
- Writing Center
- Current Students
- Online Only Students
- Faculty & Staff
- Parents & Family
- Alumni & Friends
- Community & Business
- Student Life
- Video Introduction
- Become a Writing Assistant
- All Writers
- Graduate Students
- ELL Students
- Campus and Community
- Testimonials
- Encouraging Writing Center Use
- Incentives and Requirements
- Open Educational Resources
- How We Help
- Get to Know Us
- Conversation Partners Program
- Weekly Updates
- Workshop Series
- Professors Talk Writing
- Computer Lab
- Starting a Writing Center
- A Note to Instructors
- Annotated Bibliography
- Literature Review
- Research Proposal
- Argument Essay
- Rhetorical Analysis

Literature Review Peer Review

As you begin writing your peer review, remember that your peers benefit more from constructive criticism than vague praise. A comment like "I got confused here" or "I saw your point clearly here" are more useful than "It looks okay to me." Point out ways your classmates can improve their work.
As a writer . . .
When you submit your rough draft, include answers to the following two questions at the top of your draft: What questions do you have for your reviewer? What two (or more) concerns do you have about your literature review?
As a reviewer . . .
Step 1 : First, read your peer’s rhetorical analysis two times: once to get an overview of the paper, and a second time to provide constructive criticism for the author to use when revising his/her paper.
Step 2: Answer the following questions.
- Question 1: Does the draft include an introduction that presents the topic and provides appropriate background information to clarify the context in which the writer is reviewing the literature?
- Question 2: Are the research studies and other types of literature (reviews, theoretical articles, case studies, etc.) grouped according to common denominators? E.g.: qualitative versus quantitative approaches, conclusions of authors, purpose or objective, chronology
- Question 3: Are all individual sources briefly summarized and analyzed, with descriptions of their strengths and weaknesses?
- Question 4: Are the sources reliable? Are they varied?
- Question 5: Does the draft include a conclusion that summarizes the most important contributions sources make to the topic and connects these points to the larger discipline or profession?
- Question 6: What did you find most interesting about this draft?
Step 3: Address the questions and concerns your partner wrote at the top of the draft.
Step 4: Finally, write two short paragraphs in response to your peer:
- In the first short paragraph, write about what the writer does especially well.
- In the second short paragraph, write about what you think the writer should do to improve his or her essay.
Your suggestions will be the most useful part of peer review for your classmates, so focus more of your time on these paragraphs; they will count for more of your peer review grade than the yes or no responses.
Hints for peer review:
- Point out the strengths.
- Address the larger issues first.
- Make specific suggestions for improvement.
- Be tactful but be candid and direct.
- Don’t be afraid to disagree with another reviewer.
- Make and receive comments in a useful way.
- Remember that peer review is not an editing service.

This material was developed by the COMPSS team and is licensed under a Creative Commons Attribution 4.0 International License . All materials created by the COMPSS team are free to use and can be adopted, adapted, and/or shared as long as the materials are attributed. Please keep this information on materials you adopt, adapt, and/or share.
Contact Info
Kennesaw Campus 1000 Chastain Road Kennesaw, GA 30144
Marietta Campus 1100 South Marietta Pkwy Marietta, GA 30060
Campus Maps
Phone 470-KSU-INFO (470-578-4636)
kennesaw.edu/info
Media Resources
Resources For
Related Links
- Financial Aid
- Degrees, Majors & Programs
- Job Opportunities
- Campus Security
- Global Education
- Sustainability
- Accessibility
470-KSU-INFO (470-578-4636)
© 2024 Kennesaw State University. All Rights Reserved.
- Privacy Statement
- Accreditation
- Emergency Information
- Report a Concern
- Open Records
- Human Trafficking Notice
How to Write a Literary Analysis Essay: An Insightful Guide

Welcome to the fascinating world of writing a literary analysis essay – where words come alive, stories unravel, and your insights take center stage. Have you ever wondered how to decode the deeper meanings of your favorite books or express your thoughts in a way that captivates your reader? Well, you're in the right place. In this article, we're diving headfirst into essays writing, breaking down the complexities, and showing you how to craft an essay that not only impresses your teacher but also makes you appreciate literature in a whole new light.
What Is Literary Analysis Essay
According to a literary analysis essay definition, it is a written examination and interpretation of a literary work, typically dissecting its elements such as plot, characters, themes, and symbolism. Going beyond summarization, this type of essay delves into the intricacies of a text, aiming to uncover deeper meanings, explore the author's intentions, and critically evaluate the literary techniques employed. It requires the writer to engage in thoughtful analysis, supported by evidence from the text, to unveil the layers of significance within the work. Through this process, the essay not only offers a nuanced understanding of the literature but also encourages readers to appreciate the artistry and complexity inherent in written narratives. Those students who are not ready to work on such an assignment can simply say, ‘ write my papers ,’ and our experts will handle the task shortly.
Is This Your First Time Writing a Literary Analysis Essay?
Play it safe – let professional writers show you how it’s done!
What Is the Purpose of a Literary Analysis Essay
The purpose of a literary analysis essay is to delve deeply into a literary work, examining its various elements and uncovering layers of meaning beyond the surface narrative. Through critical analysis and interpretation, this type of essay aims to illuminate the themes, characters, settings, and literary devices employed by the author, offering insights into their intentions and the broader significance of the text. By dissecting the nuances of the work, a literary analysis encourages readers to engage with literature on a deeper level, fostering a richer understanding of the human experience, societal issues, and the complexities of language and storytelling. Ultimately, the essay serves as a platform for readers to explore and appreciate the artistry and impact of literature while honing their analytical and critical thinking skills. When you have time, study our guide regarding how to write an analytical essay , which will shed light on more important academic writing aspects.
.webp)
Literary Analysis Outline
Here's a basic outline for this type of essay:
Introduction
- Hook: Engage the reader with a compelling quote, question, or anecdote related to the literary work.
- Background Information: Provide relevant information about the author, the title, and the context of the work.
- Thesis Statement: Clearly state the main point or argument of your analysis.
Body Paragraph 1: Analysis of the Plot
- Provide a brief summary of the plot.
- Analyze key events, plot twists, and their significance.
- Discuss the structure of the narrative and how it contributes to the overall theme.
Body Paragraph 2: Character Analysis
- Introduce and describe the main characters.
- Analyze their traits, motivations, and relationships.
- Discuss how the characters contribute to the development of the story.
Body Paragraph 3: Theme Exploration
- Identify and discuss the major themes in the literary work.
- Provide examples and evidence from the text to support your analysis.
- Explore the deeper meanings and messages conveyed through the themes.
Body Paragraph 4: Literary Devices and Techniques
- Identify and analyze literary devices such as symbolism, imagery, metaphors, and foreshadowing.
- Discuss how these elements enhance the overall impact of the work.
- Summarize the main points discussed in the body paragraphs.
- Restate the thesis in a fresh way.
- Offer final insights or reflections on the literary work's significance and enduring relevance.
Optional: Additional Considerations
- Discuss the cultural or historical context that may influence the interpretation of the work.
- Address any alternative perspectives or counterarguments.
- Offer recommendations for further reading or exploration related to the literary work.
We recommend analyzing this article about how to start a reflection paper to gain extra competence in the domain of school and college writing.
Literary Analysis Essay Topics
Before you commence the assignment, it’s important to find a great topic. For your inspiration, our writers shared 20 literary analysis essay ideas that you can develop in a written form within the framework of your current task.
- Symbolism in "The Great Gatsby."
- Character development in "Hamlet."
- Themes in "To Kill a Mockingbird."
- The significance of the southern setting in "The Sound and the Fury."
- Foreshadowing in "Of Mice and Men."
- Point of view in "The Catcher in the Rye."
- Irony in "Othello."
- Social class in "Pride and Prejudice."
- The motif of light and dark in "Romeo and Juliet."
- Archetypes in "The Hero’s Journey" in "The Hobbit."
- The tragic flaw of Macbeth in "Macbeth."
- The use of nature imagery in "Wuthering Heights."
- The symbolism of the green light in "The Great Gatsby."
- The role of technology in "Fahrenheit 451."
- Character motivations in "The Scarlet Letter."
- The exploration of identity in "The Invisible Man."
- The impact of war on characters in "All Quiet on the Western Front."
- The role of dreams in "A Raisin in the Sun."
- The representation of women in "Jane Eyre."
- The symbolism of the mockingbird in "To Kill a Mockingbird."
How to Write a Literary Analysis Essay Step by Step
In this section, we're ditching the jargon and breaking down the process into simple, actionable steps. Whether you're a wordsmith in the making or someone feeling a bit lost in the world of dissecting literature, we've got your back. Think of this as your roadmap, helping you navigate through characters, themes, and all the juicy stuff that makes a story tick. So, grab your metaphorical magnifying glass and let's dive into the art of making sense of written words without the unnecessary fuss!
.webp)
Step 1: Choose Your Text and Topic
Before actually writing a literary analysis essay, select a literary work that piques your interest or aligns with your academic requirements. Whether it's a novel, play, or poem, opt for a piece that offers rich content for analysis. Once you've chosen your text, narrow down a specific topic or theme within it that you find compelling. This initial step sets the stage for a focused and meaningful exploration. Use our analytical essay writing service to gain the upper hand when tackling this assignment.
Step 2: Create a Strong Thesis Statement
Write a clear and concise literary analysis essay introduction with a thesis statement that outlines the main argument or interpretation you'll be presenting in your essay. This statement should encapsulate your perspective on the chosen topic, providing a roadmap for both you and your readers. A well-defined thesis serves as the backbone of your literary analysis, guiding your analysis and ensuring a cohesive and purposeful essay. In this guide on how to write an essay introduction , you will find more information on this matter.
Step 3: Conduct Textual Analysis
Delve into the chosen literary work and conduct a thorough textual analysis. Pay attention to key elements such as characters, plot, setting, and literary devices employed by the author. Extract relevant quotes and passages that support your thesis, and consider how each element contributes to the overall meaning of the work. By the way, are you working on your capstone or dissertation at the moment? If yes, try our thesis writing services , which is especially helpful for students dealing with long-format scholarly documents.
Step 4: Set the Stage with Context
Establish the context of your literary analysis essay by providing relevant background information on the chosen work. Briefly introduce the author, the time period, and any significant historical or cultural factors that may impact the interpretation of the text. Creating this contextual framework helps orient your readers and prepares them for the nuanced exploration that follows. By offering a snapshot of the broader landscape in which the literary work exists, you set the stage for a more informed and insightful analysis.
Step 5: Construct Analytical Body Paragraphs
Organize your analysis into well-structured body paragraphs. Each paragraph should focus on a specific aspect of your thesis, supported by evidence from the text. Analyze characters, themes, and literary devices individually, connecting each point back to your overarching argument. Use clear and concise language to convey your insights and interpretations effectively.
Step 6: Craft a Thoughtful Conclusion
Summarize your main points, restate your thesis in a new light, and offer final insights in a thoughtful conclusion. Avoid introducing new information in this section but rather emphasize the significance of your analysis and its broader implications. A well-written conclusion leaves a lasting impression and reinforces the value of your literary interpretation. At this point, you have everything you need to become a student who knows how to write a literary analysis essay from A to Z.
Literary Analysis Essay Do’s and Don’ts
- Develop a clear thesis statement.
- Use evidence from the text to support your analysis.
- Organize your essay logically with coherent paragraphs.
- Focus on specific elements like characters, themes, and literary devices.
- Engage with the text critically, questioning and probing meanings.
- Don't summarize the plot extensively; focus on analysis.
- Avoid vague or generic statements without supporting evidence.
- Don't introduce new ideas in the conclusion. Stick to summarizing.
- Avoid excessive quoting; provide brief, relevant excerpts.
- Don't rush; take the time to revise and edit for clarity.
Our college essay service can help you put the finger on any time-consuming or mind-boggling written assignment right now, so use it if you’re in writer’s block or desperately trying to fit into a schedule.
Literary Analysis Essay Writing Tips
Get ready to up your academic writing game! This section is packed with straightforward tips to help you sharpen your skills. Whether you're a senior year student or just a freshman, we've got you covered. From digging into themes to writing insightful interpretations, our tips are here to make your literary analyses shine. Let's dive in and boost your writing skills!
Maintain Consistent Tone and Style
- Keep a consistent tone throughout your essay, aligning with the formality or informality required. Ensure that your writing style complements the nature of your analysis, creating a cohesive and engaging reading experience for your audience.
Focus on Analysis, Not Summary
- Avoid lengthy plot summaries. Instead, delve into the 'why' and 'how' aspects of the text – analyzing characters, themes, and literary devices to uncover deeper meanings.
Provide Textual Evidence
- Support your analysis with concrete examples from the text. This strengthens your argument and demonstrates a close engagement with the literary work.
Organize Coherently
- Structure your essay logically with well-organized paragraphs. Each paragraph should explore a specific aspect of your analysis, contributing to the overall understanding of your thesis.
Critical Engagement
- Approach the text with a critical mindset. Question the author's choices, explore alternative interpretations, and analyze the implications of various literary elements.
Concise and Clear Language
- Express your ideas using clear and concise language. Avoid unnecessary jargon, and ensure that your analysis is easily understandable by a broader audience.
Revise and Edit
- Take the time to revise your essay for clarity and coherence. Check for grammar and spelling errors, and ensure that each paragraph contributes meaningfully to your overall analysis.
Time is running out? Pay for essay now, and it will be ready tomorrow or even today! We write all types of essays across dozens of academic disciplines, which means you can have any assignment finished expertly and without delays.
Literary Analysis Essay Example
Students might find a literary analysis essay example invaluable for several reasons. Firstly, it provides a practical demonstration of the theoretical concepts they learn in class, offering a tangible model of how to analyze and interpret literary elements effectively. Additionally, examples serve as templates, offering insights into the proper structure and organization of an essay. They help students grasp the application of critical thinking skills, showcasing how to dissect a text, identify themes, and support arguments with textual evidence.
Example 1: The Symbolism of Light and Darkness in Joseph Conrad's "Heart of Darkness"
This literary analysis of Joseph Conrad's "Heart of Darkness" explores the pervasive symbolism of light and darkness throughout the novel. Examining the journey of the protagonist, Marlow, and the character of Kurtz, the essay delves into the metaphorical implications of light and darkness as they represent moral ambiguity, the corrupting influence of power, and the ironic consequences of European imperialism.
Example 2: The Complex Portrait of Identity in Jhumpa Lahiri's "The Namesake"
This literary analysis of Jhumpa Lahiri's "The Namesake" explores the intricate layers of identity depicted in the novel, focusing on the protagonist Gogol Ganguli's navigation through the complexities of cultural assimilation and the immigrant experience. The essay delves into the symbolic significance of Gogol's name as a representation of the clash between his Bengali heritage and the American environment, examining the tension between tradition and modernity.
Final Thought
To sum it up, getting the hang of how to write a literary analysis essay is an experience that benefits both new and experienced writers. Throughout this guide, we've tried to simplify the process, offering practical insights and tips. Analyzing literature isn't just an academic exercise – it's a way to dive deeper into the richness of written expression. Now armed with these tools, you're not only prepared to analyze literature effectively but also to bring your unique perspectives to the ongoing discussion about the stories we encounter. Happy writing!
Haven’t Read the Literary Original Yet?
Don’t put off till tomorrow what you can order from our service today!
What Is the Purpose of a Literary Analysis Essay?
What is literary analysis essay, how to start a literary analysis essay.

is an expert in nursing and healthcare, with a strong background in history, law, and literature. Holding advanced degrees in nursing and public health, his analytical approach and comprehensive knowledge help students navigate complex topics. On EssayPro blog, Adam provides insightful articles on everything from historical analysis to the intricacies of healthcare policies. In his downtime, he enjoys historical documentaries and volunteering at local clinics.


45 Writing Process: Peer Review Literary Analysis
Peer review literary analysis.
- The date listed on the assignment is the date that your link will be posted. This is worth 5 points.
- I will grade your Rough Draft. This is worth 20 points. You should have a complete analysis of your article with examples of the rhetorical elements as well as an evaluation of the overall article.
- Complete Peer Editing. This is worth 20 points. You will select two (2) papers. Write the names of your colleagues on the Discussion posting so that I know whose work you will review. I will look at their Google docs to see that you are making seven to ten constructive comments or asking good questions on each paper. Use this as a guide: Link . Your comments or questions will not be evaluative (great job! terrible!); instead, you will use the rubric to let your colleague know how well you do or do not understand the writing.
ENG101 for Health Sciences Copyright © by Lori Walk; Christine Jones; and Aaron Fried is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License , except where otherwise noted.
Share This Book
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
Methodology
- What Is Peer Review? | Types & Examples
What Is Peer Review? | Types & Examples
Published on December 17, 2021 by Tegan George . Revised on June 22, 2023.
Peer review, sometimes referred to as refereeing , is the process of evaluating submissions to an academic journal. Using strict criteria, a panel of reviewers in the same subject area decides whether to accept each submission for publication.
Peer-reviewed articles are considered a highly credible source due to the stringent process they go through before publication.
There are various types of peer review. The main difference between them is to what extent the authors, reviewers, and editors know each other’s identities. The most common types are:
- Single-blind review
- Double-blind review
- Triple-blind review
Collaborative review
Open review.
Relatedly, peer assessment is a process where your peers provide you with feedback on something you’ve written, based on a set of criteria or benchmarks from an instructor. They then give constructive feedback, compliments, or guidance to help you improve your draft.
Table of contents
What is the purpose of peer review, types of peer review, the peer review process, providing feedback to your peers, peer review example, advantages of peer review, criticisms of peer review, other interesting articles, frequently asked questions about peer reviews.
Many academic fields use peer review, largely to determine whether a manuscript is suitable for publication. Peer review enhances the credibility of the manuscript. For this reason, academic journals are among the most credible sources you can refer to.
However, peer review is also common in non-academic settings. The United Nations, the European Union, and many individual nations use peer review to evaluate grant applications. It is also widely used in medical and health-related fields as a teaching or quality-of-care measure.
Peer assessment is often used in the classroom as a pedagogical tool. Both receiving feedback and providing it are thought to enhance the learning process, helping students think critically and collaboratively.
Receive feedback on language, structure, and formatting
Professional editors proofread and edit your paper by focusing on:
- Academic style
- Vague sentences
- Style consistency
See an example
Depending on the journal, there are several types of peer review.
Single-blind peer review
The most common type of peer review is single-blind (or single anonymized) review . Here, the names of the reviewers are not known by the author.
While this gives the reviewers the ability to give feedback without the possibility of interference from the author, there has been substantial criticism of this method in the last few years. Many argue that single-blind reviewing can lead to poaching or intellectual theft or that anonymized comments cause reviewers to be too harsh.
Double-blind peer review
In double-blind (or double anonymized) review , both the author and the reviewers are anonymous.
Arguments for double-blind review highlight that this mitigates any risk of prejudice on the side of the reviewer, while protecting the nature of the process. In theory, it also leads to manuscripts being published on merit rather than on the reputation of the author.
Triple-blind peer review
While triple-blind (or triple anonymized) review —where the identities of the author, reviewers, and editors are all anonymized—does exist, it is difficult to carry out in practice.
Proponents of adopting triple-blind review for journal submissions argue that it minimizes potential conflicts of interest and biases. However, ensuring anonymity is logistically challenging, and current editing software is not always able to fully anonymize everyone involved in the process.
In collaborative review , authors and reviewers interact with each other directly throughout the process. However, the identity of the reviewer is not known to the author. This gives all parties the opportunity to resolve any inconsistencies or contradictions in real time, and provides them a rich forum for discussion. It can mitigate the need for multiple rounds of editing and minimize back-and-forth.
Collaborative review can be time- and resource-intensive for the journal, however. For these collaborations to occur, there has to be a set system in place, often a technological platform, with staff monitoring and fixing any bugs or glitches.
Lastly, in open review , all parties know each other’s identities throughout the process. Often, open review can also include feedback from a larger audience, such as an online forum, or reviewer feedback included as part of the final published product.
While many argue that greater transparency prevents plagiarism or unnecessary harshness, there is also concern about the quality of future scholarship if reviewers feel they have to censor their comments.
In general, the peer review process includes the following steps:
- First, the author submits the manuscript to the editor.
- Reject the manuscript and send it back to the author, or
- Send it onward to the selected peer reviewer(s)
- Next, the peer review process occurs. The reviewer provides feedback, addressing any major or minor issues with the manuscript, and gives their advice regarding what edits should be made.
- Lastly, the edited manuscript is sent back to the author. They input the edits and resubmit it to the editor for publication.
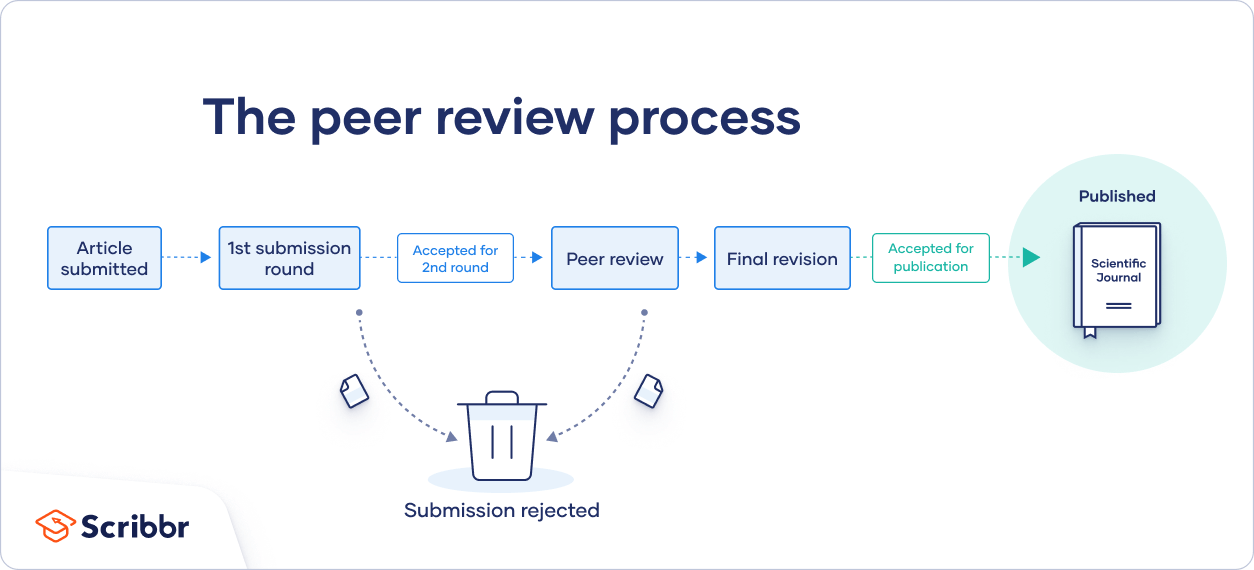
In an effort to be transparent, many journals are now disclosing who reviewed each article in the published product. There are also increasing opportunities for collaboration and feedback, with some journals allowing open communication between reviewers and authors.
It can seem daunting at first to conduct a peer review or peer assessment. If you’re not sure where to start, there are several best practices you can use.
Summarize the argument in your own words
Summarizing the main argument helps the author see how their argument is interpreted by readers, and gives you a jumping-off point for providing feedback. If you’re having trouble doing this, it’s a sign that the argument needs to be clearer, more concise, or worded differently.
If the author sees that you’ve interpreted their argument differently than they intended, they have an opportunity to address any misunderstandings when they get the manuscript back.
Separate your feedback into major and minor issues
It can be challenging to keep feedback organized. One strategy is to start out with any major issues and then flow into the more minor points. It’s often helpful to keep your feedback in a numbered list, so the author has concrete points to refer back to.
Major issues typically consist of any problems with the style, flow, or key points of the manuscript. Minor issues include spelling errors, citation errors, or other smaller, easy-to-apply feedback.
Tip: Try not to focus too much on the minor issues. If the manuscript has a lot of typos, consider making a note that the author should address spelling and grammar issues, rather than going through and fixing each one.
The best feedback you can provide is anything that helps them strengthen their argument or resolve major stylistic issues.
Give the type of feedback that you would like to receive
No one likes being criticized, and it can be difficult to give honest feedback without sounding overly harsh or critical. One strategy you can use here is the “compliment sandwich,” where you “sandwich” your constructive criticism between two compliments.
Be sure you are giving concrete, actionable feedback that will help the author submit a successful final draft. While you shouldn’t tell them exactly what they should do, your feedback should help them resolve any issues they may have overlooked.
As a rule of thumb, your feedback should be:
- Easy to understand
- Constructive
Prevent plagiarism. Run a free check.
Below is a brief annotated research example. You can view examples of peer feedback by hovering over the highlighted sections.
Influence of phone use on sleep
Studies show that teens from the US are getting less sleep than they were a decade ago (Johnson, 2019) . On average, teens only slept for 6 hours a night in 2021, compared to 8 hours a night in 2011. Johnson mentions several potential causes, such as increased anxiety, changed diets, and increased phone use.
The current study focuses on the effect phone use before bedtime has on the number of hours of sleep teens are getting.
For this study, a sample of 300 teens was recruited using social media, such as Facebook, Instagram, and Snapchat. The first week, all teens were allowed to use their phone the way they normally would, in order to obtain a baseline.
The sample was then divided into 3 groups:
- Group 1 was not allowed to use their phone before bedtime.
- Group 2 used their phone for 1 hour before bedtime.
- Group 3 used their phone for 3 hours before bedtime.
All participants were asked to go to sleep around 10 p.m. to control for variation in bedtime . In the morning, their Fitbit showed the number of hours they’d slept. They kept track of these numbers themselves for 1 week.
Two independent t tests were used in order to compare Group 1 and Group 2, and Group 1 and Group 3. The first t test showed no significant difference ( p > .05) between the number of hours for Group 1 ( M = 7.8, SD = 0.6) and Group 2 ( M = 7.0, SD = 0.8). The second t test showed a significant difference ( p < .01) between the average difference for Group 1 ( M = 7.8, SD = 0.6) and Group 3 ( M = 6.1, SD = 1.5).
This shows that teens sleep fewer hours a night if they use their phone for over an hour before bedtime, compared to teens who use their phone for 0 to 1 hours.
Peer review is an established and hallowed process in academia, dating back hundreds of years. It provides various fields of study with metrics, expectations, and guidance to ensure published work is consistent with predetermined standards.
- Protects the quality of published research
Peer review can stop obviously problematic, falsified, or otherwise untrustworthy research from being published. Any content that raises red flags for reviewers can be closely examined in the review stage, preventing plagiarized or duplicated research from being published.
- Gives you access to feedback from experts in your field
Peer review represents an excellent opportunity to get feedback from renowned experts in your field and to improve your writing through their feedback and guidance. Experts with knowledge about your subject matter can give you feedback on both style and content, and they may also suggest avenues for further research that you hadn’t yet considered.
- Helps you identify any weaknesses in your argument
Peer review acts as a first defense, helping you ensure your argument is clear and that there are no gaps, vague terms, or unanswered questions for readers who weren’t involved in the research process. This way, you’ll end up with a more robust, more cohesive article.
While peer review is a widely accepted metric for credibility, it’s not without its drawbacks.
- Reviewer bias
The more transparent double-blind system is not yet very common, which can lead to bias in reviewing. A common criticism is that an excellent paper by a new researcher may be declined, while an objectively lower-quality submission by an established researcher would be accepted.
- Delays in publication
The thoroughness of the peer review process can lead to significant delays in publishing time. Research that was current at the time of submission may not be as current by the time it’s published. There is also high risk of publication bias , where journals are more likely to publish studies with positive findings than studies with negative findings.
- Risk of human error
By its very nature, peer review carries a risk of human error. In particular, falsification often cannot be detected, given that reviewers would have to replicate entire experiments to ensure the validity of results.
If you want to know more about statistics , methodology , or research bias , make sure to check out some of our other articles with explanations and examples.
- Normal distribution
- Measures of central tendency
- Chi square tests
- Confidence interval
- Quartiles & Quantiles
- Cluster sampling
- Stratified sampling
- Thematic analysis
- Discourse analysis
- Cohort study
- Ethnography
Research bias
- Implicit bias
- Cognitive bias
- Conformity bias
- Hawthorne effect
- Availability heuristic
- Attrition bias
- Social desirability bias
Peer review is a process of evaluating submissions to an academic journal. Utilizing rigorous criteria, a panel of reviewers in the same subject area decide whether to accept each submission for publication. For this reason, academic journals are often considered among the most credible sources you can use in a research project– provided that the journal itself is trustworthy and well-regarded.
In general, the peer review process follows the following steps:
- Reject the manuscript and send it back to author, or
- Send it onward to the selected peer reviewer(s)
- Next, the peer review process occurs. The reviewer provides feedback, addressing any major or minor issues with the manuscript, and gives their advice regarding what edits should be made.
- Lastly, the edited manuscript is sent back to the author. They input the edits, and resubmit it to the editor for publication.
Peer review can stop obviously problematic, falsified, or otherwise untrustworthy research from being published. It also represents an excellent opportunity to get feedback from renowned experts in your field. It acts as a first defense, helping you ensure your argument is clear and that there are no gaps, vague terms, or unanswered questions for readers who weren’t involved in the research process.
Peer-reviewed articles are considered a highly credible source due to this stringent process they go through before publication.
Many academic fields use peer review , largely to determine whether a manuscript is suitable for publication. Peer review enhances the credibility of the published manuscript.
However, peer review is also common in non-academic settings. The United Nations, the European Union, and many individual nations use peer review to evaluate grant applications. It is also widely used in medical and health-related fields as a teaching or quality-of-care measure.
A credible source should pass the CRAAP test and follow these guidelines:
- The information should be up to date and current.
- The author and publication should be a trusted authority on the subject you are researching.
- The sources the author cited should be easy to find, clear, and unbiased.
- For a web source, the URL and layout should signify that it is trustworthy.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
George, T. (2023, June 22). What Is Peer Review? | Types & Examples. Scribbr. Retrieved August 29, 2024, from https://www.scribbr.com/methodology/peer-review/
Is this article helpful?
Tegan George
Other students also liked, what are credible sources & how to spot them | examples, ethical considerations in research | types & examples, applying the craap test & evaluating sources, get unlimited documents corrected.
✔ Free APA citation check included ✔ Unlimited document corrections ✔ Specialized in correcting academic texts

