically Assess Cyber Threats. First and foremost, applying critical thinking--which brings together all the skills shown in the "conceptual framework" above--to cyber threats improves an analyst's ability to accurately evaluate and estimate a threat's potential to impact and expose its target.
Learning critical thinking and effective communication skills breed each other. These skills are so essential to learn and apply in security domains. The significance of critical thinking may show itself in good decision-making. It also may support security professionals' fair and fast judgment in times of uncertainty (Safi and Burell 2007).
The Importance of Critical Thinking in Cybersecurity. Definition and Significance of Critical Thinking: Critical thinking is the capability to analyze, evaluate, and synthesize information to make informed decisions. In cybersecurity, it involves the capacity to assess complex situations, identify potential threats, and develop proactive ...
A critical cybersecurity would interrogate these narratives from a social and cultural perspective, challenging the construct of cybersecurity, before even thinking about its technical workings. A critical cybersecurity must insist on disciplinary diversity. A critical cybersecurity must ask who controls the cybersecurity industry.
The Dual Process Theory explains human thought by separating it into two modes: 3. System 1 is aligned with human intuition. It is characterized by fast, effortless, and emotional thoughts that we ...
Top Skills for Cyber Security Professionals 1. Critical Thinking. Richard Bejtlich, senior director at SplunkCIRT, and Jill Knesek, chief security officer at Cheetah Digital, both agree that critical thinking is one of the most important skills a cyber professional can possess. "In my opinion, the most critical skill for a cyber security ...
The key components of critical thinking include: Asking the right questions. Identifying your assumptions. Reaching out to sources of information beyond those readily available. Evaluating data for accuracy, relevance, and completeness. Assessing the data and forming hypotheses. Evaluating the hypotheses, particularly looking for conflicting data.
The key components of critical thinking include: Asking the right questions. Identifying your assumptions. Reaching out to sources of information beyond those readily available. Evaluating data for accuracy, relevance, and completeness. Assessing the data and forming hypotheses. Evaluating the hypotheses, particularly looking for conflicting data.
"In cybersecurity, critical thinking is the difference being ten steps ahead of black-hat hackers (the bad guys), or getting hacked—it's a requirement if we are going to outsmart malicious attacks." If thinking outside the box is what gives hackers a foothold in our organizations, then we must do more than think originally: we must ...
Critical thinking is a must-have skill for cybersecurity professionals. It enables you to analyze complex situations, identify potential vulnerabilities, and make well-informed decisions to protect your organization. By honing your critical thinking skills, you'll become a more effective problem solver and contribute to successfully ...
Critical thinking is not just an optional skill—it is a necessity when it comes to cyber security. As cyber attacks become more sophisticated and frequent, professionals in this field must be able to think critically in the face of uncertainty, ambiguity, and complexity.. Critical thinking enables cyber security experts to assess risks, evaluate evidence, and make informed decisions that ...
This research work focuses on critical thinking and its impact on cyber security. This research is based on two strong premises about critical thinking viz., (1) critical thinking skills outsmart the malicious attacks in cyber security and (2) cyber intelligence is inter twinned with critical thinking. The 21 st century Bloom's taxonomy is ...
In this article we offer 7 questions to ask to make sure your board understands how cybersecurity is being managed by your organization. Simply asking these questions will also raise awareness of ...
Capture the Flag style critical thinking challenges help build the technical skills required for cyber security. In addition to labs and the cyber range, Capture the Flag style critical thinking challenges are a great way to hone your analytical thinking skills while gaining technical experience. ... Cyber Security Market Size, Share & Trends ...
Abstract. The world is facing a cybersecurity skills gap as cybercrime and cyberwarfare grow in importance. One often-discussed quality that is potentially relevant to cybersecurity recruitment and education is the so-called "security mindset": a way of thinking characteristic of some security professionals that they believe to be especially advantageous in their work.
Implementing explainable AI and context and scenario-building training data can also help improve AI's critical thinking. And, as with anything, AI needs limits if we want to get the most optimal ...
Foundation for Critical Thinking. PO Box 31080 • Santa Barbara, CA 93130 . Toll Free 800.833.3645 • Fax 707.878.9111. [email protected]
Critical thinking. Cybersecurity professionals are often called upon to make important, problem-solving decisions for a company's IT department. They'll need to consider security protocols, products and services to buy, and how to approach cybersecurity overall. Critical thinking is an essential part of all of these tasks.