ENG 102: English Composition II: Literary Analysis Assignment
- Library Research Help
- Literary Analysis Assignment
How to Locate Your Research Guide
- How to Locate Your English 102 Research Guide Step-by-step instructions on how to locate your ENG102 research guide. This document can be used to help anyone needing assistance with locating a research guide at Lawson State.
Library Literary Analysis Assessment (Fall 2022)
Below are the links to the assessment and survey for the "How to Locate a Literary Criticism" video tutorial.
Assessment :
- Literary Analysis Workshop Assessment (Spring 2023)
Survey :
- Literary Analysis Workshop Survey (Spring 2023)
What is the peer review process?
What is a Literary Criticism?
When you are tasked with locating a literary criticism , most often this is due to a class assignment in your literature or English class. To first understand your task, you must understand what a literary criticism is and how it is used.
A literary criticism is an in-depth analysis of a literary work such as a poem, novel, short story, or play. A literary criticism is usually in the form of an essay, has references, and is not an opinion piece. These articles are usually published in scholarly journals instead of popular magazines or newspapers.
In your English or literature class, you would use a literary criticism to support your analysis of a particular piece of literature. A literary criticism helps you to gain a better understanding or to provides you with a different perspective on a piece of literature.
A literary criticism is a secondary source, which examines or analyzes a particular work of literature. In your English or literature class, the primary text is the one you are writing your literary analysis on for your course assignment.
Databases for Literary Analysis Essay

Example of a Scholarly Criticism

Example :
In this article, researcher Asha Nadkami juxtaposes Charlotte Perkins Gilman's short story, The Yellow Wallpaper, against Bhurati Mukherjee's 1989 novel, Jasmine .
Citation :
Nadkarni, Asha. "Reproducing Feminism in Jasmine and 'The Yellow Wallpaper." Feminist Studies , vol. 38, no. 1, spring 2012, pp. 218+. Gale Literature Resource Center , link.gale.com/apps/doc/A293668229/GLS?u=avl_law&sid=bookmark-GLS&xid=7d85bec6. Accessed 30 Aug. 2022.
Accessed:
Gale's Literature Database
Supplemental Resources
- Holman Library's Literary Criticism Research Guide This research guide provides additional resources related to literary criticisms.
- North Hampton Community College: Finding a Literary Criticism Tutorial This in-depth research guides provides step-by-step instructions on identify and locating literary criticism. It also provides different resources where you can locate literary criticism within your library.
- << Previous: Library Research Help
- Next: MLA >>
- Last Updated: Jun 24, 2024 11:20 AM
- URL: https://lawsonstate.libguides.com/eng102
Academic Editing and Proofreading
- Tips to Self-Edit Your Dissertation
- Guide to Essay Editing: Methods, Tips, & Examples
- Journal Article Proofreading: Process, Cost, & Checklist
- The A–Z of Dissertation Editing: Standard Rates & Involved Steps
- Research Paper Editing | Guide to a Perfect Research Paper
- Dissertation Proofreading | Definition & Standard Rates
- Thesis Proofreading | Definition, Importance & Standard Pricing
- Research Paper Proofreading | Definition, Significance & Standard Rates
- Essay Proofreading | Options, Cost & Checklist
- Top 10 Paper Editing Services of 2024 (Costs & Features)
- Top 10 Essay Checkers in 2024 (Free & Paid)
- Top 10 AI Proofreaders to Perfect Your Writing in 2024
- Top 10 English Correctors to Perfect Your Text in 2024
- Top 10 Essay Editing Services of 2024
- 10 Advanced AI Text Editors to Transform Writing in 2024
Academic Research
- Research Paper Outline: Templates & Examples
- How to Write a Research Paper: A Step-by-Step Guide
- How to Write a Lab Report: Examples from Academic Editors
- Research Methodology Guide: Writing Tips, Types, & Examples
- The 10 Best Essential Resources for Academic Research
- 100+ Useful ChatGPT Prompts for Thesis Writing in 2024
- Best ChatGPT Prompts for Academic Writing (100+ Prompts!)
- Sampling Methods Guide: Types, Strategies, and Examples
- Independent vs. Dependent Variables | Meaning & Examples
Academic Writing & Publishing
- Difference Between Paper Editing and Peer Review
- What are the different types of peer review?
- How to deal with rejection from a journal?
- Editing and Proofreading Academic Papers: A Short Guide
- How to Carry Out Secondary Research
- The Results Section of a Dissertation
- Checklist: Is my Article Ready for Submitting to Journals?
- Types of Research Articles to Boost Your Research Profile
- 8 Types of Peer Review Processes You Should Know
- The Ethics of Academic Research
- How does LaTeX based proofreading work?
- How to Improve Your Scientific Writing: A Short Guide
- Chicago Title, Cover Page & Body | Paper Format Guidelines
- How to Write a Thesis Statement: Examples & Tips
- Chicago Style Citation: Quick Guide & Examples
- The A-Z Of Publishing Your Article in A Journal
- What is Journal Article Editing? 3 Reasons You Need It
- 5 Powerful Personal Statement Examples (Template Included)
- Complete Guide to MLA Format (9th Edition)
- How to Cite a Book in APA Style | Format & Examples
- How to Start a Research Paper | Step-by-step Guide
- APA Citations Made Easy with Our Concise Guide for 2024
- A Step-by-Step Guide to APA Formatting Style (7th Edition)
- Top 10 Online Dissertation Editing Services of 2024
- Academic Writing in 2024: 5 Key Dos & Don’ts + Examples
- What Are the Standard Book Sizes for Publishing Your Book?
- MLA Works Cited Page: Quick Tips & Examples
- 2024’s Top 10 Thesis Statement Generators (Free Included!)
- Top 10 Title Page Generators for Students in 2024
- What Is an Open Access Journal? 10 Myths Busted!
- Primary vs. Secondary Sources: Definition, Types & Examples
- How To Write a College Admissions Essay That Stands Out
- How to Write a Dissertation & Thesis Conclusion (+ Examples)
- APA Journal Citation: 7 Types, In-Text Rules, & Examples
- What Is Predatory Publishing and How to Avoid It!
- What Is Plagiarism? Meaning, Types & Examples
- How to Write a Strong Dissertation & Thesis Introduction
- How to Cite a Book in MLA Format (9th Edition)
- How to Cite a Website in MLA Format | 9th Edition Rules
- 10 Best AI Conclusion Generators (Features & Pricing)
- Top 10 Academic Editing Services of 2024 [with Pricing]
- 100+ Writing Prompts for College Students (10+ Categories!)
- Additional Resources
- Plagiarism: How to avoid it in your thesis?
- Final Submission Checklist | Dissertation & Thesis
- 7 Useful MS Word Formatting Tips for Dissertation Writing
- How to Write a MEAL Paragraph: Writing Plan Explained in Detail
- Em Dash vs. En Dash vs. Hyphen: When to Use Which
- The 10 Best Citation Generators in 2024 | Free & Paid Plans!
- 2024’s Top 10 Self-Help Books for Better Living
- The 10 Best Free Character and Word Counters of 2024
- Know Everything About How to Make an Audiobook
- Citation and Referencing
- Citing References: APA, MLA, and Chicago
- How to Cite Sources in the MLA Format
- MLA Citation Examples: Cite Essays, Websites, Movies & More
- Citations and References: What Are They and Why They Matter
- APA Headings & Subheadings | Formatting Guidelines & Examples
- Formatting an APA Reference Page | Template & Examples
- Research Paper Format: APA, MLA, & Chicago Style
- How to Create an MLA Title Page | Format, Steps, & Examples
- How to Create an MLA Header | Format Guidelines & Examples
- MLA Annotated Bibliography | Guidelines and Examples
- APA Website Citation (7th Edition) Guide | Format & Examples
- APA Citation Examples: The Bible, TED Talk, PPT & More
- APA Header Format: 5 Steps & Running Head Examples
- APA Title Page Format Simplified | Examples + Free Template
- How to Write an Abstract in MLA Format: Tips & Examples
- 10 Best Free Plagiarism Checkers of 2024 [100% Free Tools]
- 5 Reasons to Cite Your Sources Properly | Avoid Plagiarism!
- Dissertation Writing Guide
- Writing a Dissertation Proposal
- The Acknowledgments Section of a Dissertation
- The Table of Contents Page of a Dissertation
- The Introduction Chapter of a Dissertation
- The Literature Review of a Dissertation
- The Only Dissertation Toolkit You’ll Ever Need!
- 5 Thesis Writing Tips for Master Procrastinators
- How to Write a Dissertation | 5 Tips from Academic Editors
- The 5 Things to Look for in a Dissertation Editing Service
- Top 10 Dissertation Editing & Proofreading Services
- Why is it important to add references to your thesis?
- Thesis Editing | Definition, Scope & Standard Rates
- Expert Formatting Tips on MS Word for Dissertations
- A 7-Step Guide on How to Choose a Dissertation Topic
- 350 Best Dissertation Topic Ideas for All Streams in 2024
- A Guide on How to Write an Abstract for a Research Paper
- Dissertation Defense: What to Expect and How to Prepare
- Creating a Dissertation Title Page (Examples & Templates)
- Essay Writing Guide
- Essential Research Tips for Essay Writing
- What Is a Mind Map? Free Mind Map Templates & Examples
- How to Write an Essay Outline: 5 Examples & Free Template
- How to Write an Essay Header: MLA and APA Essay Headers
- What Is an Essay? Structure, Parts, and Types
- How to Write an Essay in 8 Simple Steps (Examples Included)
- 8 Types of Essays | Quick Summary with Examples
- Expository Essays | Step-by-Step Manual with Examples
- Narrative Essay | Step-by-Step Guide with Examples
- How to Write an Argumentative Essay (Examples Included)
- Guide to a Perfect Descriptive Essay [Examples & Outline Included]
- How to Start an Essay: 4 Introduction Paragraph Examples
- How to Write a Conclusion for an Essay (Examples Included!)
- How to Write an Impactful Personal Statement (Examples Included)
Literary Analysis Essay: 5 Steps to a Perfect Assignment
- Compare and Contrast Essay | Quick Guide with Examples
- Top AI Essay Writers in 2024: 10 Must-Haves
- 100 Best College Essay Topics & How to Pick the Perfect One!
- College Essay Format: Tips, Examples, and Free Template
- Structure of an Essay: 5 Tips to Write an Outstanding Essay
- 10 Best AI Essay Outline Generators of 2024
- The Best Essay Graders of 2024 That You Can Use for Free!
- Top 10 Free Essay Writing Tools for Students in 2024
Still have questions? Leave a comment
Add Comment
Checklist: Dissertation Proposal
Enter your email id to get the downloadable right in your inbox!
Examples: Edited Papers
Need editing and proofreading services.

- Tags: Academic Writing , Essay , Essay Writing
You need to interpret a piece of writing for a literary analysis essay. With the deadline quickly approaching, you don’t know where to begin! That’s exactly why we’ve explained how to write such an essay and provided multiple literary analysis essay examples.
Here’s a simple literary analysis essay definition: A personal interpretation of a piece of writing. It’s not just a summary or an explanation of a piece of writing but an argumentative take that highlights your take on a particular poem or story. This is evidenced by the support of quoted sections from the original piece.
Get your literary analysis essay perfectly edited to score high! Learn more
Here are the steps to write a literary analysis essay in detail:
1. Read and analyze the text
In order to understand how to start a literary analysis essay, you need to realize the importance of strong research. Before you begin writing your essay , make sure to thoroughly go through your text and take detailed notes. Observe and note the words used by the author, the structure and tone of the piece, the point of view, and so on.
The goal here is to build textual connections within and outside the text. Ask yourself the following questions:
- Are there logical connections to be derived from the structure, theme, or words used?
- Does the piece make any allusions to other works?
- Is this piece similar or different from the author’s other writings?
- Are there any thematic similarities between this work and others in the same time period?
- What have critics said about this text? Can it be useful for my argument?
Let’s take a deeper look at how to analyze a literary text:
A. Use of structure
While writing an essay , studying the structure of a text is an indispensable part of literary analysis. Authors and poets divide their texts into chapters, scenes, or stanzas, which may be deliberate and intentional. Pay close attention to the organization of the text to obtain clues into the author’s intention or to create your own arguments about it.
When analyzing novels or short stories, focus on the following details:
- What is the mechanism for the organization of chapters or sections?
- Does the story begin at the beginning or middle of the action?
- Is time in the text linear, cyclical, or fluid? What effect does this have on your perception of characters, story events, and the climax?
- What role does the climax play in the narrative?
When analyzing poems, ask the following questions:
- Is there a logic behind the organization of stanzas or verses in the poem?
- Does the poem follow a set meter and rhyme scheme?
- How does rhythm in the poem influence its tone and meaning?
A play is the most structured genre of writing. When analyzing, focus on the following aspects:
- What effect does the arrangement of acts and scenes have on the audience?
- How is dramatic irony used in the play?
- What methods does the playwright employ to bring about the plot twist, if one exists?
- Are there any red herrings that are explained later on in the play?
- Does the playwright make use of foreshadowing in their play?
B. Use of narrative voice
One of the most important aspects of a piece of writing is the point of view from which it is written. While going through your text you need to observe who “speaks” and the manner in which they do.
Is the narrator removed from the text or are they part of it? Are they narrating the events faithfully or distorting it according to their perspective? Does the main character of the story or poem break the fourth wall by directly addressing the reader?
Often, writers make use of distorted points of view recounted by an unreliable narrator. One such example is The Tell-Tale Heart by Edgar Allen Poe. In his short story, Poe delves into the mind of a highly disturbed individual who is fixated on an old man’s “vulture eye”. This distorted perspective can suggest a variety of literary analysis essay topics.
C. Use of language
While going through the text, focus on the language and tone used by the author. Try to answer the following questions as you analyze the writing:
- Are the sentences used simple or verbose?
- What is the tone of the piece?
- How has figurative language been used in the text, if at all?
- What do the sensory descriptors and imagery signify?
- Is there any paradoxical or peculiar use of words?
After making notes on the language structure, you can move on to the broader aspects of the piece such as the narrative voice.
Also read: Top 10 Essay Writing Tools in 2023 | Plan, Write, Get Feedback
2. Construct a strong thesis statement
A thesis statement for a literary analysis essay is the main point or argument made based on the analysis of a particular text. It is the base that gives your essay direction and keeps it from being an arbitrary assembly of events or a mere summary.
While deciding upon your thesis statement, it is a good idea to pick an argument that can be proven or disproven with the help of the information provided in the text.
Make sure that your thesis statement is a well-rounded argument and not simply a yes or no answer. Here are some examples of well-written and poorly-written thesis statements:
Romeo and Juliet is a literary classic that is based on the themes of love and betrayal.
The themes of love and betrayal are blatantly portrayed in Romeo and Juliet . Your thesis statement should be a nuanced and, at times, debatable take on the text under scrutiny.
Here’s a better example:
The nurse’s actions and decisions in Shakespeare’s Romeo and Juliet significantly contribute to the tragic deaths of the titular characters.
The following thesis statement examines the role of Juliet’s nurse and confidante. It discusses how the careless actions of the nurse resulted in the tragic death of the main characters.
Let’s consider one more thesis statement:
Edgar Allan Poe makes use of symbolism and repetition to enhance his poem The Raven .
Although the thesis statement describes important literary devices used in Poe’s poem, it does not include any argument that can be elaborated on or debated.
Here’s a more well-rounded example:
In Edgar Allan Poe’s poem The Raven , the repetition of the word “nevermore” serves as a haunting and symbolic refrain, representing the protagonist’s descent into despair.
The following thesis statement example focuses on the significance of the word “nevermore” in The Raven . Although the thesis statement also revolves around literary devices, the significance behind “nevermore” is interpreted with a specific approach. This creates an argument that can be elaborated on or contradicted.
3. Write well-organized body paragraphs
A literary analysis essay generally consists of three body paragraphs, along with an introduction and conclusion. However, the number of body paragraphs present varies from one essay to another. Understand the structure of a MEAL paragraph to write effective body paragraphs.
Each body paragraph begins with a topic sentence. This sentence details the aspect on which your body paragraph is based. Make sure that each body paragraph discusses only one aspect of your literary analysis essay.
Each topic sentence should be evidenced with the help of information present in the piece of writing. This information can be in the form of direct quotes, summaries, as well as paraphrases. It is important to ensure that these pieces of information are focused and relevant to the point you’re trying to make.
Each body paragraph is concluded with a transition that links to the next topic sentence. Here’s an example of an effective body paragraph:
- Topic sentence
- Evidence presented
- Transition sentence
The raven’s perch upon the bust of Pallas, the goddess of wisdom, enhances the symbolic significance of the word “nevermore.” In stanza 14, the speaker describes the raven’s positioning, stating, “Perched upon a bust of Pallas just above my chamber door.” This juxtaposition of the raven, a symbol of death and darkness, with the statue of wisdom, reinforces the irony and futility of the protagonist’s quest for answers. The symbol of the raven, paired with the recurring utterance of “nevermore,” serves as a constant reminder of the protagonist’s entrapment within his grief. The gloomy atmospheric setting along with a constant sense of despair heightens the overall feeling of hopelessness which contributes to the tragic mood of The Raven .
Also read: How to Write an Essay Outline: 5 Examples & Free Template
4. End with a powerful conclusion
Like all essay types, the conclusion of a literary essay analysis shouldn’t introduce any new arguments. Rather, this space should be used to emphasize the significance of your argument. This can be done by summarizing all the key aspects of your essay and linking them back to your main argument.
It’s a good idea to conclude your essay with the help of a powerful statement that creates an impression. This can include a quote by the author of the piece you’re analyzing or your own interpretation of the subject matter.
Here’s an example of a well-rounded conclusion:
- Updated thesis statement
- Summary of main points of the essay
- Concluding statement
As we can see, the repeated use of the word “nevermore” serves as a powerful symbol that encapsulates the protagonist’s descent into despair and his futile struggle to find solace or meaning in the face of loss. Through the relentless repetition of this word, Poe creates a sense of finality and negation that magnifies the protagonist’s torment, leaving him trapped in a cycle of despair. The raven, perched upon the bust of Pallas, further intensifies the symbolism, as it becomes an embodiment of the protagonist’s own tortured thoughts and emotions, denying him the wisdom and solace he yearns for. The poem’s dark and atmospheric setting adds to the overall mood, enhancing the emotional impact of the narrative. Together, these elements converge to create a chilling exploration of the fragility of the human psyche in the face of irrevocable loss.
Having written the body paragraphs and conclusion, you can construct an attractive title and introduction based on the content of the rest of your essay.
5. Write an impactful introduction
The introduction of your essay provides a quick overview of the direction it’ll follow. It may include a general theme present in your chosen piece of literature or your take on a particular aspect of the text.
Make sure to cite the name of the text in question along with the writer of the piece in your essay introduction . This will provide the readers with the necessary context for your essay. Your introduction can also include a commonly held interpretation of a piece of writing by the general public. This belief can either be substantiated or disproven by evidence present in the text.
Your introduction provides a synthesis of the main argument you’d like to present in your essay, also known as the thesis statement. You could also end with a brief overview of your essay by signposting the main topics you’d like to discuss in your essay.
Here’s an example of an ideal essay introduction:
- Opening sentence
- Background information
- Thesis statement
Edgar Allan Poe’s iconic poem, The Rave, is a masterpiece of gothic literature that delves into the depths of human emotions and the haunting presence of loss. Within this enigmatic work, Poe employs the repetition of a single word, “nevermore,” as a haunting and symbolic refrain. In this essay, we will explore how the repetitive use of “nevermore” serves as a profound symbol, representing the protagonist’s descent into despair and his futile struggle to find solace or meaning in the face of overwhelming loss.
6. Come up with a good title
The first thing that attracts the reader to your work is an attractive title. An effective title should be succinct and to the point, yet intriguing. An effective essay title consists of the name of the text you’re examining accompanied by the aspect you’ve analyzed.
Using the name of the text concerned without any alteration is simply not sufficient. You also have to put your own spin on it. The idea is to provide the gist of your essay in a single sentence. There are several ways in which you can do this.
Here are a few examples of effective literary essay titles:
- The dual nature of sin and redemption as portrayed in The Scarlet Letter
- The significance of “nevermore” in The Raven
- A warning against totalitarianism and surveillance presented in 1984
- The Great Gatsby : The illusion of the American dream
- Moby-Dick: Exploring the themes of obsession and fate
- The complexities of revenge and madness explored in Shakespeare’s Hamlet
- The Catcher in the Rye : A search for authenticity
- Frankenstein : The dangers of ambition and scientific progress
- Examining the link between social injustice and human resilience in The Grapes of Wrath
- Pride and Prejudice : Unveiling the social constructs of marriage
Literary analysis essay example
The following literary analysis essay example examines the role of Captain Arthur Hastings as an unreliable narrator in Agatha Christie’s last novel, Curtains. It explores how the personal biases of Hastings add a sense of mystery to the novel.
Examining Hastings’ Perspective in Agatha Christie’s Curtains
Agatha Christie’s novel Curtains presents readers with a captivating murder mystery, skillfully crafted to keep them guessing until the very end. The role of Captain Arthur Hastings, both a close friend and narrator of the story, is crucial in shaping the readers’ understanding of events. However, an analysis of Hastings’ character reveals that he is an unreliable narrator, prone to biases and limited perceptions. This essay explores the reasons behind Hastings’ unreliability and its impact on the reader’s interpretation of the narrative.
Hastings’ unreliability stems from his inherent subjectivity and personal biases. As an involved character in the story, he possesses preconceived notions about the suspects, events, and motives. This subjectivity can cloud his judgment and influence the information he chooses to reveal or withhold from the readers. His personal biases can lead to misinterpretations, creating a skewed version of events that may misdirect readers in their pursuit of the truth.
Another factor contributing to Hastings’ unreliability is his limited observations and perceptions. As a narrator, he can only provide insights into what he personally witnesses or is directly told by others. Consequently, his knowledge is restricted to the information available to him at any given moment. Hastings may overlook crucial details, misinterpret clues, or fail to grasp the significance of certain actions due to his limited perspective. This limitation can result in gaps or inaccuracies in the narrative, causing readers to form incomplete or incorrect conclusions.
Hastings’ emotional involvement and personal relationships further contribute to his unreliability. His close friendship with Hercule Poirot, for example, may lead him to downplay or overlook Poirot’s mistakes or biases. Additionally, Hastings’ emotional state throughout the investigation, whether it be fear, confusion, or loyalty, can impact his ability to objectively interpret events. Emotions can cloud his judgment and affect his narrative, potentially leading readers astray in their own deductions.
Agatha Christie’s choice to present Captain Hastings as an unreliable narrator adds an element of uncertainty and intrigue to the story. His subjectivity, limited observations, and emotional influences all contribute to his unreliability, shaping the readers’ understanding and interpretation of events. By questioning his version of the truth and scrutinizing his biases and perceptions, readers are encouraged to actively engage in the process of solving the mystery alongside the characters. The unreliability of his narration serves as a reminder that in the world of detective fiction, unraveling the truth requires careful consideration and a discerning eye.
Alongside offering expert essay editing services , it’s our duty to ensure that you have all the tools to improve your writing skills. Here are some resources you may find helpful:
- How to Write an Essay Header: MLA and APA Essay Headers
- Narrative Essay | Step-by-Step Guide with Examples
- Guide to a Perfect Descriptive Essay [Examples & Outline Included]
- Compare and Contrast Essay | Quick Guide with Examples
- Guide to Essay Editing: Methods, Tips, & Examples
Frequently Asked Questions
What is the purpose of a literary analysis essay, how to write a hook for an essay, what is the fundamental characteristic of a literary analysis essay, how to title a literary analysis essay, how long is a literary analysis essay.
Found this article helpful?
Leave a Comment: Cancel reply
Your email address will not be published.
Your vs. You’re: When to Use Your and You’re
Your organization needs a technical editor: here’s why, your guide to the best ebook readers in 2024, writing for the web: 7 expert tips for web content writing.
Subscribe to our Newsletter
Get carefully curated resources about writing, editing, and publishing in the comfort of your inbox.
How to Copyright Your Book?
If you’ve thought about copyrighting your book, you’re on the right path.
© 2024 All rights reserved
- Terms of service
- Privacy policy
- Self Publishing Guide
- Pre-Publishing Steps
- Fiction Writing Tips
- Traditional Publishing
- Academic Writing and Publishing
- Partner with us
- Annual report
- Website content
- Marketing material
- Job Applicant
- Cover letter
- Resource Center
- Case studies
- Rating Count
- Price (Ascending)
- Price (Descending)
- Most Recent
Peer review for literary analysis
Resource type.

Literary Analysis Peer Review Sheet

Peer Review and Feedback form for a Text / Literary Analysis Response Essay

Peer Review Writing Circles: Literary Analysis Essays

Peer Review Literary Analysis

Literary Analysis Essay - Peer Review Worksheet

Peer Review Slides - Literary Analysis Essays

Romeo and Juliet Essay Literary Analysis Unit w/ Lesson Plans, Rubric, Revision

Essay writing bundle for high school! Analytical / Literary Analysis Essay

Reading Skills & Analysis BUNDLE Lesson Practice with Literary Elements Devices

End Of Year Writing Review Argument Informative Narrative Literary Analysis

Editing or Peer Review Checklist for Writing ANY Lit Analysis Essay

Literary Analysis Essay Peer Editing Checklist

The Outsiders: Literary Analysis Essay on Theme

Literary Analysis Essay: everything you need & ready to print

Literary Analysis Graphic Organizer and Outline for High School Essay Writing

Digital Template One-Pager for Literary Analysis High School (Remote Learning)

Self-Editing Guide/Checklist for Literary Analysis Essay

SCAFFOLDED WRITING PACKET: Literary Analysis Body Paragraph Writing Process

Literary Analysis Essay - 5 Step Process (Editable)

A Christmas Carol Novel Study End of the Unit Final Essay & Peer Review |Dickens

Peer Interview Activity for Literary Analysis Essay (Thematic Essay)

Romeo and Juliet Literary Analysis 2- Assessment, Review , Essay Pre-Writing

Literary / Text Analysis Rubric

Literary Analysis of Irony in The Story of An Hour High School Distance Learning

- We're hiring
- Help & FAQ
- Privacy policy
- Student privacy
- Terms of service
- Tell us what you think
Loading metrics
Open Access
Peer-reviewed
Research Article
Perspectives on conducting “sex-normalising” intersex surgeries conducted in infancy: A systematic review
Roles Data curation, Formal analysis, Investigation, Methodology, Project administration, Writing – original draft, Writing – review & editing
* E-mail: [email protected] , [email protected]
Affiliation Department of Public Health and Primary Care, University of Cambridge, Cambridge, United Kingdom
Roles Data curation, Formal analysis, Investigation, Methodology, Writing – review & editing
Affiliation Faculty of Medicine, Nursing and Health Sciences, Monash University, Melbourne, Australia
Roles Writing – review & editing
Affiliation Department of Gender, Rights and Equity, World Health Organization, Geneva, Switzerland
Affiliation Department of Mental Health and Substance Use, World Health Organization, Geneva, Switzerland
Affiliation Department of Sexual and Reproductive Health and Research, UNDP-UNFPA-UNICEF-WHO-World Bank Special Programme of Research, Development and Research Training in Human Reproduction (HRP), World Health Organization, Geneva, Switzerland
Roles Conceptualization, Formal analysis, Supervision, Writing – review & editing
Roles Conceptualization, Data curation, Formal analysis, Supervision, Writing – review & editing
- Luke Muschialli,
- Connor Luke Allen,
- Evelyn Boy-Mena,
- Aiysha Malik,
- Christina Pallitto,
- Åsa Nihlén,
- Lianne Gonsalves

- Published: August 28, 2024
- https://doi.org/10.1371/journal.pgph.0003568
- Reader Comments
Children with intersex variations continue to be subject to elective, irreversible, “sex-normalising” surgical interventions, despite multiple human rights and legislative bodies calling for their prohibition. Our systematic review aims to understand how medical literature reports rationales for “sex-normalising” surgical interventions conducted in childhood, and how they are contextualised within the medical and social controversy surrounding such interventions. PubMed, EMBASE and CINAHL were searched for English language, peer-reviewed articles reporting primary data on elective, genital, “sex-normalising” surgical interventions conducted on individuals <10 years, published 01/07/2006-30/06/2023 (PROSPERO ID: CRD42023460871). Data on outcomes reported, rationale for the conduct and timing of interventions and acknowledgement of controversy were extracted. Narrative synthesis described rationales and controversy. Risk of bias was assessed using Johanna Briggs Institute Tools. 11,042 records were retrieved, with 71 articles included for analysis. One of the most common outcomes collected in included literature were cosmetic outcomes, primarily reported by surgeons or parents. 62.0% of studies reported no rationale for intervention timing, 39.4% reported no rationale for conduct and 52.1% acknowledged no controversy in intervention conduct. Rationales included parental desire for intervention, anatomical/functional/cosmetic reasons, and a perceived goal of aligning with sex assigned by surgical teams or parents. Controversies addressed included concerns about the quality of interventions, the ethics of intervention conduct and gendered and social considerations. “Sex-normalising” interventions are conducted based largely on rationales that were not adequately supported by evidence, a desire from parents and surgeons to match genital cosmesis typically ascribed to male and female bodies, and a parental desire for intervention conduct. Legislating and medical regulatory bodies should advocate for ending the conduct of irreversible, elective, “sex-normalising” interventions conducted without the full, free and informed consent of the person concerned, to promote and protect the highest attainable standard of health for people with intersex variations.
Citation: Muschialli L, Allen CL, Boy-Mena E, Malik A, Pallitto C, Nihlén Å, et al. (2024) Perspectives on conducting “sex-normalising” intersex surgeries conducted in infancy: A systematic review. PLOS Glob Public Health 4(8): e0003568. https://doi.org/10.1371/journal.pgph.0003568
Editor: Sualeha Siddiq Shekhani, Centre of Biomedical Ethics and Culture, PAKISTAN
Received: May 14, 2024; Accepted: July 26, 2024; Published: August 28, 2024
Copyright: © 2024 Muschialli et al. This is an open access article distributed under the terms of the Creative Commons Attribution License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Data Availability: All relevant data are within the paper and its Supporting Information files.
Funding: This review was conducted with the financial support of the UNDP-UNFPA-UNICEF-WHO-World Bank Special Programme of Research, Development and Research Training in Human Reproduction (HRP), a cosponsored programme executed by the World Health Organization (WHO) to LM, CLA, LG and AN. The funders had no role in study design, data collection and analysis, decision to publish, or preparation of the manuscript.
Competing interests: The authors have declared that no competing interests exist.
Introduction
Intersex is an umbrella term used to refer to individuals born with physical or biological sex characteristics (including sexual anatomy, reproductive organs and/or chromosomal patterns) that do not fit normative definitions of male or female bodies [ 1 ]. These congenital variations in sex characteristics, also known as differences/disorders of sex development (DSDs), are a large, heterogeneous group of reproductive, urogenital, chromosomal and/or hormonal congenital conditions, with the set of diagnoses lying within these umbrella terms varying across different settings and disciplines [ 2 , 3 ]. Some of these variations may be visible and identifiable at birth, while others may not be recognized until later in childhood, puberty and/or adulthood [ 1 ].
Many congenital variations in sex characteristics pose no threat to physical health, while others may necessitate medical or surgical intervention (i.e., to facilitate excretion or urination). However, standard surgical practice for decades has involved using a variety of elective (i.e., non-urgent) surgical procedures to attempt to ‘normalize’ ‘atypical’ traits in people with congenital variations in sex characteristics, striving for cosmetic, functional and anatomical outcomes that align more with those associated with ‘typical’ male or female bodies [ 4 ], referred to in this manuscript as “sex-normalising” interventions. These procedures frequently take place in infancy or early childhood, due in part to pervasive beliefs that early intervention will facilitate better psychological and/or physiological development, and alleviate anticipated personal and parental stress associated with the congenital variation in sex characteristics [ 5 – 8 ]. Treatment options may also involve hormonal therapy, mechanical procedures (e.g., neovaginal dilations), or surgical, hormonal, and mechanical interventions which take place in adolescence, all of which are outside the scope of this review.
The continued conduct of “sex-normalising” surgical interventions in infancy or early childhood is supported by clinical guidance such as the 2006 Consensus Statement on Management of Intersex Disorders , a statement that attempted to create recommendations for the long-term management, evaluation of, and future research into, congenital variations in sex characteristics [ 9 ]. This is despite a noted lack of evidence regarding the physical, mental, and social outcomes of infants with congenital variations in sex characteristics who have undergone such interventions, with an extant evidence-base primarily consisting of short case reports and cohort data with small sample sizes [ 2 , 4 ].
Evidence on patient preference for infant surgical intervention, despite still being used as a rationale for procedures, is also inconsistent. Although some patients retrospectively express a clear preference for, and satisfaction with, early surgical intervention [ 10 – 12 ], others who have undergone these surgeries share dissatisfaction with long-term outcomes, citing resultant distress and trauma associated with subsequent gender identity, compromised sexual function and pleasure, dissatisfaction with genital appearance and a reflective distress surrounding their compromised autonomy for interventions practiced before they were able to articulate consent for the procedure [ 13 – 23 ].
Human rights experts have recently raised serious concerns about the conduct of elective, irreversible, “sex-normalising” surgical interventions carried out in infancy and childhood. In October 2016, multiple UN human rights monitoring and accountability mechanisms (The international human rights treaty bodies and special procedures behind this joint statement were the UN Committee on the Rights of the Child, UN Committee against Torture, UN Committee on the Rights of People with Disabilities, UN Sub-Committee on Prevention of Torture and other Cruel, Inhuman or Degrading Treatment or Punishment, UN Special Rapporteur on torture and other cruel, inhuman or degrading treatment or punishment, UN Special Rapporteur on the right of everyone to the highest attainable standard of health, UN Special Rapporteur on violence against women, its causes and consequences, Special Representative of the UN Secretary-General on Violence against Children, African Commission on Human and Peoples’ Rights, Council of Europe Commissioner for Human Rights and the Inter-American Commission on Human Rights.) issued a joint statement highlighting the human rights violations associated with ‘medically unnecessary surgeries […] in an attempt to forcibly change [intersex infants’, children’s and adolescents’] appearance to be in line with societal expectations about female and male bodies’ and called on governments to ’prohibit harmful medical practices on intersex children, including unnecessary surgery and treatment without their informed consent’ [ 24 ]. Following this, several UN human rights treaty bodies, including the UN Committee on the Rights of the Child [ 25 ], as well as the World Health Organization (WHO) [ 26 ], have provided further advice, speaking out against medically unnecessary surgical interventions for infants with congenital variations in sex characteristics on the grounds of compromised bodily integrity and rights of the child. Recently, and for the first time, the UN Human Rights Council adopted a resolution calling on countries to enhance efforts to combat discrimination, violence and harmful practices against people with congenital variations in sex characteristics [ 27 ]. Simultaneously, intersex community groups have extensively campaigned against “sex-normalising” interventions on the same grounds, with some suggesting that the existence of such interventions also represent an elimination of intersex communities and an enforcement of strongly normative conceptualizations of gender and sex [ 28 ]. The collective impact of advocacy groups and human rights monitoring bodies has been reflected in a growing wave of national and sub-national legislative change restricting the practice of elective genital surgery conducted on children, focusing on the protection of children’s physical integrity and the prohibition of surgical intervention for infants and children with congenital variations in sex characteristics too young to participate in decision-making [ 29 ].
Both a 2016 Global Disorders of Sex Development Update since 2006 publication and a 2018 European publication, Caring for Individuals with a Difference of Sex Development , emphasise the need for clinicians to consider the ethical implications of conducting “sex-normalising” surgical interventions, and discuss the postponing of genital surgery until an individual is old enough to understand the intervention and participate in decision-making [ 2 , 4 ]. Despite this, there is little evidence to suggest that the prevalence of, or rationales for conducting, “sex-normalising” surgical interventions on individuals too young to consent has changed in recent years [ 30 , 31 ]. Understanding the rationale behind the continued practice of “sex-normalising” surgical interventions and how clinicians acknowledge and contextualise the controversial nature of the interventions they are practicing is necessary for identifying misconceptions in practice, and designing policy and interventions that target common drivers of continued, early surgical procedures.
Our review aims to understand the extent to which the extant medical literature is reporting rationales for elective, “sex-normalising” surgical interventions conducted in infancy and childhood, what these rationales are, and how they are contextualised within the social, medical, and political controversy surrounding “sex-normalising” interventions for people with congenital variations in sex characteristics.
Search and screening
Our review was compliant with PRISMA Reporting Guidelines [ 32 ] (see S1 text ), and is registered with PROSPERO (CRD42023460871).
On 30/06/2023, PubMed, EMBASE and CINAHL were searched for relevant articles published between 01/07/2006-30/06/2023, using search terms derived from previous reviews, recommendations from field experts and terminology from the International Classification of Diseases, Version 11 (ICD-11). The search start date aligns with the year of publication of the 2006 Consensus Statement on Management of Intersex Disorders [ 9 ].
S2 Text reports our search strategy. One search filter captured medical and public health terms that covered intersex as an umbrella term as well as individual congenital variations in sex characteristics that are generally identified in infancy or early childhood (as opposed to during puberty or adulthood). A second search filter captured general surgical terms as well as specific procedures associated with genital surgery for persons with congenital variations in sex characteristics [ 4 ]. English language restrictions were applied due to the risks of losing the complex nuances of surgical rationale in translation. A final search filter attempted to exclude: animal studies; commentaries, letters, and editorials; studies covering gender-affirming care surgeries; studies focusing on adolescence or young people over the age of 10 years.
Title/abstract and full-text screening was carried out by LM and CLA. LG independently screened a random sample of 10% of full texts to ensure consensus between reviewers. Screening was conducted in the systematic review management software, Covidence [ 33 ].
Inclusion and exclusion criteria
Peer-reviewed journal articles reporting primary data on elective, genital, “sex-normalising” surgical interventions conducted before the age of 10 years were included. This age cut-off was selected to align with the WHO’s definition of adolescence (ages 10–19 years) [ 34 ]. Inclusion decisions regarding surgical interventions were guided by the Gardner and Sandberg terminology of ‘urgent’ vs ‘elective’ surgery, with ‘urgent surgeries’ referring to those "performed promptly to avoid life-threatening circumstances or to prevent permanent disability”, while ‘elective surgeries’ include “those that address non-urgent issues” [ 35 ].
The following exclusion criteria were developed:
- Malignancy . Articles that cited malignancy as their rationale for conducting surgeries were excluded. Some individual congenital variations in sex characteristics are associated with increased risk of germ cell tumours, which is sometimes cited as a rationale for surgical intervention, despite the general malignancy risk associated with congenital variations in sex characteristics being debated [ 36 , 37 ]. However, for this review, it was thought that the potential for malignancy as perceived by clinicians and presented to parents/guardians, would, in the eyes of concerned parties, change the suggested surgery from being considered ‘elective’ to ‘urgent’. Whether surgical intervention due to the potential risk of malignancy was recommended for the specific congenital variation in sex characteristics in the 2006 Consensus Statement on Management of Intersex Disorders [ 9 ], which was the last statement to tabulate malignancy risk by individual variation, was recorded, and addressed in the discussion.
- Urinary incontinence . Studies citing preserving urinary continence, or studies citing functional urological goals (e.g., removing urethral obstruction), as their rationale were excluded, as these interventions were deemed to be non-elective [ 35 ]. Studies whose stated urological goals were intended to bring an individual in line with a perceived normative social behaviour (e.g., surgery to allow a boy to urinate standing up rather than sitting down) were included.
- Age. Studies in which it was unclear if all participants were under 10-years-old (i.e., age range was not provided), or studies which reported outcomes for a combination of individuals aged above and below 10-years-old without segregating outcomes, were excluded.
- No patient outcome data . Studies that collected no patient outcomes (e.g., studies focusing on surgical equipment use, histological studies) were excluded.
- Hypospadias, epispadias or cryptorchidism . Studies addressing hypospadias, epispadias or cryptorchidism that did not present these variations as congenital variations in sex characteristics or did not investigate them as part of an established congenital variation in sex characteristics were excluded due to debate among the medical community over their status as congenital variations in sex characteristics.
- Primary focus not “sex-normalising” surgical interventions. Studies that reported patients who had previously received a “sex-normalising” intervention but did not report the outcomes of or rationale for that surgery were excluded.
- Non-intersex populations . Studies that reported interventions that could be classed as “sex-normalising” but were administered to patients both with and without (e.g., transgender and gender diverse patients) congenital variations in sex characteristics without segregating outcomes for individuals with congenital variations in sex characteristics, were excluded.
- Reviews . Relevant systematic and scoping reviews were excluded but studies included in the reviews were screened against our inclusion criteria as part of a secondary search strategy.
Data extraction
Data extraction was conducted in Covidence [ 33 ], using a data-extraction table constructed by LM. LM and LG independently extracted, with CLA extracting a random sample of 25% of studies. In addition to bibliometric data (e.g., author, year of publication), the following data were extracted:
- Surgical outcomes . In line with the recommendations for data collection on long-term surgical outcomes for individuals with congenital variations in sex characteristics in the 2018 publication Caring for Individuals with a Difference of Sex Development [ 2 ] , we recorded if studies reported: complication rates, success rates, cosmetic outcomes, quality of life, sexual functioning, urogenital outcomes, sexuality/gender assignment, re-evaluation, fertility outcomes, social and psychosexual adjustment, mental health, social participation and parental outcomes. The precise and detailed categorisation of long-term outcome reporting used in the 2018 publication was deemed most appropriate for tabulating outcomes, rather than the 2006 Consensus Statement on Management of Intersex Disorders [ 9 ] or the 2016 Global Disorders of Sex Development Update since 2006 [ 4 ].
- Rationale . We recorded whether studies provided a rationale for conducting the surgical intervention, as well as rationale for the timing of the surgery. Rationales were extracted verbatim, alongside any work cited by authors when justifying rationale.
- Acknowledgement of controversy . We extracted verbatim text from studies that acknowledged the social, political, cultural, medical, ethical and/or surgical controversy surrounding the intervention they were conducting, as well as any work cited by authors when discussing this controversy.
Quality assessment was conducted independently by LM and CLA using the Joanna Briggs Institute’s instruments for Quality Assessment [ 38 ], with consensus reached through discussion. As no syntheses of outcomes were conducted, and rationale and controversy reporting were deemed to be independent of manuscript quality, manuscripts were not excluded on the basis of low quality.
Data analysis
Descriptive statistics were used to present the number of studies reporting each of the aforementioned outcomes. Qualitative, verbatim data on rationale and controversy was analysed using a narrative synthesis with an inductive approach. LM, LG and AN independently reviewed data to identify codes which addressed commonly occurring themes. LM, LG, and AN met to discuss and agree upon these high-level themes, after which LM independently coded all articles, discussing and refining emerging subthemes with LG and AN.
Throughout the narrative synthesis, the names of congenital variations in sex characteristics used by study authors will be used to avoid unintentional change in diagnosis through misinterpretation by the authorship team. These terms may not always be the accepted term within the intersex or medical communities.
Justifications and rationales for surgical intervention are presented in the narrative synthesis as presented by study teams, regardless of the accuracy of the assumptions stated. The presentation of such rationales does not represent an endorsement of their validity, and the accuracy of stated rationales is explored in the discussion.
Our search yielded 11,042 records, with 6,963 undergoing title/abstract screening after de-duplication. Following full-text screening of 1,649 records, 70 met all inclusion criteria and underwent data extraction. One further study was identified from searching systematic, scoping and literature reviews identified from the search ( Fig 1 ). S2 Text details the full search results from each database.
- PPT PowerPoint slide
- PNG larger image
- TIFF original image
https://doi.org/10.1371/journal.pgph.0003568.g001
Of the 71 studies in the final sample, 73.2% were case studies or case series (n = 52) and 26.8% were cohort studies (n = 19). Countries publishing included studies were India (n = 11; 15.5%), United States of America (n = 7; 9.9%), Brazil (n = 6; 8.5%), Türkiye (n = 5, 7.0%), Japan (n = 4; 5.6%), Algeria (n = 3; 4.2%), United Kingdom of Great Britain and Northern Ireland (UK), Netherlands, Pakistan, Romania, Egypt, Italy (n = 2; 2.8%, respectively), Sweden, Portugal, Republic of Korea, Iran (Islamic Republic of), Canada, Saudi Arabia, Spain, Finland, France, Germany, Indonesia, Argentina, Uganda, Nigeria, China, Poland, North Macedonia, Australia, Iraq, Belgium, Colombia, Kuwait, Syria, Bangladesh, Switzerland and Uzbekistan (n = 1; 1.4%, respectively). Included studies investigated a range of congenital variations in sex characteristics, including 29.6% of studies reporting on congenital adrenal hyperplasia (CAH, n = 21), 15.5% on diphallia and ovotesticular DSD (n = 11, respectively), 8.5% on persistent Mullerian duct syndrome (PMDS, n = 6), 5.6% on mixed gonadal dysgenesis (MGD, n = 4) and 4.2% Mayer-Rokitansky-Küster-Hauser (MRKH) syndrome and partial androgen insensitivity syndrome (PAIS, n = 3, respectively). Table 1 reports study characteristics. Quality of studies was generally low, with limited description of patient demographics, surgical interventions, and outcomes ( S1 Table ).
https://doi.org/10.1371/journal.pgph.0003568.t001
Outcomes measured in the literature
Fig 2 is a representation of the outcomes reported in included articles, categorised in line with the recommended reporting outcomes in the 2018 publication Caring for Individuals with a Difference of Sex Development [ 2 ]. Fig 2 also indicates which articles reported rationales for the conduct or timing of surgery, and those that acknowledged controversy. The most common outcomes collected in included literature were cosmetic outcomes, primarily reported by surgeons or parents, complication rates and urogenital outcomes. There was a notable lack of validated measures used by studies when assessing any surgical outcome, particularly cosmetic, and no studies collected any data on child quality of life or parental outcomes (i.e., parental mental health).
https://doi.org/10.1371/journal.pgph.0003568.g002
Rationales provided for conducting “sex-normalising” procedures and their timings
Four codes were inductively identified to categorise the rationales for “sex-normalising” procedures: Anatomical/Functional/Cosmetic (used in 50.7% of studies for either conduct or timing of intervention; n = 36), Perceived Goal of Aligning with Assigned Sex (39.4%; n = 28), Parental Desire (19.7%; n = 14), Belief of Best Practice (9.9%; n = 7) and Access (1.4%; n = 1). 33.8% of studies provided no rationale for the timing or conduct of “sex-normalising” interventions (n = 24).
Anatomical/functional/cosmetic.
Studies providing anatomical/functional/cosmetic reasons as a rationale for the timing or conduct of procedures investigated CAH (n = 17), diphallia, MGD (n = 3, respectively), PMDS, MRKH syndrome, Herlyn-Werner-Wunderlich syndrome, unspecified DSDs, PAIS (n = 2, respectively), genital ambiguity with high vaginal confluence, true hermaphroditism, genital ambiguity, 5-alpha reductase deficiency, ovotesticular syndrome, ovotesticular DSD, perineal hypospadias in DSD, persistent cloaca and 46, XX DSD (n = 1, respectively).
Rationale for conducting procedure . Cosmetic rationalisations for intervention were primarily based around the goal of achieving a ‘normal’ external genital appearance, corresponding with the sex proposed for children by the surgical team or parents [ 5 – 8 , 39 – 57 ]. This was sometimes done through critically presenting ambiguous genitalia, labelling them as ‘ugly’ [ 44 ] or something to ‘correct’ [ 53 ]. Cosmetic goals were generally unspecific, with authors striving for cosmetic results that were ‘satisfactory’ [ 54 , 57 ], ‘aesthetically pleasing’ [ 49 ], ‘normal’ [ 8 , 50 , 51 ], ‘good’ [ 52 ], ‘natural-looking’ [ 47 ], ‘favourable’ [ 55 ] or ‘typical’ [ 56 ]. Improved cosmesis, determined primarily by parents or surgeons ( Fig 2 ), was perceived by surgical teams to be linked to improved psychosocial outcomes such as anticipated improved parent-child attachment, reduced stigma or psychological distress, or perceived improvements in developments of gender identity [ 6 , 43 ].
Anatomically, surgical interventions were proposed as a way to prevent perceived incorrect virilisation of children and to align genitalia with the perceived ‘typical’ anatomy of the sex proposed by parents or surgeons [ 5 , 7 , 43 , 58 , 59 ]. Studies often articulated this by proposing interventions as a way of resituating anatomical structures to their ‘typical’ position [ 54 , 60 ]. As with cosmetic outcomes, goals were unspecific [ 61 ], with some teams describing the results they were striving for as ‘satisfactory’ [ 8 , 49 , 50 , 62 ]. Preventing downstream complications associated with ambiguous genitalia, such as endometriosis in Herlyn-Werner-Wunderlich Syndrome [ 63 ], was also cited as anatomical rationale for intervention conduct. Anatomical justifications were also used to select and justify the type of procedure being offered, such as one surgical team electing for ‘conservative’ approaches to minimise tissue removal for children who do not yet have definitive gender identity [ 64 ]. There was a notable impression by some authors that anatomical goals were secondary to aforementioned cosmetic rationales [ 50 ].
Many functional rationales were unspecific and subjective, including achieving ‘satisfactory’ [ 57 ], ‘good’ [ 8 , 52 ], ‘proper’ [ 40 ], ‘typical’ [ 56 ], ‘favourable’ [ 55 ] or ‘desirable’ [ 53 ] functional outcomes. More specific functional goals included achieving sexual function, including the prospect of ‘successful’ future intercourse (with the implication that sexual intercourse constituted penis-in-vagina, penetrative sex) [ 42 , 45 , 48 ] and achieving sexual arousal [ 5 , 41 , 44 , 50 ], menstruation [ 5 , 42 , 43 ] and protection of fertility [ 5 , 62 ]. Follow-up times for studies were often not long enough to be able to reliably confirm these functional goals ( Table 1 ). One study suggested a recent shift in prioritisation by global surgical teams towards protecting sexual satisfaction and sensate genital tissues in interventions [ 44 ]. There were also notable instances in which authors recognised uncertainty surrounding the functional impact of interventions, with articles suggesting post-intervention genitalia may be ‘more natural looking, and possibly functioning [emphasis added]’ [ 47 ] and that interventions ‘ may facilitate sexual intercourse [emphasis added]’ [ 45 ]. Similar to anatomic rationales, some authors implied functional outcomes were secondary to the cosmetic results they desired [ 46 , 50 ].
Rationale for timing of procedure . Cosmetic rationalisations for early intervention were often identical to those justifying the conduct of procedures, with no clear distinction articulated on the relative benefits of conducting these interventions in infancy. Some studies argued that the long-term psychological impact of the appearance of ambiguous genitalia is greater if interventions are not conducted early, without citing any recommendations or wider literature justifying this [ 6 , 39 ]. Other studies suggested that better compliance from patients and a lack of recollection in adulthood should justify early conduct of interventions [ 55 ]. Anatomical justifications for early surgery were more detailed, centring around the argument that early conduct is associated with better surgical outcomes. Several studies suggested that increased oestrogen exposure in the first month of life will provide better vascularised tissue and thicker walls of vaginal tissue [ 7 , 55 ], with other studies providing alternate developmental anatomical justifications, such as undeveloped penile circumflex arteries in infants leading to reduced risks of intra-operational bleeding (an uncited justification) [ 44 ]. Early age was also suggested to be the most appropriate time for preventing a range of complications that could have life-long effects [ 61 , 63 , 65 , 66 ]. Studies also suggested general higher success rates of operations conducted in infancy, without expanding on the specificities of this [ 67 ]. “Sex-normalising” interventions in infancy were also rationalised in infants requiring multiple surgeries. For example, one study suggested the benefits of concurrently performing vaginal reconstruction in a child with MRKH syndrome who incidentally had an anorectal malformation, with the justification that scarring of the urinary tract and rectum from anorectal reconstruction in this case may make vaginoplasty more difficult in later life [ 68 ]. Early intervention was also suggested as a way to prevent anticipated incorrect virilisation and puberty associated with retained gonads, the justifications for which were uncited [ 62 , 69 ]. Interestingly, one included study initially promoting early surgical intervention changed their mind following their study, moving to advocating for delaying intervention until puberty, with the anatomical justification that post-pubertal genital skin is more robust than the introital skin of infants [ 7 ]. Functional justifications for early intervention centred around the fact that early surgery will more effectively achieve desired function outcomes [ 61 ], including maintaining reproductive potential [ 63 ] and metabolic development [ 62 ].
Perceived goal of aligning with assigned sex.
The 28 studies reporting a perceived goal of aligning with an assigned sex as a rationale for the timing or conduct of procedures investigated CAH (n = 14), ovotesticular DSD (n = 4), 5-alpha reductase deficiency, MGD (n = 2, respectively), MRKH syndrome, true hermaphroditism, unspecified DSDs, ambiguous genitalia and 46, XX DSD (n = 1, respectively).
Rationale for conducting procedure . Rationalising procedures through pursuing a binary assigned sex for infants manifested in several ways. Anatomically, articles cited an intention to use interventions to create ‘normal’ external genitalia corresponding with the assigned sex of the infant by parents or surgeons [ 7 , 8 , 40 , 42 – 44 , 70 , 71 ] or to remove genitals unconcordant with the sex assigned to infants [ 7 , 65 , 70 – 73 ]. Some articles went further than this and identified interventions as a way to manifest the assigned sex (and subsequently, gender identity) chosen for the infant [ 5 , 74 ], suggesting interventions could ‘ create anatomical […] female gender [emphasis added]’ [ 58 ] or ‘ convert to the male sex [emphasis added]’ [ 75 ]. Facilitating psychosocial adjustment through conforming to a binary sex was also cited as an ethical motivation for conducting interventions [ 43 , 45 , 76 ], based on the assumption that genital appearance influences the development of the sexual psyche [ 39 ]. Teams also suggested that intervention could achieve certain sexual orientations and sexual development associated with the assigned sex [ 62 ], with one study citing hysterectomy and vaginectomy in CAH patients as a way to provide ‘satisfactory male gender identity and heterosexual orientation’ [ 62 ], and another suggesting intervention would facilitate the infant becoming a ‘functional member of the society’ [ 77 ].
Rationale for timing of procedure . The key rationalisation of early intervention timing when enacting the perceived goal of aligning with an assigned sex was the assumption that earlier intervention will more effectively facilitate gender identity development in line with sex assigned to a child by parents or surgeons, and limit psychological distress associated with an ambiguous sex [ 5 , 6 , 41 , 42 , 46 , 62 , 70 , 74 ]. One study extends this to suggest that early intervention will facilitate healthy body image development, a suggestion that did not cite any recommendations or relevant literature [ 39 ]. Some rationales relied on a belief that gender identity formation occurs in early life and can be strongly influenced by environmental surroundings [ 39 , 78 ]. Others cited early intervention as key for preventing psychological distress, without detailing the specific reason or evidence-base as to why early intervention is protective against this [ 8 , 44 ]. One study cites early intervention as an important tool to prevent societal barriers related to assigned sex for people with congenital variations in sex characteristics, specifically highlighting the complicated sports life in female athletes with 5-alpha reductase deficiency [ 79 ].
Parental desire.
The 14 studies reporting parental desire as a rationale for the timing or conduct of procedures investigated CAH (n = 10), ovotesticular DSD (n = 3) and 5-alpha reductase deficiency (n = 1). Both anticipated (n = 11) and vocalised parental desire (n = 4) were used as rationales.
Rationale for conducting procedure . Several articles predicted that external genital appearance that did not match conventional conceptions of male or female bodies would increase parental anxiety, distress and embarrassment, and used mitigating this as a justification for intervention [ 7 ]. One study specifically identifies the anticipated parental embarrassment surrounding a large clitoris in a child with CAH as a rationale for intervention [ 39 ]. Articles also assumed that parental acceptance and parent-child attachment would be improved through surgical intervention, despite often citing no relevant literature or discussions with family to justify this [ 6 ]. Surgical teams also articulated a difficulty in navigating voiced parental distress. Two surgical teams report going against their own recommendation to delay treatment due to intense parental desire for early intervention [ 40 , 78 ]. Parental desire was not only expressed for surgical intervention, but also for the assigned sex of their child. One study reported a strong parental preference to raise their child with ovotesticular DSD as a girl, which was then used as a rationale for conducting reconstructive vaginoplasty [ 80 ].
Rationale for timing of procedure . Some articles anticipated that specifically early reconstruction would alleviate anticipated psychological distress in parents [ 7 , 8 , 41 ], improve parental attachment [ 69 , 70 ] and increase parental comfort [ 62 ]. One study cites parents asking for early orchiopexy for their child with ovotesticular DSD before they began school to ensure wellbeing within the family, school and wider society [ 71 ]. In some cases, authors acknowledged that conducting early intervention was going against current global trends towards delaying intervention, but used strong parental desire in their local context to justify this. For example, one study cited parental anxiety specifically resulting from their sociocultural context as reason to complete the procedure as soon as possible [ 69 ]. Ethical justifications relating to preventing parental harm were also used to justify early intervention, with one study stating the birth of a child with ambiguous genitalia is a ‘tragedy’ for parents and thus ‘prolonging this suffering’ is morally unjustifiable [ 81 ].
Belief of best practice.
The 7 studies reporting belief of best practice as a rationale investigated CAH (n = 5), unspecified DSDs and ambiguous genitalia (n = 1, respectively).
Rationale for conducting procedure . All included studies citing clinical documentation to justify interventions cite the 2006 publication, Consensus Statement on Management of Intersex Disorders [ 9 ], referencing its recommendations to conduct surgical interventions in cases of severe virilisation, with the goal of not only improving cosmesis but also future sexual function [ 6 , 41 , 54 , 67 ].
Rationale for timing of procedure . Studies similarly cited the 2006 publication, Consensus Statement on Management of Intersex Disorders [ 9 ] when justifying early intervention in cases of severe virilisation [ 6 , 41 ], as well as citing clinical practice guidelines from the Endocrine Society [ 40 , 43 , 67 , 82 ] and recommendations from a range of government health authorities [ 45 , 83 ].
One study from the UK investigating CAH reported a logistic issue justifying the timing of infant genital surgery [ 78 ]. Despite teams advocating delayed intervention to parents, an imminent move by the family to their country of origin led the clinical team to elect to conduct the intervention in their specialist unit rather than risk the intervention being conducted in non-specialist facilities at a later date.
No rationale.
44 studies provided no rationale for timing of surgery, 28 no rationale for the conduct of surgery, and 24 studies no rationale for either. These studies providing no rationale for either timing or conduct investigated diphallia (n = 8), PMDS, ovotesticular DSD (n = 4, respectively), CAH, transverse testicular ectopia(n = 3, respectively), gonadal dysgenesis (n = 2), 5-alpha reductase deficiency, 45,X/46, XY DSD, Antley-Bixler syndrome, PAIS, severe hypospadias and microphallus, sex chromosome mosaicism and Herlyn-Weber-Wunderlich syndrome (n = 1, respectively)
Acknowledgement of controversy
47.9% of studies (n = 34) acknowledged controversy surrounding the interventions they were reporting. Three codes were developed to describe studies’ acknowledgment of the controversy surrounding “sex-normalising” surgical interventions: controversy surrounding the quality and standards of care (n = 29), controversy surrounding the cultural, gender and social well-being implications of interventions (n = 18) and controversy surrounding the ethics of the procedure (n = 15).
Standards of care and quality.
There was extensive debate in included studies addressing concerns about the quality of interventions, specifically highlighting a lack of information about long-term outcomes of the surgery [ 42 , 43 , 55 , 60 , 64 , 84 ], harms caused by the surgery [ 6 , 13 , 40 , 43 , 56 , 84 ], lack of evidence on the number of operations required [ 7 , 39 , 43 ] and contention about intervention timing [ 7 , 8 , 39 , 40 , 42 , 43 , 53 , 55 , 62 , 64 , 68 , 71 , 74 , 76 , 81 ]. Studies navigated these controversies in different ways. Some authors introduced the ethical debate surrounding interventions, and went on to dismiss the validity of these concerns and continue with the intervention regardless [ 60 , 62 , 68 , 85 ]. Several studies also explored concerns about intervention quality, but continued with various levels of accommodations for these controversies, including leaving surgical decision-making up to expertise of the surgical team [ 7 , 55 ], changing surgical procedure [ 5 , 40 , 42 , 43 , 53 , 64 , 81 , 86 ], individualising care [ 87 ] or providing psychological support to parents and children [ 71 , 75 ].
Culture/gender/social well-being.
Studies that addressed controversies surrounding the cultural, gender and social considerations of interventions introduced this debate through discussing the age of gender identity and sexual development, largely suggesting that by 2–3 years of age, children may be able to correctly label themselves of a certain gender, thus justifying intervention before this age [ 39 , 78 ]. Some studies recognised that controversies surrounding sex determination were increasing [ 7 ], particularly with concerns around higher prevalence of gender dysphoria among individuals with congenital variations in sex characteristics due to assignment of sex not matching future gender identity [ 42 , 64 , 69 ]. Often these controversies were dismissed through authors citing previous experience or small-scale qualitative evidence citing low levels of gender-related regret in adults having undergone infant genital surgery [ 64 , 78 ]. The rights of the child and perceived rights of parents also pervaded in these debates, with authors debating the gender preferences of families and the future gender identity of individuals with congenital variations in sex characteristics [ 46 , 71 , 73 , 75 ]. In addition to the aforementioned ways of navigating these controversies, such as offering patient-centred, multidisciplinary, individualised care for patients [ 7 , 46 , 64 , 71 ], studies also cited the possibility of a sex reversal later in life to rationalise controversial decisions to undergo procedures [ 71 , 74 , 79 ] or recommended psychological support for children who develop gender dysphoria from incorrect sex assignment from surgeons or parents post-intervention [ 69 , 75 ]. Authors also justified intervention in the face of these controversies by suggesting conservative surgery could balance future risks of gender dysphoria while protecting children from growing up in non-accepting environments [ 64 , 71 ].
A range of ethical controversies were acknowledged by included studies, primarily concerning the ability to provide informed consent for an irreversible intervention in infancy, and the interventions’ implied impact on cosmesis and gender identity [ 40 , 42 , 53 , 64 , 69 , 78 ]. Some studies further extend this debate to discuss the relative rights of the individual and the perceived rights of parents/guardians to request such intervention [ 46 , 55 , 74 , 81 ]. There is a recognition in some articles about a changing trend in the ethical approach to “sex-normalising” interventions, suggesting a global trend towards prioritising rights of the individual and postponing interventions [ 46 , 71 ]. These ethical controversies were navigated in different ways. Often ethical concerns were considered but not explored or integrated into decision-making [ 86 , 88 ]. The aforementioned surgical, functional, and anatomical rationales are also used by authors as considerations that overwhelm the ethical concerns of interventions, despite many concurrently noting that evidence on the relative efficacies of early and late surgery are lacking [ 40 , 53 , 55 , 74 ]. Notably, one team changed their recommendations to promote later intervention after their study, citing ethical concerns arising when considering high complication rates and low patient satisfaction with early intervention [ 42 ]. Placement of the global ethical debate within the context teams were working was also used to rationalise why teams found it appropriate to continue to conduct interventions, primarily suggesting that perceived rights of parents overwhelm the rights of the child in certain settings [ 46 , 69 , 74 , 75 ]. Other studies introduced ethical controversies surrounding interventions but rationalised their conduct through providing individualised care to patients from a multidisciplinary team and providing psychological counselling to those involved [ 69 , 71 ]. Some studies adapted their interventions based off of ethical concerns about irreversibility [ 64 ], with authors of one diphallia study promoting early surgery using a technique that did not remove penile tissue as a way to (in their view) address ethical concerns surrounding irreversibility [ 86 ]. One study adapted their study to focus on vaginoplasty rather than clitoroplasty in their report on a child with CAH to incorporate ethical concerns, due to vaginoplasty being ‘less debated’ in their setting [ 89 ].
This manuscript reports the findings of the first systematic review investigating the rationales, outcomes and controversies surrounding elective, “sex-normalising” interventions for infants with congenital variations in sex characteristics. Included articles were largely case reports, matching previous observations about the extant literature [ 2 , 4 ]. Among a geographically diverse set of articles, we noted outcome reporting that did not align with recommended reporting guidance. Rationales reported by surgical teams both concerning the conduct of interventions and their timings were heterogeneous across included studies, but broadly included anatomical/cosmetic/functional rationales, a perceived desire of aligning with a sex assigned by surgeons and parents, parental desire, and a belief of best practice. Studies acknowledged controversies surrounding the quality of interventions, cultural, gender and social considerations, and the ethics surrounding surgeries, while demonstrating different ways of integrating these controversies into their rationale for the continued justification of surgical intervention. 62.0% of studies reported no specific rationale for intervention timing, 39.4% reported no rationale for conduct and 52.1% acknowledged no controversy in the interventions they were conducting, implying that in some settings these surgical interventions remain accepted, common practice.
Cosmesis emerged as an important rationale for the conduct of interventions, as well as being one of the most commonly reported outcome measures collected in included articles. There was notable subjectivity in the reporting of cosmesis, with subjective, descriptive terminology used by surgeons and parents to determine successful cosmetic outcomes, combined with a lack of validated measures used for outcome appraisal. There is no guarantee that infant genital surgery will improve long-term cosmetic outcomes for the individual concerned; indeed, some adults with congenital variations in sex characteristics who have received surgical intervention in infancy report dissatisfaction and distress associated with their post-surgical genital appearance [ 90 ], concerns which will sometimes require multiple repeat surgeries to address [ 91 ]. Decisions about genital cosmesis should not be made without the active participation and consent of the individual to whom the genitalia belong, and thus elective, irreversible genital surgical interventions for infants and children with congenital variations in sex characteristics should not take place before the individual can decide for themselves whether they would like to undergo such procedures [ 92 ].
19.7% of studies reported parental distress as rationale for either the conduct or timing of interventions, primarily citing an anticipated or voiced parental desire for improved genital cosmesis or for genitals that align more with those associated with ‘typical’ male or female bodies. Medical teams also suggested surgery could relieve psychological distress in parents, improve parental attachment and increase parental comfort. Importantly, a belief that infant surgery was not best practice by surgical teams was occasionally overwhelmed by intense parental desire for intervention in infancy or early childhood, indicating the respect given to parental desire in many settings. Medical teams in some settings struggled with balancing clearly voiced parental desire for early intervention against medical recommendations and human rights imperatives to delay decision-making surrounding intervention until children with congenital variations in sex characteristics are able to participate in decision-making processes. This underscores the need for multidisciplinary teams supporting infants and children with congenital variations in sex characteristics and their parents. Medical teams have a critical role to play in guiding and managing ethical decision-making with parents in clinical settings and sociocultural environments where the rights of the child and obligations of the parents to make decisions which benefit the child do not necessarily match parental desire [ 93 ]. Known drivers of parental distress should be better and consistently integrated into parent and family counselling and psychosocial support, and delivered by qualified professionals like psychologists and social workers [ 4 ]. This counselling may include, for example, a focus on destigmatising congenital variations in sex characteristics, providing clear supportive pathways for communicating with their child on their variation as they grow, being candid on the risks of early surgery for a child, and connecting parents to the intersex community and parents of children with congenital variations in sex characteristics.
39.4% of studies reported a perceived goal of aligning with an assigned sex from parents or surgeons as a rationale for intervention conduct or timing, with arguments around promoting a specific gender also pervading into cosmetic, functional, and anatomical rationales. These rationales largely rely on the assumption that early life experience, including cosmetic, social, and functional features, predicts future gender identity; a theory cited by several studies when navigating sex assignment controversies [ 39 , 78 ]. This is reminiscent of mid-20th century arguments about gender identity development, popularized by John Money (the work of whom is cited by some included articles [ 42 , 81 ] which suggests gender identity is socially constructed in childhood and thus can be re-assigned in infancy, with external factors such as social environment and anatomical features made to match this chosen assignment [ 94 ]. Although this theory is now debunked [ 95 , 96 ], it still pervades in rationales for intervention conduct and a belief that earlier intervention is more efficacious at promoting gender identity development aligned with an assigned sex from parents or medical teams. There is no evidence to suggest surgical intervention for infants with congenital variations in sex characteristics is associated with ‘better’ gender identity development. In fact, several studies note an increased prevalence of gender dysphoria in individuals having undergone “sex-normalising” surgical intervention in infancy [ 2 , 97 , 98 ]. Irreversible, elective genital surgical interventions with the rationale of promoting the development of a specific gender identity are unethical without the full, free, and informed consent and decision-making of the person concerned. Rather, counselling and support for children and parents should be provided throughout infancy, childhood and adolescence, until an individual is old enough to decide for themselves whether they wish to undergo such interventions, and, if they do desire intervention, are able to understand and provide informed consent for any desired interventions.
Forty-six studies were excluded from analysis after full-text screening for citing malignancy as a rationale for conducting interventions, as we determined mitigation of a perceived malignancy risk to be sufficient to consider an intervention to be non-elective. The importance of mitigating the risk of childhood malignancy should not be understated. However, it is important to ensure that the choice to undertake prophylactic genital surgeries (versus a more conservative course of biopsy and monitoring) before a child can provide full, free and informed consent and participate in decision-making processes is done with caution, and that any risk of malignancy is justified and evidence-based. Twenty-six of these forty-six studies cited malignancy as a rationale for surgery for a congenital variation in sex characteristics for which surgical intervention was not recommended as a malignancy mitigation strategy in the 2006 publication, Consensus Statement on Management of Intersex Disorders [ 9 ], which was the last guidance to segregate malignancy risk by individual congenital variation in sex characteristics. This echoes a lack of clarity on the malignant potential of different congenital variations in sex characteristics, which is noted in the extant literature [ 36 , 37 , 99 ]. The expertise of this team did not allow for a critical appraisal of the validity of oncological concerns justifying interventions. Future research should focus on fully elucidating causal pathways and epidemiological connections between individual congenital variations in sex characteristics and malignancy to ensure irreversible genital surgeries are not being conducted when biopsy and monitoring may be sufficient malignancy mitigation strategies.
The social and cultural complexity of congenital variations in sex characteristics across different geographic settings and demographic groups was cited as a reason for conducting interventions and permeated throughout discussions about intervention controversy. This was of particular importance when considering parental desire and concerns about raising a child in a setting that could potentially be stigmatising. Attitudes towards people with congenital variations in sex characteristics differ largely across settings, with cultural considerations about gender preference, identity and stigma towards children with congenital variations in sex characteristics driving strong parental and surgeon desire for intervention in certain settings [ 69 , 100 ]. Concerns about raising a child with congenital variations in sex characteristics should be acknowledged and integrated into discussions with parents (for example, by providing resources, including through peer support from intersex persons and their parents, on how to communicate with other family and community members). Parental or surgeon concerns, however, should not be used to justify the conduct of elective, irreversible genital surgeries before an individual can provide full, free and informed consent.
International human rights treaty bodies have recommended the prohibition of irreversible, elective, genital surgeries conducted on children with congenital variations in sex characteristics before they can participate in decision-making and give full, free and informed consent [ 25 ]. Despite this, we identified that interventions continue to be conducted, based largely around heterogeneous anatomical and functional goals that were not adequately supported by recommendations and the extant medical literature, a desire from parents and surgeons to match genital cosmesis with that typically ascribed to male and female bodies, and a parental desire for intervention conduct. In-keeping with the recommendations of human rights bodies, we recommend that human rights, including the rights of the child, should be protected and prioritised by health systems, and, as such, desire for intervention from parents or surgical teams is not sufficient to justify conducting irreversible, elective, genital interventions before a child can decide for themselves if they want or do not want such procedures, and if they do, provide informed consent to any intervention.
There are notable limitations to this review. Our findings are not entirely representative of the diversity of persons with congenital variations in sex characteristics, given the notable discrepancy in the categorisation of these variations across different disciplines and countries. Our conservative approach to study inclusion, such as excluding studies citing generic urological functional goals and all studies citing malignancy regardless of recommendations from oncological literature, may have led to the exclusion of relevant studies. However, a strength of this review is that this conservative approach ensured that all included interventions were clearly elective. There is also likely to be a publication bias towards congenital variations in sex characteristics that aren’t commonly occurring, given the predominance of case reports emerging from our inclusion criteria (i.e., the large number of diphallia cases included, when the variation itself is reported to be limited to one in every five million live births [ 101 ]). A decision to exclude articles in which it was not certain if all individuals were under the age of 10, to ensure our findings represented only interventions conducted in infancy and childhood, led to the exclusion of cohort and larger scale studies where these data were not disaggregated by age, potentially biasing the study towards primarily considering lower-quality case reports. Available clinical data lacks adequate sample sizes, independence and relevant control groups [ 28 ], undermining the generalisability of the outcomes reported in this review. Although some guidance recommend upscaling longitudinal (including retrospective) outcome assessment studies to address this lack of data [ 2 , 9 ], it is important that any long-term outcome data is collected from individuals who provided full, free and informed consent to undergo elective, irreversible, genital interventions and to being a participant in any research. Outcome measurements and research priorities should focus on understanding the perspectives, health and wellbeing of the individuals affected and how health services can better meet their current and future needs.
International human rights monitoring and accountability mechanisms call for the deferral of decision-making around elective, irreversible, “sex-normalising” genital surgeries for infants and children with congenital variations in sex characteristics until individuals can participate in decision-making and provide free, full and informed consent to any desired interventions. This review has identified a heterogenous literature reporting the surgical outcomes, rationales, and controversies of surgical interventions, with notably inconsistent study designs, methods, and outcome reporting. Assessment of surgical rationale and outcomes has revealed that medical teams continue to conduct these interventions in the face of controversy due to desires to mitigate parental distress surrounding the perceived difficulties of raising a child with a congenital variation in sex characteristics, as well as a variety of under-researched or outdated beliefs that doing so mitigates suboptimal anatomical, cosmetic, physiological, and psychological outcomes for a child, or that surgical intervention is best practice.
Irreversible, elective, “sex-normalising” genital interventions on infants or children with congenital variations of sex characteristics are unethical without the full, free, and informed consent and active participation in decision-making of the individual concerned. Rationales of achieving a cosmetic outcome perceived as satisfactory by individuals to whom the genitalia do not belong, matching parental desire or alleviating parental distress, or promoting a specific gender identity do not justify continuation of these procedures.
National legislating and medical regulatory bodies, in collaboration with relevant international and regional organisations, should enhance efforts to end the conduct of irreversible, elective, “sex-normalising” interventions conducted without the full, free, and informed consent of the person concerned, in an effort to promote and protect the right to the highest attainable standard of physical and mental health for people with congenital variations in sex characteristics.
Supporting information
S1 text. prisma checklist..
https://doi.org/10.1371/journal.pgph.0003568.s001
S2 Text. Search strategy.
https://doi.org/10.1371/journal.pgph.0003568.s002

S1 Table. Quality assessment table.
https://doi.org/10.1371/journal.pgph.0003568.s003
S2 Table. Articles excluded at full text with exclusion reason.
https://doi.org/10.1371/journal.pgph.0003568.s004
S3 Table. Study characteristics with information on data extraction.
https://doi.org/10.1371/journal.pgph.0003568.s005
Acknowledgments
The authors wish to thank Morgan Carpenter and Mauro Cabral Grinspan for their help to define the review’s search strategy, and Anna Coates, Jenny Cresswell, Eva Krpelanova, Andreas Reis, for their inputs on the review’s results and interpretation.
Disclaimer: The named authors alone are responsible for the views expressed in this publication and do not necessarily represent the decisions or the policies of the UNDP-UNFPA-UNICEF-WHO-World Bank Special Programme of Research , Development and Research Training in Human Reproduction (HRP) or the World Health Organization (WHO) .
- 1. World Health Organisation. Gender, Equity and Human Rights; FAQ on Health and Sexual Diversity. An Introduction to Key Concepts [Internet]. 2016. Available from: https://iris.who.int/bitstream/handle/10665/255340/WHO-FWC-GER-16.2-eng.pdf?sequence=1 .
- View Article
- PubMed/NCBI
- Google Scholar
- 24. Office of the High Commissioner for Human Rights, African Commission on Human and Peoples’ Rights, Council of Europe, Office of the Commissioner for Human Rights, Inter-American Commission on Human Rights, Special Rapporteur on torture and other cruel, inhuman or degrading treatment or punishment, et al. Intersex Awareness Day–Wednesday 26 October. End violence and harmful medical practices on intersex children and adults, UN and regional experts urge. [Internet]. Office of the High Commissioner for Human Rights; 2016 [cited 2024 May 1]. Available from: https://www.ohchr.org/en/2016/10/intersex-awareness-day-wednesday-26-october?LangID=E&NewsID=20739 .
- 25. Office of the High Commissioner for Human Rights (OHCHR). OHCHR Technical Note on the Human RIghts of Intersex People: Human Rights Standards and Good Practice [Internet]. 2023 [cited 2024 Mar 22]. Available from: https://www.ohchr.org/en/documents/tools-and-resources/ohchr-technical-note-human-rights-intersex-people-human-rights .
- 26. World Health Organization. Sexual health, human rights and the law [Internet]. Geneva: World Health Organization; 2015 [cited 2023 Aug 2]. Available from: https://apps.who.int/iris/handle/10665/175556 .
- 27. United Nations Human Rights Council. Combating discrimination, violence and harmful practices against intersex persons [Internet]. United Nations General Assembly; 2024 [cited 2024 Apr 23]. Report No.: A/HRC/55/L.9. Available from: https://documents.un.org/doc/undoc/ltd/g24/048/06/pdf/g2404806.pdf?token=XlcT9Mfyw1sK9JJJoM&fe=true .
- 29. ILGA World Database. Legal Frameworks—Restrictions on Interventions on Intersex Minors [Internet]. 2024 [cited 2024 Apr 6]. Available from: https://database.ilga.org/interventions-intersex-minors .
- 33. Veritas Health Innovation. Covidence systematic review software [Internet]. Melbourne, Australia; Available from: www.covidence.org .
- 34. World Health Organisation (WHO). Adolescent Health [Internet]. World Health Organisation Health Topics. 2023 [cited 2023 Aug 31]. Available from: https://www.who.int/health-topics/adolescent-health#tab=tab_1 .
- 37. Amnesty International. First, Do No Harm: Ensuring the Rights of Children with Variations of Sex Characteristics in Denmark and Germany [Internet]. UK; 2017. Available from: https://www.amnesty.org/en/documents/eur01/6086/2017/en/ .
- 92. Zilli L, Khosla R. The notion of consent in the UN Treaty Bodies’ general comments and jurisprudence. United Nations University International Institute for Global Health; 2023.
- 93. Council of Europe. Convention for the Protection of Human Rights and Dignity of the Human Being with regard to the Application of Biology and Medicine: Convention on Human Rights and Biomedicine * [Internet]. Oviedo; 1997. Report No.: No. 164. Available from: https://rm.coe.int/168007cf98 .
- 96. Colapinto J. As Nature Made Him: The Boy Who Was Raised as a Girl. Harper Collins; 2013.
- 101. Murphy JP, Gatti JM. Chapter 122—Abnormalities of the Urethra, Penis, and Scrotum. In: Coran AG, editor. Pediatric Surgery (Seventh Edition) [Internet]. Philadelphia: Mosby; 2012 [cited 2024 Apr 18]. p. 1555–1563. Available from: https://www.sciencedirect.com/science/article/pii/B9780323072557001227 .
- Systematic Review
- Open access
- Published: 30 August 2024
A scoping review of stroke services within the Philippines
- Angela Logan 1 , 2 ,
- Lorraine Faeldon 3 ,
- Bridie Kent 1 , 4 ,
- Aira Ong 1 &
- Jonathan Marsden 1
BMC Health Services Research volume 24 , Article number: 1006 ( 2024 ) Cite this article
Metrics details
Stroke is a leading cause of mortality and disability. In higher-income countries, mortality and disability have been reduced with advances in stroke care and early access to rehabilitation services. However, access to such services and the subsequent impact on stroke outcomes in the Philippines, which is a lower- and middle-income countries (LMIC), is unclear. Understanding gaps in service delivery and underpinning research from acute to chronic stages post-stroke will allow future targeting of resources.
This scoping review aimed to map available literature on stroke services in the Philippines, based on Arksey and O’Malley’s five-stage-process.
Summary of review
A targeted strategy was used to search relevant databases (Focused: MEDLINE (ovid), EMBASE (ovid), Cumulative Index to Nursing and Allied Health Literature (CINAHL), PsycINFO (ebsco); broad-based: Scopus; review-based: Cochrane Library, International Prospective Register of Systematic Reviews (PROSPERO), JBI (formerly Joanna Briggs Institute) as well as grey literature (Open Grey, Google scholar). The searches were conducted between 12/2022-01/2023 and repeated 12/2023. Literature describing adults with stroke in the Philippines and stroke services that aimed to maximize well-being, participation and function were searched. Studies were selected if they included one or more of: (a) patient numbers and stroke characteristics (b) staff numbers, qualifications and role (c) service resources (e.g., access to a rehabilitation unit) (d) cost of services and methods of payment) (e) content of stroke care (f) duration of stroke care/rehabilitation and interventions undertaken (g) outcome measures used in clinical practice.
A total of 70 papers were included. Articles were assessed, data extracted and classified according to structure, process, or outcome related information. Advances in stroke services, including stroke ready hospitals providing early access to acute care such as thrombectomy and thrombolysis and early referral to rehabilitation coupled with rehabilitation guidelines have been developed. Gaps exist in stroke services structure (e.g., low number of neurologists and neuroimaging, lack of stroke protocols and pathways, inequity of stroke care across urban and rural locations), processes (e.g., delayed arrival to hospital, lack of stroke training among health workers, low awareness of stroke among public and non-stroke care workers, inequitable access to rehabilitation both hospital and community) and outcomes (e.g., low government insurance coverage resulting in high out-of-pocket expenses, limited data on caregiver burden, absence of unified national stroke registry to determine prevalence, incidence and burden of stroke). Potential solutions such as increasing stroke knowledge and awareness, use of mobile stroke units, TeleMedicine, TeleRehab, improving access to rehabilitation, upgrading PhilHealth and a unified national long-term stroke registry representing the real situation across urban and rural were identified.
This scoping review describes the existing evidence-base relating to structure, processes and outcomes of stroke services for adults within the Philippines. Developments in stroke services have been identified however, a wide gap exists between the availability of stroke services and the high burden of stroke in the Philippines. Strategies are critical to address the identified gaps as a precursor to improving stroke outcomes and reducing burden. Potential solutions identified within the review will require healthcare government and policymakers to focus on stroke awareness programs, primary and secondary stroke prevention, establishing and monitoring of stroke protocols and pathways, sustainable national stroke registry, and improve access to and availability of rehabilitation both hospital and community.
What is already known?
Stroke services in the Philippines are inequitable, for example, urban versus rural due to the geography of the Philippines, location of acute stroke ready hospitals and stroke rehabilitation units, limited transport options, and low government healthcare insurance coverage resulting in high out-of-pocket costs for stroke survivors and their families.
What are the new findings?
The Philippines have a higher incidence of stroke in younger adults than other LMICs, which impacts the available workforce and the country’s economy. There is a lack of data on community stroke rehabilitation provision, the content and intensity of stroke rehabilitation being delivered and the role and knowledge/skills of those delivering stroke rehabilitation, unmet needs of stroke survivors and caregiver burden and strain,
What do the new findings imply?
A wide gap exists between the availability of stroke services and the high burden of stroke. The impact of this is unclear due to the lack of a compulsory national stroke registry as well as published data on community or home-based stroke services that are not captured/published.
What does this review offer?
This review provides a broad overview of existing evidence-base of stroke services in the Philippines. It provides a catalyst for a) healthcare government to address stroke inequities and burden; b) development of future evidence-based interventions such as community-based rehabilitation; c) task-shifting e.g., training non-neurologists, barangay workers and caregivers; d) use of digital technologies and innovations e.g., stroke TeleRehab, TeleMedicine, mobile stroke units.
Peer Review reports
Introduction
In the Philippines, stroke is the second leading cause of death, with a prevalence of 0·9% equating to 87,402 deaths per annum [ 1 , 2 ]. Approximately 500,000 Filipinos will be affected by stroke, with an estimated US$350 million to $1·2 billion needed to meet the cost of medical care [ 1 ]. As healthcare is largely private, the cost is borne out-of-pocket by patients and their families. This provides a major obstacle for the lower socio-demographic groups in the country.
Research on implementation of locally and regionally adapted stroke-services and cost-effective secondary prevention programs in the Philippines have been cited as priorities [ 3 , 4 ]. Prior to developing, implementing, and evaluating future context-specific acute stroke management services and community-based models of rehabilitation, it was important to map out the available literature on stroke services and characteristics of stroke in the Philippines.
The scoping review followed a predefined protocol, established methodology [ 5 ] and is reported according to the Preferred Reporting Items for Systematic Review and Meta-Analyses Extension for Scoping Reviews Guidelines (PRISMA-ScR) [ 6 , 7 ]. Healthcare quality will be described according to the following three aspects: structures, processes, and outcomes following the Donabedian model [ 8 , 9 ].The review is based on Arksey and O'Malley’s five stages framework [ 5 ].
Stage 1: The research question:
What stroke services are available for adults within the Philippines? The objective was to systematically scope the literature to describe the availability, structure, processes, and outcome of stroke services for adults within the Philippines.
Stage 2: Identifying relevant studies:
The following databases were searched. Focused: MEDLINE, EMBASE, Cumulative Index to Nursing and Allied Health Literature (CINAHL), PsycINFO; broad-based: Scopus; review-based: Cochrane Library, Prospero, JBI (formerly Joanna Briggs Institute); Grey literature: Herdin, North Grey, Grey matters, MedRxiv, NIHR health technology assessment, Department of Health Philippines, The Kings Fund, Ethos, Carrot2. Additionally, reference lists of full text included studies were searched.
The targeted search strategy, developed in consultation with an information scientist, was adapted for each database (see supplemental data). Search terms were peer reviewed using the PRESS (Peer Review of Electronic Search Strategies) checklist [ 10 ].
The key search concepts from the Population, Concept and Context (PCC) framework were ≥ 18 years with a stroke living in the Philippines ( population ), stroke services aiming to maximize well-being, participation and function following a stroke ( concept ) and stroke services from acute to chronic including those involving healthcare professionals, non-healthcare related personnel or family or friends ( context ). Search tools such as medical subject headings (MESH) and truncation to narrow or expand searches were used. Single and combined search terms were included (see supplemental data). The search was initially conducted over two weeks in December 2022 and re-run in December 2023.
Studies were selected if they described stroke care in the Philippines in terms of one or more of the following: (a) patient numbers and stroke characteristics (b) staff numbers, qualifications and role (c) service resources (e.g., number of beds/access to a rehabilitation unit, equipment used) (d) cost of services and methods of payment (UHC, Insurance, private) (e) content of stroke care (f) duration of stroke care (hours of personnel contact e.g., Therapy hours per day); interventions undertaken (g) outcome measures used in clinical practice.
Additional criteria:
Context: all environments (home, hospital, outpatients, clinic, academic institute).
Date limits: published between 2002 onwards. This is based on the Philippines Community Rehabilitation Guidelines published in 2009 that would suggest that papers earlier than 2002 may not reflect current practice [ 11 ].
Qualitative and quantitative studies including grey literature.
Language: reported in English or Filipino only.
Publication status: no limit because the level of rigor was not assessed.
Type of study: no limit which included conference abstracts, as the level of rigor was not assessed.
Studies were excluded if they were in non-stroke populations or the full text article could not be obtained. Conference abstracts were excluded if there were insufficient data about methods and results.
Searches of databases were performed by one researcher (JM) and searches of grey literature were performed by one researcher (AO). All retrieved articles were uploaded into Endnote X9 software™, and duplicates identified and removed before transferring them to Rayyan [ 12 ] for screening.
Stage 3: study selection
The title and abstract were selected using eligibility criteria. Two pairs of researchers independently screened abstracts and titles;(Databases: JM and AL and grey literature by AO and LF). Where a discrepancy existed for title and abstract screening, the study was automatically included for full text review and discussed among reviewers.
Two reviewers (JM and AL) undertook full-text screening of the selected studies. Discrepancies were resolved through consensus discussions without the need for a third reviewer. There were no discrepancies that required a third reviewer. Reason for exclusion were documented according to pre-determined eligibility criteria. References of included full text articles were screened by each reviewer independently and identified articles were subjected to the same screening process as per the PRISMA-ScR checklist (Fig. 1 ).

PRISMA-ScR flow diagram
Stage 4: Charting the data
Two reviewers independently extracted the data using a piloted customized and standardized data extraction form including (1) Structure: financial (e.g., costs, insurance, government funding), resources (structure and number of stroke facilities, staff (number, profession/specialism, qualifications etc.), stroke characteristics (2) Process: duration of care, content of stroke care within acute, secondary care, community, outcome measures used; (3) Outcome: survival, function, patient satisfaction, cost (admission and interventions), and (4) year of publication, geographical location (including if Philippines only or multiple international locations) and type of evidence (e.g., policy, review, observational, experimental, clinical guidelines). Critical appraisal of included studies was not undertaken because the purpose of the review was to map available evidence on stroke services available within the Philippines.
Stage 5: Collating, summarising and reporting the results
The search identified 351 records from databases and registers. A total of 70 records are included and reasons for non-inclusion are summarized in Fig. 1 .
Study descriptors
The characteristics of included studies are shown in Supplementary Material Table 1. Of the 70 included studies, 36 were observational with most being based on a retrospective review of case notes ( n = 31), two were audits, eight were surveys or questionnaires, four were consensus opinion and/or guideline development, three were randomized controlled trial (RCT) or feasibility RCT, 1 was a systematic review, two were policy and guidelines, 11 were narrative reviews or opinion pieces, two were case series or reports and one was an experimental study.
Of the 70 studies, 32 (45.7%) were based in a single tertiary hospital site. There were only three papers based in the community (4.3%). Papers that were opinion pieces or reviews were classified as having a national focus. Of the 22 papers classified as having a national focus, 10 (45.5%) were narrative reviews/ opinion pieces (Table 1 ).
The primary focus of the research studies (excluding the 11 narrative reviews and 2 policy documents) were classified as describing structure ( n = 8, 14%); process ( n = 21,36.8%) or outcomes ( n = 29, 49.2%). The structure of acute care was described in seven studies out of eight studies ( n = 7/8 87.5%) whilst neurosurgery structures were described in one out of eight studies (12.5%). Acute care processes were described in 11 out of 21 studies ( n = 11/21 52.3%) whilst rehabilitation processes were described in six out of 21 studies (28.6%), with three out of 21 studies primarily describing outcome measurement (14.3%). The primary focus of the outcomes were stroke characteristics (25 out of 28 papers, 89.2%) in terms of number of stroke (prevalence), mortality or severity of stroke. Measures of stroke quality of life were not reported. Healthcare professional knowledge was described in two studies ( n = 2/28 7.1%) whilst risk factors for stroke were described in one study ( n = 1/28, 3.6%). Carer burden was described in one study ( n = 1/28, 3.6%).
A summary of the findings is presented in Table 2 .
This scoping review describes the available literature on stroke services within the Philippines across the lifespan of an adult (> 18 years) with a stroke. The review has identified gaps in information about structures, processes and outcomes as well as deficits in provision of stroke services and processes as recommended by WHO. These included a low number of specialist clinicians including neurologists, neuro-radiographers and neurosurgeons. The high prevalence of stroke suggests attention and resources need to focus on primary and secondary prevention. Awareness of stroke is low, especially in terms of what a stroke is, the signs/symptoms and how to minimize risk of stroke [ 25 ]. Barriers exist, such as lack of healthcare resources, maldistribution of health facilities, inadequate training on stroke treatment among health care workers, poor stroke awareness, insufficient government support and limited health insurance coverage [ 22 ].
The scoping review also highlighted areas where further work is needed, for example, descriptions and research into the frequency, intensity, and content of rehabilitation services especially in the community setting and the outcome measures used to monitor recovery and impairment. PARM published stroke rehabilitation clinical practice guidelines in 2012, which incorporated an innovative approach to contextualize Western clinical practice guidelines for stroke care to the Philippines [ 42 ]. Unfortunately, availability and equitable access to evidence-based rehabilitation for people with stroke in the Philippines pose significant challenges because of multiple factors impacting the country (e.g., geographical, social, personal, environmental, educational, economic, workforce) [ 25 , 40 , 43 ].
The number of stroke survivors with disability has not been reported previously, thus, the extent and burden of stroke from acute to chronic is unknown. The recent introduction of a national stroke registry across public and private facilities may provide some of this data [ 82 ]. The project started in 2021 and captures data on people hospitalized for transient ischemic attack or stroke in the Philippines. National stroke registries have been identified as a pragmatic solution to reduce the global burden of stroke [ 83 ] through surveillance of incidence, prevalence, and outcomes (e.g., death, disability) of, and quality of care for, stroke, and prevalence of risk factors. For the Philippine government to know the full impact and burden of stroke nationally, identify areas for improvement and make meaningful changes for the benefit of Filipinos, the registry would need to be compulsory for all public and private facilities and include out of hospital data. This will require information technology, trained workforces for data capture, monitoring and sharing, as well as governance and funding [ 83 ].
This scoping review has generated a better understanding of the published evidence focusing on availability of stroke services in the Philippines, as well as the existing gaps through the lens of Donabedian’s Structure , Process and Outcome framework. The findings have helped to inform a wider investigation of current stroke service utilization conducted using survey and interview methods with stroke survivors, carers and key stakeholders in the Philippines, and drive forward local, regional and national policy and service changes.
Conclusions
This scoping review describes the existing evidence-based relating to structure, processes and outcomes of stroke services for adults within the Philippines. The review revealed limited information in certain areas, such as the impact of stroke on functional ability, participation in everyday life, and quality of life; the content and intensity of rehabilitation both in the hospital or community setting; and the outcome measures used to evaluate clinical practice. Developments in stroke services have been identified however, a wide gap exists between the availability of stroke services and the high burden of stroke in the Philippines. Strategies are critical to address the identified gaps as a precursor to improving stroke outcomes and reducing burden. Potential solutions identified within the review will require a comprehensive approach from healthcare policymakers to focus on stroke awareness programs, primary and secondary prevention, establishing and monitoring of stroke protocols and pathways, implementation of a compulsory national stroke registry, use of TeleRehab, TeleMedicine and mobile stroke units and improve access to and availability of both hospital- and community-based stroke rehabilitation. Furthermore, changes in PhilHealth coverage and universal credit to minimize catastrophic out-of-pocket costs.
Limitations
Although a comprehensive search was undertaken, data were taken from a limited number of located published studies on stroke in the Philippines. This, together with data from databases and grey literature, may not reflect the current state of stroke services in the country.
Availability of data and materials
Not applicable.
Data availability
No datasets were generated or analysed during the current study.
Navarro JC, Baroque AC, Lokin JK, Venketasubramanian N. The real stroke burden in the Philippines. Int J Stroke. 2014;9(5):640–1.
Article PubMed Google Scholar
Philippines TSSot. Phillipines: stroke 2024. Available from: https://www.strokesocietyphilippines.org/philippines-stroke/#:~:text=Stroke%20is%20the%20Philippines'%20second,or%2014.12%25%20of%20total%20deaths .
Banaag MS, Dayrit MM, Mendoza RU. Health Inequity in the Philippines. In: Batabyal A, Higano Y, Nijkamp P (eds). Disease, Human Health, and Regional Growth and Development in Asia. New Frontiers in Regional Science: Asian Perspectives, vol 38. Singapore: Springer; 2019.
Hodge A, Firth S, Bermejo R, Zeck W, Jimenez-Soto E. Utilisation of health services and the poor: deconstructing wealth-based differences in facility-based delivering in teh Philippines. BMC Public Health. 2016;16:1–12.
Arksey H, O’Malley L. Scoping studies: towards a methodological framework. Int J Soc Res Methodol. 2005;8:19–32.
Article Google Scholar
Tricco AC, Lillie E, Zarin W, O’Brien KK, Colquhoun H, Levac D, et al. PRISMA extension for scoping reviews (PRISMA-ScR): checklist and explanation. Ann Intern Med. 2018;169(7):467–73.
Levac D, Colquhoun H, O’Brien KK. Scoping studies: advancing the methodology. Implement Sci. 2010;5:69.
Article PubMed PubMed Central Google Scholar
Donabedian A. The quality of care. How can it be assessed? JAMA. 1988;260(12):1743–8.
Article CAS PubMed Google Scholar
McDonald KM, Sundaram V, Bravata DM, Lewis R, Lin N, Kraft SA, et al. Closing the quality gap: a critical analysis of quality improvement strategies. Tech Rev. 2007;7(9).
McGowan J, Sampson M, Salzwedel DM, Cogo E, Foerster V, Lefebvre C. PRESS peer review of electronic search strategies: 2015 guideline statement. J Clin Epidemiol. 2016;75:40–6.
McGlade B, Mendoza VE. Philippines CBR manual: an inclusive development strategy. Philippines: CBM-CBR Coordinating office; 2009.
Ouzzani M, Hammady H, Fedorowicz Z, et al. Rayyan—a web and mobile app for systematic reviews. Syst Rev. 2016;5(210). https://doi.org/10.1186/s13643-016-0384-4 .
Baliguas B. Adherence to the clinical practice guidelines of the stroke society of the Philippines in the management of ischemic stroke in young adults admitted in 3 tertiary hospitals in Bacolod City, Philippines from May to October 2010. Neurology. 2018;90(15).
Barcelon EA, Moll MAKDN, Serondo DJ, Collantes MEV. Validation of the Filipino version of national institute of health stroke scale. Clinical Neurology. 2016;56:S379.
Google Scholar
Baticulon RE, Lucena LLN, Gimenez MLA, Sabalza MN, Soriano JA. The Neurosurgical Workforce of the Philippines. Neurosurgery. 2024;94(1):202–11. https://doi.org/10.1227/neu.0000000000002630 .
Berroya RM. Incidence of symptomatic intracerebral hemorrhage after thrombolysis for acute ischemic stroke at St. Luke’s Medical Center-Global City from January 2010 to February 2017. J Neurol Sci. 2010;2017(381):398–9.
Carcel C, Espiritu-Picar R. Circadian variation of ischemic and hemorrhagic strokes in adults at a tertiary hospital: a retrospective study. J Neurol Sci. 2009;285:S174.
Cayco CS, Gorgon EJR, Lazaro RT. Proprioceptive neuromuscular facilitation to improve motor outcomes in older adults with chronic stroke. Neurosciences (Riyadh). 2019;24(1):53–60.
Co COC, Yu JRT, Macrohon-Valdez MC, Laxamana LC, De Guzman VPE, Berroya-Moreno RMM, et al. Acute stroke care algorithm in a private tertiary hospital in the Philippines during the COVID-19 pandemic: a third world country experience. J Stroke Cerebrovasc Dis. 2020;29(9):105059.
Co COC, Yu JRT, Laxamana LC, David-Ona DIA. Intravenous thrombolysis for stroke in a COVID-19 positive Filipino patient, a case report. J Clin Neurosci. 2020;77:234–6.
Article CAS PubMed PubMed Central Google Scholar
Collantes ME. Evaluation of change in stroke care in the Philippines using RES-Q data. Eur Stroke J. 2019;4:318.
Collantes ME. Improving stroke systems of care in lmic: Philippines. Int J Stroke. 2021;16(2):4.
Collantes ME, Navarro J, Belen A, Gan R. Stroke systems of care in the Philippines: addressing gaps and developing strategies. Front Neurol. 2022;13:1046351.
Collantes MEV, Yves Miel H, Zuñiga Uezono DR. Incidence and prevalence of stroke and its risk factors in the Philippines: a systematic review. Acta Medica Philippina. 2022;56:26–34.
Collantes MV, Zuniga YH, Granada CN, Uezono DR, De Castillo LC, Enriquez CG, et al. Current state of stroke care in the Philippines. Front Neurol. 2021;12:665086.
Constantino GA, Soliven JA. Points of in-hospital delays in thrombolytic therapy among patients with acute ischemic stroke: a single center 5-year retrospective study. Neurology. 2020;94(15). https://doi.org/10.1212/WNL.94.15_supplement.2901 .
Constantino GAA, Señga MMA, Soliven JAR, Jocson VED. Emerging Utility of Endovascular Thrombectomy in the Philippines: A Single-center Clinical Experience. Acta Med Philipp [Internet]. 2023;57(5). Available from: https://actamedicaphilippina.upm.edu.ph/index.php/acta/article/view/5113 . [cited 2024 Aug 21].
Dans AL, Punzalan FE, Villaruz MV. National Nutrition and Health Survey (NNHeS): atherosclerosis-related diseases and risk factors. Philipp J Intern Med. 2005;43:103–15.
De Castillo LL, Collantes ME. Thrombolysis for stroke at the Philippine general hospital: a descriptive analysis. Cerebrovasc Dis. 2019;48:54.
de Castillo LLC, Diestro JDB, Tuazon CAM, Sy MCC, Añonuevo JC, San Jose MCZ. J Stroke Cerebrovasc Dis. 2021;30(7):105831.
Delfino JPM, Carandang-Chacon CA. Comparison of acute ischemic stroke care quality before and during the COVID-19 pandemic in a private tertiary hospital in metro Manila, Philippines. Neurol Asia. 2023;28(1):13–7.
Department of Health. Department of Health Administrative Order 2011-0003. 2011. [Accessed online: 12/2022], from the Philippine Department of Health].
Department of Health. The national policy framework on the prevention, control and management of acute stroke in the Philippines. 2020.
Diestro JDB, Omar AT, Sarmiento RJC, Enriquez CAG, Castillo LLC, Ho BL, et al. Cost of hospitalization for stroke in a low-middle-income country: Findings from a public tertiary hospital in the Philippines. Int J Stroke. 2021;16(1):39–42.
Duenas M, Ranoa G, Benjamin VS. Assessment of post-stroke caregivers’ burden through the modified caregivers strain index (MCSI) in a tertiary center in the Philippines: a cross-sectional study. Cerebrovasc Dis. 2019;48:56–7.
Duya JE, Hernandez K, San Jose MC. The evolving clinical and echocardiographic profile of patients admitted for acute cardioembolic stroke at a Tertiary Hospital in the Philippines. J Hong Kong Coll Cardiol. 2019;27(1):58.
Espiritu AI, San Jose MCZ. A call for a stroke referral network between primary care and stroke-ready hospitals in the philippines: a narrative review. Neurologist. 2021;26(6):253–60.
Gambito ED, Gonzalez-Suarez CB, Grimmer KA, Valdecañas CM, Dizon JM, Beredo ME, et al. Updating contextualized clinical practice guidelines on stroke rehabilitation and low back pain management using a novel assessment framework that standardizes decisions. BMC Res Notes. 2015;8:643.
Gelisanga MA, Gorgon EJ. Upright motor control test: interrater reliability, retest reliability, and concurrent validity in adults with subacute stroke. Eur Stroke J. 2017;2(1):357–8.
Gonzalez-Suarez C, Grimmer K, Alipio I, Anota-Canencia EG, Santos-Carpio ML, Dizon JM, et al. Stroke rehabilitation in the Philippines: an audit study. Disabil CBR Inclusive Develop. 2015;26(3):44–67.
Gonzalez-Suarez CB, Grimmer K, Cabrera JTC, Alipio IP, Anota-Canencia EGG, Santos-Carpio MLP, et al. Predictors of medical complications in stroke patients confined in hospitals with rehabilitation facilities: a Filipino audit of practice. Neurology Asia. 2018;23(3):199–208.
Gonzalez-Suarez CB, Grimmer-Somers K, Margarita Dizon J, King E, Lorenzo S, Valdecanas C, et al. Contextualizing Western guidelines for stroke and low back pain to a developing country (Philippines): an innovative approach to putting evidence into practice efficiently. J Healthc Leadersh. 2012;4:141–56.
Gonzalez-Suarez CB, Margarita J, Dizon R, Grimmer K, Estrada MS, Uyehara ED, et al. Implementation of recommendations from the Philippine Academy of Rehabilitation Medicine's Stroke Rehabilitation Guideline: a plan of action. Clin Audit. 2013;5:77–89.
Ignacio KHD, Diestro JDB, Medrano JMM, Salabi SKU, Logronio AJ, Factor SJV, et al. Depression and anxiety after stroke in young adult Filipinos. J Stroke Cerebrovasc Dis. 2022;31(2):106232.
Inting K, Canete MT. Ischemic stroke subtypes: a comparison between causative and phenotypic classifications in a tertiary hospital in the Philippines. Int J Stroke. 2021;16(2):28.
Jaca PKM, Chacon CAC, Alvarez RM. Clinical characteristics of cerebrovascular disease with COVID-19: a single-center study in Manila. Philippines Neurology Asia. 2021;26(1):15–25.
Jamora RDG, Corral EV, Ang MA, Epifania M, Collantes V, Gan R. Stroke recurrence among Filipino patients taking aspirin for first-ever non-cardioembolic ischemic stroke. Neurol Clin Neurosci. 2017;5:1–5.
Jamora RDG, Prado MB Jr, Anlacan VMM, Sy MCC, Espiritu AI. Incidence and risk factors for stroke in patients with COVID-19 in the Philippines: an analysis of 10,881 cases. J Stroke Cerebrovasc Dis. 2022;31(11).
Juangco DN, Mariano GS. Endovascular therapy for acute ischemic stroke: a review of cases and outcomes from a primary stroke center (a 5-year retrospective study). Cerebrovasc Dis. 2016;41:54.
Leochico CFD, Austria EMV, Gelisanga MAP, Ignacio SD, Mojica JAP. Home-based telerehabilitation for community-dwelling persons with stroke during the COVID-19 pandemic: a pilot study. J Rehabil Med. 2023;55:jrm4405.
Loo KW, Gan SH. Burden of stroke in the Philippines. Int J Stroke. 2013;8(2):131–4.
Mansouri A, Ku JC, Khu KJ, Mahmud MR, Sedney C, Ammar A, et al. Exploratory analysis into reasonable timeframes for the provision of neurosurgical care in low- and middle-income countries. World Neurosurg. 2018;117:e679–91.
Mendoza RA. The clinical profile and treatment outcome of acute ischemic stroke patients who underwent thrombolysis with recombinant tissue plasminogen activator therapy, Philippine experience: a retrospective study. J Neurol Sci. 2009;285:S85–6.
Navarro J. Prevalence of stroke: a community survey. Philipp J Neurol. 2005;9(2):11–5.
Navarro JC, Venketasubramanian N. Stroke burden and services in the Philippines. Cerebrovasc Dis Extra. 2021;11(2):52–4.
Navarro JC, Baroque AC 2nd, Lokin JK. Stroke education in the Philippines. Int J Stroke. 2013;8 Suppl A100:114–5.
Navarro JC, Chen CL, Lee CF, Gan HH, Lao AY, Baroque AC, et al. Durability of the beneficial effect of MLC601 (NeuroAiD™) on functional recovery among stroke patients from the Philippines in the CHIMES and CHIMES-E studies. Int J Stroke. 2017;12(3):285–91.
Navarro JC, Escabillas C, Aquino A, Macrohon C, Belen A, Abbariao M, et al. Stroke units in the Philippines: an observational study. Int J Stroke. 2021;16(7):849–54.
Navarro JC, San Jose MC, Collantes E, Macrohon-Valdez MC, Roxas A, Hivadan J, et al. Stroke thrombolysis in the Philippines. Neurol Asia. 2018;23(2):115.
Ng JC, Churojana A, Pongpech S, Vu LD, Sadikin C, Mahadevan J, et al. Current state of acute stroke care in Southeast Asian countries. Interv Neuroradiol. 2019;25(3):291–6.
Ocampo FF, De Leon-Gacrama FRG, Cuanang JR, Navarro JC. Profile of stroke mimics in a tertiary medical center in the Philippines. Neurol Asia. 2021;26(1):35–9.
Pascua R, Hiyadan JH. Outcome of decompressive hemicraniectomy without evacuation of hematoma in supratentorial intracerebral hemorrhage in a tertiary government hospital in the Philippines: a retrospective study. Eur Stroke J. 2023;8(2):586.
Prado M, Jamora RD, Charmaine Sy M, Anlacan M, Espiritu A. Determinants and Outcomes of Cerebrovascular Disease in Patients with COVID19 in the Philippines: An Analysis of 10881 Cases. Neurology. 2022;98(18). https://doi.org/10.1212/WNL.98.18_supplement.2076 .
Qua CV, Tiqui V, Villatima NE, Perales DJ, Rubio SM, Santos ER, et al. A predictive assessment of early neurological deterioration among Filipino acute ischemic stroke patients utilizing hematological, lipid profile, and metabolic parameters in a tertiary hospital in Pampanga. Philippines Cerebrovasc Dis. 2022;51:101.
Que DL, Cuanang J, San Jose MC. Clinical profile, management and outcomes of patients with cerebralvenous thrombosis in atertiary hospital in the Philippines. Int J Stroke. 2020;15(1):511.
Quiles LEP, Diamante PAB, Pascual JLV. Impact of the COVID-19 pandemic in the acute stroke admissions and outcomes in a Philippine Tertiary Hospital. Cerebrovasc Dis Extra. 2022;12(2):76–84.
Roxas AA. The RIFASAF project: a case-control study on risk factors for stroke among Filipinos. Philippine J Neurol. 2002;6(1):1–7.
Roxas AAC, Carabal-Handumon J. Knowledge and perceptions among the barangay health workers in Plaridel, Misamis Occidental. Philipp J Neurol. 2002;6(1):44.
Sasikumar S, Bengzon Diestro JD. Global & community health: acute ischemic stroke in Toronto and Manila: bridging the gap. Neurology. 2020;95(13):604–6.
Senga MM, Reyes JPB. Cerebral venous thrombosis in a single center tertiary hospital of a South East Asian country (CVSTS study)-a retrospective study on the clinical profiles of patients with cerebral venous thrombosis. Neurology. 2019;92(15). https://doi.org/10.1212/WNL.92.15_supplement.P5.3-011 .
Sese LVC, Guillermo MCL. Strengthening stroke prevention and awareness in the Philippines: a conceptual framework. Front Neurol. 2023;14:1258821.
Suwanwela NC, Chen CLH, Lee CF, Young SH, Tay SS, Umapathi T, et al. Effect of combined treatment with MLC601 (NeuroAiDTM) and rehabilitation on post-stroke recovery: the CHIMES and CHIMES-E studies. Cerebrovasc Dis. 2018;46(1–2):82–8.
Talamera AF, Franco DS. Validation study of Siriraj stroke score in Southern Philippines. Cerebrovasc Dis. 2011;32:9.
Tan A, Navarro J. Outcomes and quality of care outcome of patients with primary intracerebral hemorrhage in a single center in the philippines. Int J Stroke. 2014;9:269.
Tangcuangco NC, Bitanga ES, Roxas AA, Pascual JL, Saniel E, Reyes JP, et al. Intravenous recombinant tissue plasminogen activator (IV-rtPA) use in acute ischemic stroke in a private tertiary hospital: a Philippine setting. Int J Stroke. 2010;5:107.
Tsang ACO, Yang IH, Orru E, Nguyen QA, Pamatmat RV, Medhi G, et al. Overview of endovascular thrombectomy accessibility gap for acute ischemic stroke in Asia: a multi-national survey. Int J Stroke. 2020;15(5):516–20.
Vatanagul J, Cantero-Auguis C. Awareness on acute stroke management among family medicine and internal medicine residents in Metro Cebu. Philippines J Neurol Sci. 2015;357:e418–9.
Vatanagul J, Rulona IA. The incidence of post-stroke depression in a tertiary hospital in Cebu City, Philippines. J Neurol Sci. 2015;357:e419.
Vatanagul JAS, Rulona IA, Belonguel NJ. Cerebral venous thrombosis (CVST): study of four Filipino patients and literature review. Cerebrovasc Dis. 2013;36:81.
Venketasubramanian N, Yoon BW, Pandian J, Navarro JC. Stroke epidemiology in south, east, and south-east Asia: a review. J Stroke. 2017;19(3):286–94.
Yu RF, San Jose MC, Manzanilla BM, Oris MY, Gan R. Sources and reasons for delays in the care of acute stroke patients. J Neurol Sci. 2002;199(1–2):49–54.
Philippine Neurological Association One Database - Stroke DsSMG. Multicentre collection of uniform data on patients hospitalised for transient ischaemic attack or stroke in the Philippines: the Philippine Neurological Association One Database-Stroke (PNA1DB-Stroke) protocol. BMJ Open. 2022;12(5):54.
Feigin VL, Owolabi MO, Group WSOLNCSC. Pragmatic solutions to reduce the global burden of stroke: a world stroke organization-lancet neurology commission. Lancet Neurol. 2023;22(12):1160–206.
Download references
Acknowledgements
We acknowledge the TULAY collaborators: Dr Roy Francis Navea, Dr Myrna Estrada, Dr Elda Grace Anota, Dr Maria Mercedes Barba, Dr June Ann De Vera, Dr Maria Elena Tan, Dr Sarah Buckingham and Professor Fiona Jones. We are grateful to Lance de Jesus and Dr Annah Teves, Research Assistants on the TULAY project, for their contribution to some of the data extraction.
This research was funded by the NIHR Global Health Policy and Systems Research Programme (Award ID: NIHR150244) in association with UK aid from the UK Government to support global health research. The views expressed in this publication are those of the authors and not necessarily those of the NIHR or the UK’s Department of Health and Social Care.
Author information
Authors and affiliations.
Faculty of Health, Intercity Place, University of Plymouth, Plymouth, Devon, PL4 6AB, UK
Angela Logan, Bridie Kent, Aira Ong & Jonathan Marsden
Royal Devon University Healthcare NHS Foundation Trust, William Wright House, Barrack Road, Exeter, Devon, EX2 5DW, UK
Angela Logan
De La Salle University-Evelyn D. Ang Institute of Biomedical Engineering and Health Technologies, 2401 Taft Avenue, Malate, Manila, 1004, Philippines
Lorraine Faeldon
The University of Plymouth Centre for Innovations in Health and Social Care: A JBI Centre of Excellence, Faculty of Health, Intercity Place, University of Plymouth, Plymouth, Devon, PL4 6AB, UK
Bridie Kent
You can also search for this author in PubMed Google Scholar
Contributions
Conceptualisation, methodology and setting search terms, AL, LF, AO, JM, BK. Searches and screening, AL, JM, LF, AO. Data extraction, AL, LF, AO, JM, LdJ, AT. Original draft preparation, AL, JM. All authors provided substantive intellectual and editorial revisions and approved the final manuscript.
Corresponding author
Correspondence to Angela Logan .
Ethics declarations
Ethics approval and consent to participate, consent for publication, competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary material 1., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Cite this article.
Logan, A., Faeldon, L., Kent, B. et al. A scoping review of stroke services within the Philippines. BMC Health Serv Res 24 , 1006 (2024). https://doi.org/10.1186/s12913-024-11334-z
Download citation
Received : 20 March 2024
Accepted : 22 July 2024
Published : 30 August 2024
DOI : https://doi.org/10.1186/s12913-024-11334-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Stroke care
- Low- middle-income countries
- Developing countries
- Philippines
BMC Health Services Research
ISSN: 1472-6963
- General enquiries: [email protected]
- Systematic Review
- Open access
- Published: 24 August 2024
Palliative care in small-scale living facilities: a scoping review
- Brittany S. DeGraves 1 ,
- Judith M. M. Meijers 2 , 3 ,
- Carole A. Estabrooks 1 &
- Hilde Verbeek 2 , 3
BMC Geriatrics volume 24 , Article number: 700 ( 2024 ) Cite this article
185 Accesses
Metrics details
Innovative small-scale facilities for dementia focus on providing quality of life and maintaining the functional abilities of residents while offering residents a home for life. To fulfill the home-for-life principle, palliative care approaches are necessary to maintain quality of life in these facilities. Few studies have reported on how palliative care is provided to residents in small-scale facilities. The aim of our review is to determine the extent to which palliative care approaches are reported in small-scale facilities.
A scoping review of the literature using recommended methods from the Joanna Briggs Institute. Four databases, CINAHL, PubMed, PsycINFO, and Web of Science, were searched for studies published from 1995 to 2023. One reviewer completed the title, abstract and full-text screening and data extraction; two additional team members piloted the screening and extraction process and met with the main reviewer to make decisions about article inclusion and ensure consistency and accuracy in the review process. The extracted data was open-coded and analyzed using thematic analysis. The data was then synthesized into themes using palliative care domains for dementia.
Of the 800 articles obtained in the search, only ten met the inclusion criteria: six from Japan, two from the Netherlands, and one each from Austria and the United States. In most small-scale facilities, palliative care is important, with facilities prioritizing family involvement and person-centred care, minimizing resident discomfort and enhancing residents’ remaining abilities until the end of life. The included studies did not discuss palliative care policies or professional staff training in depth.
Conclusions
This study provides an overview of the literature on palliative care in small-scale facilities for individuals with dementia. Most facilities focus on residents’ wishes at the end of life to enhance comfort and provide a home-like environment. However, more research is needed to further understand the quality of palliative care approaches in these homes.
Peer Review reports
Innovative small-scale care environments are designed to meet the complex needs of residents with dementia by maintaining their functional ability and quality of life in a person-centred way while maintaining a true home-like setting [ 1 , 2 , 3 ]. Small-scale facilities provide physical and psychosocial care for older adults or individuals who are no longer able to live independently. Small-scale facilities differ from long-term care facilities because they have a smaller number of residents (six to fifteen on average). These facilities provide a community environment and person-centred care while stimulating resident autonomy by promoting active participation in social activities, household chores, and decision-making surrounding daily schedules [ 1 , 2 , 3 , 4 , 5 ]. To create a home-like environment, these facilities include home-like kitchens, living rooms, and private bedrooms while also allowing residents to bring pets and furniture from home [ 1 , 3 , 6 ]. Staff in these environments are often responsible for multiple additional tasks, including cooking and cleaning [ 3 ]. Small-scale facilities are also “a home for life”, meaning that residents can stay and live a purposeful life within these homes until their death [ 3 , 7 ].
There are multiple types of small-scale facilities internationally [ 3 ]. These include Group Living/Homes (Japan/Sweden), Small-scale Living Facilities (Netherlands/Belgium), Green Care Farms (Netherlands), Residential Groups (Germany), Cantou (France), Care Housing (Scotland), Domuses (United Kingdom), Woodside Place (Canada/United States), and Green Houses (United States) [ 3 , 8 ]. Recently, research has focused on the outcomes of living in small-scale homes compared to traditional long-term care; however, few studies have reported on palliative care approaches in these homes [ 3 , 4 , 5 , 9 ]. With these studies reporting that residents in small-scale homes have increased social and physical engagement and functioning compared to residents in long-term care and with these facilities growing in popularity, it is critical to understand if these facilities can provide palliative care and a home for life for residents with dementia. Therefore, factors surrounding palliative care in these innovative facilities, including the quality of palliative care and what can be improved, need to be identified [ 1 , 10 ].
To live within these small-scale settings until death, a palliative approach is essential, as it promotes a focus on person-centred, family-centred and holistic care while trying to improve the quality of dying [ 11 , 12 ]. Palliative care is also essential for providing residents with peace at the end of life, as only half of individuals with dementia in long-term care die peacefully, according to their families [ 13 ]. The quality of care that residents receive toward the end of life is also a more relevant care goal than increasing the length of residents’ lives due to the complicated nature and symptom burden associated with dementia [ 12 , 14 , 15 ].
No review has yet to be completed on the topic of palliative care in small-scale facilities. Our purpose in conducting a scoping review was to identify the current body of knowledge and to identify research gaps in this field. Our research question was “To what extent are palliative care approaches reported in small-scale home-like facilities internationally?”
We conducted a scoping review to identify the available literature and determine how palliative care approaches are used in small-scale facilities [ 16 , 17 ]. Our search strategy and review were based on the framework proposed by the Joanna Briggs Institute Reviewers Manual for scoping reviews [ 17 ]. This framework proposes enhancements made to Arksey and O’Malley’s framework [ 16 ]. We followed the recommended steps of (1) defining the objectives and research questions, (2) developing inclusion criteria and aligning them with the research question, (3) describing a planned approach to searching, data extraction and presentation, (4) searching for evidence, (5) selecting the studies or evidence, (6) data extraction, (7) analysis of data and evidence, (8) presentation of results, and (9) connecting the evidence to the purpose of the review and stating the implications of the findings [ 17 ].
Search strategy and study identification
To identify keywords and create a search string for our literature search, Medline, Google Scholar, and CINAHL were searched to analyze the text words and abstracts of the retrieved papers. A health sciences librarian, in addition to the writers, helped define terminology and add to the search strategy. The final search used all identified terms in the steps described in Table 1 .
Index terms were constructed once the search strategy was finalized in all the following databases: CINAHL, PubMed, PsycINFO, and Web of Science. Our literature search covered from 1995 onward; for the full search strategy, please see Additional File 1 , PubMed Final Search Strategy. The decision to search from 1995 onward was made in partnership with research team members and a health sciences librarian who had familiarity with the literature and discussed this as an adequate timeline to explore both critical concepts identified in our study (palliative care for individuals with dementia, and small-scale dementia care facilities). We also completed an ancestry search of the reference lists of the retrieved papers. We conducted a grey literature search using the search engine Google Scholar. Our initial search was conducted in July 2019 and was updated in September 2023.
We also consulted six experts in palliative care and small-scale living home-like facilities in multiple countries (North America and Europe) to determine if they had access to additional literature focused on this subject area; four answered our inquiry.
Selection criteria
Inclusion criteria.
Inclusion criteria were: (1) studies must have collected primary data; (2) the study aims had to have explicitly addressed small-scale residential models (settings that resemble home-like environments, including having a maximum of 15 residents per house or unit, having staff, residents, and their family form a household together sharing responsibilities, staff performing integrated tasks both medical and personal [ 3 , 5 ]); (3) studies must have described palliative care or end-of-life care approaches; (4) study samples had to include adults aged 65 years or older; (5) studies must have focused primarily on residents with dementia; and (6) studies must have been in English, Dutch, or German languages.
Exclusion criterion
Studies could not have been conducted in a hospice or traditional long-term care facility.
Study selection
Before conducting the review, the selection criteria and review processes were discussed until a consensus was reached between BD, HV, and JM. The selection criteria were piloted in title/abstract and full-text screenings by BD, HV and JM to ensure the criteria were straightforward and to determine agreement between team members. Based on the selection criteria, one reviewer (BD) screened all titles, abstracts, and full-text articles. Two additional team members, HV and JM, each conducted title/abstract and full-text screenings on a subsection of the retrieved articles to ensure consistency and accuracy with BD’s screening decisions. HV and JM also reviewed BD’s screening decisions and notes throughout the screening process. During the screening process, articles that did not directly match the criteria or were deemed questionable by BD were reviewed individually by the three reviewers, who then met to determine the eligibility and make decisions about article inclusion. During these meetings, all decisions and questions that arose during the screening process were discussed with the team to ensure transparency and consistency and reach a consensus. Each full-text article was also discussed in meetings between the three team members (BD, HV, and JM), and an agreement was reached on which papers were to be included.
Database management
We exported the retrieved studies to Endnote X9 for management and deduplication. The review update was conducted using Covidence. Thematic analysis was performed with the assistance of NVIVO-12, which we used to open-code the extracted data and cluster the data into themes.
Data extraction
The extraction process was piloted by three reviewers (BD, HV, JM). Data from the retrieved articles were extracted and summarized by BD, and the extraction tables were reviewed for accuracy and consistency by two team members (JM and HV). We extracted the following information from each study: (1) title of the literature, (2) study design, (3) research question, (4) country of data collection, (5) study sample, (6) type of housing, (6) results and discussion, and (7) study limitations.
Analysis and synthesis of results
The extracted data were synthesized using thematic analysis, where the author read and became familiar with the data, began to open-code included studies and grouped these codes into sub-themes. The subthemes were then clustered into themes using van der Steen et al.’s [ 15 ] domains of palliative care [ 18 ]. These domains of palliative care received international consensus from experts in multiple countries in a European Association for Palliative Care (EAPC) whitepaper to promote high-quality care for individuals with dementia, as there are no preexisting guidelines for end-of-life care for individuals with dementia [ 15 ]. For an in-depth overview of van der Steen et al.’s [ 15 ]. palliative care domains for dementia, please see Table 2 .
The data were reported based on the 2018 PRISMA Preferred Reporting Items for Systematic Reviews and Meta-Analyses extension for Scoping Reviews (PRISMA-ScR) Checklist [ 19 ]. This was performed by BD and checked by JM and HV for clarity and to reach a consensus on the data charting and extraction methods.
Our search retrieved a total of 800 references from PsycINFO, PubMed, CINAHL, and Web of Science databases; 213 duplicates were removed. After title and abstract screening, 99 articles met our criteria for full-text review. Figure 1 shows the PRISMA diagram [ 20 ]. Our final sample of ten reports included eight papers from the initial search and two records (one policy document and one unpublished dataset) from the grey literature.
PRISMA flow diagram [ 20 ]
The articles included in the scoping review were from Japan (6), Austria (1), the Netherlands (2), and the United States (1). Nine papers were in English, and one was in German [ 21 ]. The article in German [ 21 ] was initially translated by Google Translate, and the translation was reviewed by a research associate fluent in German. Of the ten papers, six focused on group homes (GH) in Japan, [ 2 , 22 , 23 , 24 , 25 , 26 ] which house 5–9 residents with mild to moderate dementia and encourage residents to participate in activities of daily living in a home-like setting [ 2 , 3 ]. The concept of group homes in Japan is similar to other homes included in this study, including small-scale facilities in the Netherlands, shared housing (WG’s) in Austria, and Green Houses in the United States, which also have shared home-like kitchen and living areas and private bedrooms and recommend participation in daily activities [ 3 ]. For the characteristics of the included reports, please see Table 3 .
Study characteristics and design
Seven of the final ten reports had the primary goal of investigating palliative care in dementia [ 2 , 21 , 23 , 24 , 25 , 27 , 29 ]. Two studies [ 22 , 28 ] had a more general aim in which palliative care was only mentioned briefly. The last study, Takada et al. (2022) [ 26 ] aimed to develop an advanced care planning inventory and compare this inventory to the quality of death of residents with dementia.
Four studies used qualitative techniques and explored more detailed descriptions of palliative care approaches in small-scale homes [ 2 , 21 , 22 , 27 ]. Five studies used quantitative assessments to compare palliative care practices among a larger population [ 23 , 24 , 25 , 26 , 29 ]. One article focused on examining palliative care practices in one home [ 28 ].
Below, we summarize findings based on van der Steen et al.’s domains of palliative care [ 15 ]. An in-depth summary of the thematic analysis results is provided in Table 4 .
Domain 1: applicability of palliative care
Palliative care services are important in small-scale facilities due to residents’ increasing age and their dementia diagnosis [ 21 , 28 ]. Maintaining a familiar lifestyle, minimizing discomfort, proactively utilizing medical care, and collaborating with family members are essential to end-of-life care [ 2 ].
Hirakawa et al. (2006) [ 23 ] state that despite most group homes reporting that it was possible to provide palliative care (76.4%), 27.5% of these homes would not provide this care, and only 22.3% provided end-of-life care.
Domain 2: person-centred care, communication, and shared decision-making
Having the residents’ wishes as the first priority and including residents in care was discussed in six studies. For example, asking residents’ wishes for end-of-life and incorporating wishes into regular routines, such as asking about preferences for meals, music, and activities [ 2 , 21 , 22 , 23 , 27 ]. In some group homes, residents regularly discussed end-of-life wishes (i.e., location of death) with other residents during regular resident council meetings [ 22 ]. Takada et al. (2022) [ 26 ] also identified a significant relationship between having conversations with residents to express end-of-life wishes (ACP-PI component) and improved quality of end-of-care (increases in the QOD-LTC scores) of individuals who had passed away in group homes in Japan.
Domain 3: advanced care planning and care goals
Managing directors (60.6%) were the primary palliative care planners in group homes and were responsible for confirming resident wishes and directing care, such as organizing staff training to prepare for resident deterioration [ 2 , 24 ]. In Reitinger et al.’s (2010) study, homes described contradictory views on living wills (advanced directives). Some homes preferred living wills to be written as soon as possible (i.e., upon admission), while other homes only used them as a safeguard for the staff or did not require them at all [ 21 ].
Hirakawa et al. (2006) [ 23 ] reported that 68% of staff members asked families about their wishes for end-of-life care, and 65.5% of staff members asked residents about their wishes. Residents with dementia in many homes were viewed as capable of discussing end-of-life wishes and care planning [ 2 , 22 , 28 ]. Similarly, Takada et al. (2022) [ 26 ] emphasized the significance of advanced care planning for residents with dementia, as they reported that the advanced care planning practice inventory (ACP-PI) had a significant association ( p < 0.001) with improvements in the quality of end of life care (QOD-LTC) of residents who had passed away in group homes.
Identifying and respecting residents’ wishes at the end of life did not occur in all group homes; for example, in Nakanishi and Honda’s (2009) [ 24 ] study of 33 end-of-life cases, residents’ preferred place of death was confirmed in only 18.2% of cases.
Domain 4: continuity of care
Group homes and green care farms aim to maintain optimal continuity of care by having staff closely observe and record resident conditions to provide detailed information to other healthcare professionals [ 2 , 23 , 27 ]. These collaborations included close contact between healthcare workers, physicians and psychologists. Healthcare workers shared how a guideline for end-of-life care within the home for all disciplines would be beneficial [ 27 ]. Group homes also report collaborative relationships with medical institutions, which are often mandatory; however, Hirakawa et al. (2006) [ 23 ] report that group homes with progressive end-of-life care policies were less likely to have these affiliations with in-home institutions. Managers in group homes set criteria for physicians to follow during end-of-life consultations and treatment. If the criteria were not met, physicians were replaced [ 2 , 23 ].
Reitinger et al. (2010) [ 21 ] report avoiding or shortening hospitalizations of residents at the end of life with methods including encouraging residents, families, and staff to work together to maintain continuity of care by avoiding hospitalizations. This was found to be an important component of care, as hospitals were identified to not be suitable for residents with dementia as they were often left unattended and lacking in basic dignity while in this setting [ 2 , 21 ]. However, group homes in Japan associated themselves with hospitals to provide end-of-life or emergent care [ 2 , 23 ].
None of the 10 studies reported how the continuity of care between facilities was maintained, especially at the end of life, nor did they report barriers to care or care transfers.
Domain 5: prognostication and timely recognition of dying
Staff reported anticipating resident death through accurate assessments, such as recognizing that a decline in the residents’ appetite and changes in activities of daily living including how becoming dependent on personal hygiene signals the beginning of the end-of-life period [ 2 , 24 ]. Smit et al. (2022) also described how the end-of-life phase is often short in green care farms, possibly due to the encouragement of activity up until death, and this sometimes results in deaths that are sudden and may come as a surprise to staff and family members [ 27 ].
Domain 6: avoiding overly aggressive, burdensome, or futile treatment
Avoiding aggressive treatment is achieved by carefully examining therapeutic measures; for example, care homes try to avoid hospitalization due to these environments, often leading to poor outcomes [ 2 , 21 ].
However, Nakanishi et al. (2016) [ 25 ] report more frequent use of physical restraint and antipsychotics with residents in Japanese group homes than in those receiving home care (in-home long-term care support or multiple care providers). These treatments were used regardless of the professionals’ attitudes and knowledge regarding palliative and dementia care. The authors do not identify in their results why group homes have more aggressive treatments compared to other community providers [ 25 ].
Domain 7: optimal treatment of symptoms and providing comfort
Contrary to the findings of Nakanishi et al. (2016) [ 25 ], minimizing mental and physical discomfort is essential in end-of-life care. In many cases, staff compensate for decreased residents’ ability to maintain quality of life, such as assisting with impaired mobility to enhance residents’ remaining abilities [ 2 ]. Staff use many methods to provide physical and psychological comfort, such as supporting a comfortable posture, touch, and massage while providing optimal treatment for discomfort and pain [ 2 , 23 , 27 ].
However, in van der Steen’s (2016) [ 29 ] unpublished data from the Dutch End of Life in Dementia (DEOLD) study of 330 care homes, small-scale facilities exhibited no difference in comfort at dying but a better quality of dying compared to traditional long-term care.
Domain 8: psychosocial and spiritual support
Group homes provide residents with opportunities for discussion of feelings and provision of grief support near the end of life. These homes also promote a familiar lifestyle and comfort by encouraging interactions with other residents and maintaining familiar relationships, as this helps decrease agitation and promotes quality of life in the end-of-life period [ 2 , 21 , 23 ]. Similarly, Nakanishi et al. (2016) [ 25 ] found that compared to in-home and multiple small-scale home providers, residents in group homes had higher scores of interactions with their surroundings and self-expression closer to the end of life.
Group homes also report a smaller opportunity to heal religiously and provide education about property law within their facilities [ 23 ].
Domain 9: family care and involvement
Family involvement is encouraged by staff by providing the family with a bed to stay at the residents’ bedside at the end of life and encouraging the family to participate in care, such as by picking out residents’ clothes [ 2 , 27 ]. Family education also includes palliative care services and objective health changes experienced by residents to help families make end-of-life care decisions [ 2 , 23 , 27 ]. However, Hirakawa et al. (2006) [ 23 ] found that only 37.2% of group homes within their study provided families with information about palliative care services in their homes.
Most homes focused on family involvement in medical treatment and end-of-life decision-making, including asking about wishes for their loved one’s care. These discussions were held on multiple occasions, including at the beginning of the resident’s stay and as the resident’s condition deteriorated [ 2 , 24 , 27 ]. In some homes, the managing director handled discrepancies between residents’ and families’ wishes [ 2 , 24 ].
In many group homes, aftercare rituals and grief support for staff and families are important in honouring the resident and supporting the community after the resident’s death [ 21 , 22 ]. These rituals include planning ceremonies with families and maintaining cultural practices to honour the resident’s relationships with the family, staff, and residents [ 22 ]. Group homes with more progressive policies on palliative care also reported providing more grief support to families. In contrast, only 69% of group homes reported providing this via various methods, such as phone calls [ 23 ].
Domain 10: education of the healthcare team
Nursing staff regard competence in providing care support as critical for providing end-of-life care [ 21 ]. Staff also describe feeling anxious about providing care when they lack detailed knowledge about the decline of the resident’s condition [ 2 ]. Education surrounding palliative care in group homes includes various topics, such as living wills, communication skills, mental support for residents and family, and end-of-life symptoms and care, to adequately prepare staff to provide palliative care services [ 23 ]. These educational resources have become more common in small-scale homes and are provided via various methods, such as manuals, case studies, or work experience. Teaching sessions also provide staff members with mental health support surrounding their positions as palliative care providers [ 2 , 21 , 23 ].
Increases in quality of life, self-expression, interaction with the surrounding environment, and exhibition of minimum negative behaviour in residents are associated with caregivers having greater knowledge and positive attitudes toward palliative and dementia care [ 25 ].
Domain 11: societal and ethical issues
Kobayashi et al. (2008) [ 2 ] describe that despite financial and staffing restrictions from the Japanese long-term care insurance system that result in these facilities being ill equipped to provide palliative care, administrators choose to provide this care to maintain residents’ quality of life until death. However, many group homes in Hirakawa et al. (2006) report that homes will only provide palliative care when the resident requires no medical intervention, there is no complaint of pain from the resident, and when there is an understanding by all parties surrounding the limitations to care that the group home can provide [ 23 ].
Takada et al. (2022) [ 26 ] was the only study to briefly address national strategies or incentives to provide palliative care. They discussed an end-of-life care bonus, which incentivized nursing homes and group homes to improve the quality of care and advanced care planning at the end of life. In particular, this study revealed that homes that received this national incentive had a significant association with higher QOD-LTC scores and, therefore, higher quality end-of-life care.
Smit et al. (2022) [ 27 ] discuss the implications of COVID-19 for end-of-life care, particularly how staff and caregivers identified barriers to providing care due to specific national guidelines implemented during the pandemic.
No papers discuss the training of caregivers during their professional education domain [ 15 ].
Main findings
To our knowledge, this scoping review is the first to provide an overview of palliative care approaches in innovative small-scale dementia care homes. We found few studies discussing palliative care in small-scale facilities; however, the included studies identified that it is possible to provide palliative care approaches and a “home for life” for residents with dementia in these innovative facilities.
The findings in the 10 included articles suggest that it is possible to provide palliative care for individuals with dementia within innovative small-scale facilities. The homes in this review prioritized resident and family-centred palliative care approaches while providing a familiar environment for residents, avoiding hospital admissions, and providing quality psychosocial and physical care up until death [ 2 , 21 , 22 , 23 , 25 , 27 ]. By maintaining these priorities, these small-scale homes are prioritizing a “home-for-life” principle, which involves maintaining an environment that provides comprehensive care to residents with dementia and a place where they can live and maintain their quality of life up until death [ 3 , 7 , 27 , 30 ]. The home-for-life principle and quality palliative care approaches in these homes support residents’ and families’ wishes when they need it the most [ 11 , 12 ].
Barriers to palliative care
While our results suggest that palliative care is possible in these homes, the included studies rarely discussed barriers to palliative care. Identifying and considering how barriers may influence the ability to provide quality palliative care in these settings is important. One particular barrier identified was the COVID-19 pandemic, which influenced the ability of staff to maintain resident comfort, particularly due to visitation restrictions for family caregivers [ 27 ]. Additional barriers to providing palliative care for dementia in traditional long-term care homes include time commitment, lack of equipment, and inadequate staffing [ 31 ]. Additional research is needed to identify the barriers and potential solutions in innovative small-scale facilities, including barriers newly introduced by the COVID-19 pandemic.
Palliative care approaches in small-scale facilities internationally
The papers in this review touched on all general themes of van der Steen et al.’s [ 15 ] palliative care domains for dementia and applied them to palliative care within these innovative homes. Most of the papers in this review were from Japan. Therefore, our results must be interpreted with some caution because they are likely influenced by cultural factors specific to Japanese group homes. This includes factors such as the end-of-life bonus implemented in Japan in 2006 to care homes (including group homes) to incentivize the quality of palliative care and advanced care planning in care homes toward the end of life [ 26 , 32 ]. Studies in this review, such as Hirakawa et al. (2006) [ 23 ], were published in the early years of this program, and the group homes included in this paper were the only small-scale facilities in our review with strong relationships with hospitals. These relationships may provide additional care resources and relate to Japan’s national strategy for dementia, which emphasizes avoiding hospitalizations of residents by using a trained outreach team to treat individuals with dementia in the community [ 2 , 23 , 24 , 32 , 33 ]. This is particularly important for Japanese group homes, as not all group homes are constructed to provide end-of-life care and are not required to have trained medical professionals on site; this differs from other small-scale homes, such as green houses in the United States, which hold hospice principles and have some specialized palliative care training [ 21 , 24 , 28 ]. Avoiding hospitalizations is a common theme in many homes included in this review. This may be due to the association of hospital use with poor outcomes for residents with dementia, including aggressive treatments, functional decline, falls, and dehydration [ 2 , 21 , 34 , 35 ]. This is consistent with our findings that many small-scale homes prioritized similar palliative care domains, such as reducing discomfort [ 15 ].
Another example of the influence of culture and end-of-life care policies on end-of-life care is how resident autonomy and advanced care planning are treated near the end of life. Hirakawa [ 36 ] describes that resident autonomy is a key factor in the cultural difference between Japan and Western Countries, as Western Countries have high respect for patient autonomy, while in Japan, when an individual lacks decision-making capacity, both the family and physicians play an important role in decision making. Hirakawa [ 36 ] also describes how patients in Japan often have submissive attitudes toward medical professionals concerning their concept of life and death. Similarly, Groenewoud et al. [ 37 ] discuss how Japanese individuals were less likely than Dutch individuals in their study to want to discuss end-of-life care in advance, and more Japanese individuals reported that they would be a burden to family members if they were dependent on help at the end of life. Nakanishi et al. [ 33 ] also explored the differences between end-of-life care policies for dementia in multiple countries using van der Steen et al.’s [ 15 ] recommendations for palliative care for dementia. Nakanishi et al. [ 33 ] found that palliative care policies vary significantly among countries, including the Netherlands, Japan, and the United States, on topics such as the applicability of palliative care, staff education, and person-centred care. This finding is consistent with that of Krikorian et al. [ 38 ], who report that ideas about a good death or end-of-life care relate to financial issues, religion, disease, and cultural factors. Despite the cultural factors that may have influenced our findings, many components of palliative care remain consistent despite cultural and geographical contexts, particularly pain and symptom control [ 39 ]. While the studies included in the review did not identify the cultural or contextual implications influencing palliative care, this research gap should be addressed in the future.
Palliative care domains for dementia
Some of van der Steen et al.’s [ 15 ] recommendations were covered to a greater extent in some of the papers included in this review. The studies included in this review did not adequately describe all palliative care components. This may be the case, as many of the studies included did not aim to describe palliative care in terms of the van der Steen et al. [ 15 ] domains. Palliative care domains such as advanced care planning, palliative care policies, and palliative care education require more research to determine how these processes occur in small-scale facilities. This is important as a focus on palliative care and improving palliative care education is needed both within small-scale facilities and at the public policy level to improve care at the end of life for individuals with dementia and reduce the emotional distress of family and staff members [ 40 , 41 ].
Strengths & limitations
Strengths. We used a rigorous review approach, including using the Joanna Briggs Institute Reviewers Manual for a scoping review, to structure our search and review process [ 17 ]. The van der Steen et al.’s domains for palliative care with dementia, which we used to interpret our findings, have received international consensus from experts in multiple countries [ 15 ]. Using these domains, we identified key gaps surrounding what is currently known about palliative care approaches in these small-scale dementia care facilities.
Limitations. Only papers written in English, German, or Dutch were included in this study, which may limit the number of relevant papers included in the review. The included studies were from four high-income countries, with the majority from Japan. Thus, this paper may not account for the variation in small-scale facilities in other countries. Differences in culture, national policies, and facilities, such as access to resources, may also influence the palliative care approaches of various small-scale facilities, limiting our findings’ generalizability. For example, while there are similarities between small-scale homes, there are differences in terms of access to outdoor space, participation in group activities, staffing, and the inclusion of cultural rituals that may affect palliative care approaches in these facilities [ 3 , 22 ]. The decision to have a single reviewer conduct most of our article screenings may have influenced the sensitivity of our screening process and the number of papers included in our review. However, we aimed to reduce that risk by (1) using strict selection criteria, (2) piloting our selection criteria, and (3) having two additional reviewers conduct subsections of the screening process and reviewing the screening notes and decisions made by the primary reviewer (BD).
Implications
This review identifies the current knowledge base and practices used in small-scale innovative facilities to maintain quality of life and end-of-life for residents living with dementia. The findings of our review can help inform future research in this area by identifying research gaps surrounding palliative care in these innovative facilities. Specifically, future research is needed to identify the following:
Outcomes of palliative care approaches in small-scale facilities compared to traditional homes.
Differences and similarities between countries and cultures regarding palliative care in small-scale facilities.
Various outcomes and practices related to palliative care in different models of small-scale living facilities (comparative evaluation). This includes research on the quality of palliative care, barriers to palliative care, advanced care planning, policies, and education.
This scoping review is the first of which we are aware that attempts to characterize palliative care in small-scale innovative dementia care facilities. Our results suggest that it is possible to provide palliative care and a “home for life” for individuals with dementia in these settings. This paper offers a glimpse into the palliative care approaches in these innovative facilities, particularly their focus on minimizing discomfort and prioritizing patient and family-centred care at the end of life. Most studies in this area have focused primarily on Japanese Group Homes; therefore, cultural factors may have influenced our results. Future research is, therefore, needed to understand the palliative care approaches in small-scale homes internationally and how these innovative facilities compare to traditional long-term care homes.
Data availability
No datasets were generated or analysed during the current study.
Abbreviations
Advanced care planning practice inventory
Cumulative index to nursing and allied health literature
Dutch end-of-life in dementia
European association for palliative care
Green care farm
Group home (Japan)
Preferred reporting items for systematic reviews and meta-analysis
Quality of dying long-term care scale
Wolfarts and welfare mix (Austria shared housing)
te Boekhorst S, Depla, MFIA, de Lange J, Pot AM, Eefsting JA. The effects of group living homes on older people with dementia: a comparison with traditional nursing home care. Int J Geriatr Psychiatry. 2009;24(9):970–8.
Article Google Scholar
Kobayashi S, Yamamoto-Mitani N, Nagata S, Murashima S. End-of-life care for older adults with dementia living in group homes in Japan. Japan J Nurs Science: JJNS. 2008;5(1):31–40.
Article PubMed Google Scholar
Verbeek H, van Rossum E, Zwakhalen SMG, Kempen, GIJM, Hamers JPH. Small, homelike care environments for older people with dementia: a literature review. Int Psychogeriatr. 2009;21(2):252–64.
Ausserhofer D, Deschodt M, De Geest S, van Achterberg T, Meyer G, Verbeek H, et al. There’s no place like home: a scoping review on the impact of homelike residential care models on resident-, family-, and staff-related outcomes. J Am Med Dir Assoc. 2016;17(8):685–93.
Verbeek H, van Rossum E, Zwakhalen SMG, Ambergen T, Kempen, GIJM, Hamers JPH. The effects of small-scale, homelike facilities for older people with dementia on residents, family caregivers and staff: design of a longitudinal, quasi-experimental study. BMC Geriatr. 2009;9:3.
Article PubMed PubMed Central Google Scholar
Kane RA, Lum TY, Cutler LJ, Degenholtz HB, Yu T. Resident outcomes in small-house nursing homes: a longitudinal evaluation of the initial Green House program. J Am Geriatr Soc (JAGS). 2007;55(6):832–9.
Cohen LW, Zimmerman S, Reed D, Brown P, Bowers BJ, Nolet K, et al. The Green House Model of Nursing Home Care in design and implementation. Health Serv Res. 2016;51(S1):352–77.
Marshall M. Small scale, domestic style, long stay accommodation for people with dementia. Stirling: University of Stirling, Dementia Services Development Centre; 1993.
Google Scholar
Verbeek H, Kane RA, van Rossum E, Hamers JPH. Promoting resilience in small-scale, homelike residential care settings for older people with dementia: experiences from the Netherlands and the United States. In: Resnick B, Gwyther L, Roberto K, editors. Resilience in aging. New York, NY: Springer New York; 2010. pp. 289–304.
de Rooij AH, Luijkx KG, Schaafsma J, Declercq A, Emmerink PM, Schols JM. Quality of life of residents with dementia in traditional versus small-scale long-term care settings: a quasi-experimental study. Int J Nurs Stud. 2012;49(8):931–40.
Sawatzky R, Porterfield P, Lee J, Dixon D, Lounsbury K, Pesut B, et al. Conceptual foundations of a palliative approach: a knowledge synthesis. BMC Palliat care. 2016;15:5.
van der Steen JT, Lemos Dekker N, Gijsberts MJHE, Vermeulen LH, Mahler MM, The BAM. Palliative care for people with dementia in the terminal phase: a mixed-methods qualitative study to inform service development. BMC Palliat care. 2017;16:28.
De Roo ML, Albers G, Deliens L, de Vet HCW, Francke AL, Van Den Noortgate N, et al. Physical and psychological distress are related to dying peacefully in residents with dementia in long-term care facilities. J Pain Symp Man. 2015;50(1):1–8.
Froggatt KA, Wilson D, Justice C, MacAdam M, Leibovici K, Kinch J, et al. End-of-life care in long-term care settings for older people: a literature review. Int J Older People Nurs. 2006;1(1):45–50.
van der Steen JT, Radbruch L, Hertogh CMPM, de Boer ME, Hughes JC, Larkin P, et al. White paper defining optimal palliative care in older people with dementia: a Delphi study and recommendations from the European Association for Palliative Care. Palliat Med. 2014;28(3):197–209.
Arksey H, O’Malley L. Scoping studies: towards a methodological framework. Int J Soc Res Methodol. 2005;8(1):19–32.
Peters MDJ, Godfrey C, McInerney P, Munn Z, Tricco AC, Khalil H. Scoping Reviews. In: Aromataris E and Munn Z, editors Joanna Briggs Institute Manual for Evidence Synthesis 2010.
Braun V, Clarke V. Using thematic analysis in psychology. Qualitative Res Psychol. 2006;3(2):77–101.
Tricco AC, Lillie E, Zarin W, O’Brien KK, Colquhoun H, Levac D et al. PRISMA Extension for scoping reviews (PRISMA-ScR): Checklist and Explanation. Ann Inter Med. 2018;169(7):467–73.
Moher D, Liberati A, Tetzlaff J, Altman DG, The PRISMA Group. Preferred reporting items for systematic reviews and meta-analyses: the PRISMA statement. Ann Inte Med. 2009;151(4):264–9.
Reitinger E, Pleschberger S, Schumann F. Living and dying in community based housing for people with dementia. An exploratory qualitative study. Zeitschrift für Gerontologie Und Geriatrie. 2010;43(5):285–90.
Article CAS PubMed Google Scholar
Anbäcken E, Minemoto K, Fujii M. Expressions of identity and self in daily life at a Group Home for older persons with dementia in Japan. Care Manag J. 2015;16(2):64–78.
Hirakawa Y, Masuda Y, Uemura K, Kuzuya M, Kimata T, Iguchi A. End-of-life care at group homes for patients with dementia in Japan: Findings from an analysis of policy-related differences. Arch Gerontol Geriatr. 2006;42(3):233–45.
Nakanishi M, Honda T. Processes of decision making and end-of-life care for patients with dementia in group homes in Japan. Arch Gerontol Geriatr. 2009;48(3):296–9.
Nakanishi M, Hirooka K, Morimoto Y, Nishida A. Quality of care for people with dementia and professional caregivers’ perspectives regarding palliative care in Japanese community care settings. Int J Geriatr Psychiatry. 2016;32(12):1342–51.
Takada S, Ogata Y, Yumoto Y, Ikeda M. Implementation of an Advance Care Planning Inventory and its possible effect on quality of dying: A nationwide cross-sectional study in Group Homes for persons with dementia in Japan. Healthcare. 2021;10(1):62.
Smit KD, Bolt SR, De Boer B, Verbeek H, Meijers JMM. End-of-life care for people with dementia on a green care farm during the COVID-19 pandemic: a qualitative study. BMC Geriatr. 2022;22:956.
The Green House Project. Core values and practices. The Green House Project, Maryland, US: Report; 2012.
van der Steen JT. Dutch End of Life in Dementia (DEOLD). Unpublished Raw Data. 2016.
Wild D, Nelson S, Szczepura A. A ‘home for life’ in residential homes for older people in England: exploring the enhancers and inhibitors. Housing, Care and Support. 2010;13(2):26–35.
Brazil K, Bédard M, Krueger P, Taniguchi A, Kelley ML, McAiney C, et al. Barriers to providing palliative care in long-term care facilities. Can Fam Physician. 2006;52(4):472–3.
PubMed PubMed Central Google Scholar
Nishiguchi S, Sugaya N, Sakamaki K, Mizushima S. End-of-life care bonus promoting end-of-life care in nursing homes: an 11-year retrospective longitudinal prefecture-wide study in Japan. BST. 2017;11:54–61.
Nakanishi M, Nakashima T, Shindo Y, Miyamoto Y, Gove D, Radbruch L, et al. An evaluation of palliative care contents in national dementia strategies in reference to the European Association for Palliative Care white paper. Int Psychogeriatr. 2015;27(9):1551–61.
Dewing J, Dijk S. What is the current state of care for older people with dementia in general hospitals? A literature review. Dementia. 2016;15(1):106–24.
Palan Lopez R, Mitchell SL, Givens JL. Preventing burdensome transitions of nursing home residents with Advanced Dementia: it’s more than advance directives. J Palliat Med. 2017;20(11):1205–9.
Hirakawa Y. Palliative care for the elderly: a Japanese perspective. In E.Chang (editor), Contemporary and Innovative Practice Palliative Care 2012;271–90.
Groenewoud AS, Sasaki N, Westert GP, Imanaka Y. Preferences in end of life care substantially differ between the Netherlands and Japan: results from a cross-sectional survey study. Medicine. 2020;99(44):e22743.
Krikorian A, Maldonado C, Pastrana T. Patient’s perspectives on the notion of a good death: a systematic review of the literature. J Pain Symptom Manag. 2020;59(1):152–64.
Nishimura M, Dening KH, Sampson EL, et al. Cross-cultural conceptualization of a good end of life with dementia: a qualitative study. BMC Palliat Care. 2022;21:106.
Abbey J, Froggatt KA, Parker D, Abbey B. Palliative care in long-term care: a system in change. Int J Older People Nurs. 2006;1(1):56–63.
Vandervoort A, Houttekier D, Vander Stichele R, van der Steen JT, Van den Block L. Quality of dying in nursing home residents dying with dementia: does advanced care planning matter? A nationwide postmortem study. PLoS One. 2014;9(3):e91130.
Download references
Acknowledgements
Not applicable.
The authors disclosed receipt of the following financial support for this article’s research and/or publication: B. DeGraves’ inclusion was supported by the Mitacs Globalink Research Award [grant reference number IT14027]. The authors received no other financial support for the research, authorship, or publication of this article.
Author information
Authors and affiliations.
Faculty of Nursing, University of Alberta, Edmonton, AB, Canada
Brittany S. DeGraves & Carole A. Estabrooks
Department of Health Services Research, Care and Public Health Research Institute, Maastricht University, Maastricht, Netherlands
Judith M. M. Meijers & Hilde Verbeek
Living Lab in Ageing and Long-Term Care, Maastricht, Netherlands
You can also search for this author in PubMed Google Scholar
Contributions
BD, JM, and HV drafted the research question and scoping design. BD collected and analyzed the literature and wrote the review. JM, HV, and CE assisted in writing and reviewing the paper. All authors read and approved the final manuscript.
Corresponding author
Correspondence to Judith M. M. Meijers .
Ethics declarations
Ethics approval and consent to participate, consent for publication, competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Supplementary Material 1
Rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
DeGraves, B.S., Meijers, J.M.M., Estabrooks, C.A. et al. Palliative care in small-scale living facilities: a scoping review. BMC Geriatr 24 , 700 (2024). https://doi.org/10.1186/s12877-024-05259-9
Download citation
Received : 26 March 2024
Accepted : 29 July 2024
Published : 24 August 2024
DOI : https://doi.org/10.1186/s12877-024-05259-9
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Small-scale living
- End of life
- End of life care
- Palliative care
- Nursing home
- Scoping review
BMC Geriatrics
ISSN: 1471-2318
- General enquiries: [email protected]
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu

- Subscribe SciFeed
- Author Biographies
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Dexmedetomidine as adjunctive therapy for the treatment of alcohol withdrawal syndrome: a systematic review and meta-analysis.

1. Introduction
2.1. primary outcome (tracheal intubation), 2.2. secondary outcome (bradycardia), 2.3. secondary outcome (hypotension), 3. discussion, 4.1. study search, 4.2. study selection, 4.3. definition and outcome, 4.4. data extraction and quality assessment, 4.5. data analysis, 5. conclusions, author contributions, data availability statement, acknowledgments, conflicts of interest.
- Association, A.P. Diagnostic and Statistical Manual of Mental Disorders , 5th ed.; American Psychiatric Association: Arlington, VA, USA, 2000. [ Google Scholar ] [ CrossRef ]
- Ganatra, R.B.; Breu, A.C.; Ronan, M.V. Clinical guideline highlights for the hospitalist: 2020 American Society of Addiction Medicine clinical practice guideline on alcohol withdrawal management. J. Hosp. Med. 2022 , 17 , 47–49. [ Google Scholar ] [ CrossRef ]
- Weerink, M.A.S.; Struys, M.M.R.F.; Hannivoort, L.N.; Barends, C.R.M.; Absalom, A.R.; Colin, P. Clinical Pharmacokinetics and Pharmacodynamics of Dexmedetomidine. Clin. Pharmacokinet. 2017 , 56 , 893–913. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Yuki, K. The immunomodulatory mechanism of dexmedetomidine. Int. Immunopharmacol. 2021 , 97 , 107709. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- U.S. Department of Health and Human Services (HHS); Substance Abuse and Mental Health Services Administration (SAMHSA); Center for Behavioral Health Statistics and Quality; Treatment Services Branch. Preliminary Findings from Drug-Related Emergency Department Visits. 2021. Available online: https://store.samhsa.gov/sites/default/files/PEP22-07-03-001.pdf (accessed on 16 April 2024).
- Peterson, C.; Li, M.; Xu, L.; Mikosz, C.A.; Luo, F. Assessment of Annual Cost of Substance Use Disorder in US Hospitals. JAMA Netw. Open 2021 , 4 , e210242. [ Google Scholar ] [ CrossRef ]
- Chang, D.W.; Shapiro, M.F. Association between Intensive Care Unit Utilization during Hospitalization and Costs, Use of Invasive Procedures, and Mortality. JAMA Intern. Med. 2016 , 176 , 1492–1499. [ Google Scholar ] [ CrossRef ]
- Harrer, M.; Cuijpers, P.; Furukawa, T.A.; Ebert, D.D. Doing Meta-Analysis with R: A Hands-On Guide , 1st ed.; Chapman & Hall/CRC Press: Boca Raton, FL, USA; London, UK, 2021. [ Google Scholar ]
- Crispo, A.L.; Daley, M.J.; Pepin, J.L.; Harford, P.H.; Brown, C.V. Comparison of clinical outcomes in nonintubated patients with severe alcohol withdrawal syndrome treated with continuous-infusion sedatives: Dexmedetomidine versus benzodiazepines. Pharmacotherapy 2014 , 34 , 910–917. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Bielka, K.; Kuchyn, I.; Glumcher, F. Addition of dexmedetomidine to benzodiazepines for patients with alcohol withdrawal syndrome in the intensive care unit: A randomized controlled study. Ann. Intensive Care 2015 , 5 , 33. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- VanderWeide, L.A.; Foster, C.J.; MacLaren, R.; Kiser, T.H.; Fish, D.N.; Mueller, S.W. Evaluation of Early Dexmedetomidine Addition to the Standard of Care for Severe Alcohol Withdrawal in the ICU:A Retrospective Controlled Cohort Study. J. Intensive Care Med. 2016 , 31 , 198–204. [ Google Scholar ] [ CrossRef ]
- Lizotte, R.J.; Kappes, J.A.; Bartel, B.J.; Hayes, K.M.; Lesselyoung, V.L. Evaluating the effects of dexmedetomidine compared to propofol as adjunctive therapy in patients with alcohol withdrawal. Clin. Pharmacol. 2014 , 6 , 171–177. [ Google Scholar ] [ CrossRef ]
- Love, K.; Zimmermann, A.E. Use of Propofol Plus Dexmedetomidine in Patients Experiencing Severe Alcohol Withdrawal in the Intensive Care Unit. J. Clin. Pharmacol. 2020 , 60 , 439–443. [ Google Scholar ] [ CrossRef ]
- Collier, T.E.; Farrell, L.B.; Killian, A.D.; Kataria, V.K. Effect of Adjunctive Dexmedetomidine in the Treatment of Alcohol Withdrawal Compared to Benzodiazepine Symptom-Triggered Therapy in Critically Ill Patients: The EvADE Study. J. Pharm. Pract. 2022 , 35 , 356–362. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Mueller, S.W.; Preslaski, C.R.; Kiser, T.H.; Fish, D.N.; Lavelle, J.C.; Malkoski, S.P.; MacLaren, R. A randomized, double-blind, placebo-controlled dose range study of dexmedetomidine as adjunctive therapy for alcohol withdrawal. Crit. Care Med. 2014 , 42 , 1131–1139. [ Google Scholar ] [ CrossRef ]
- Ludtke, K.A.; Stanley, K.S.; Yount, N.L.; Gerkin, R.D. Retrospective Review of Critically Ill Patients Experiencing Alcohol Withdrawal: Dexmedetomidine Versus Propofol and/or Lorazepam Continuous Infusions. Hosp. Pharm. 2015 , 50 , 208–213. [ Google Scholar ] [ CrossRef ]
- Wong, A.; Benedict, N.J.; Kane-Gill, S.L. Multicenter evaluation of pharmacologic management and outcomes associated with severe resistant alcohol withdrawal. J. Crit. Care 2015 , 30 , 405–409. [ Google Scholar ] [ CrossRef ]
- Riihioja, P.; Jaatinen, P.; Oksanen, H.; Haapalinna, A.; Heinonen, E.; Hervonen, A. Dexmedetomidine, diazepam, and propranolol in the treatment of ethanol withdrawal symptoms in the rat. Alcohol. Clin. Exp. Res. 1997 , 21 , 804–808. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Rovasalo, A.; Tohmo, H.; Aantaa, R.; Kettunen, E.; Palojoki, R. Dexmedetomidine as an adjuvant in the treatment of alcohol withdrawal delirium: A case report. Gen. Hosp. Psychiatry 2006 , 28 , 362–363. [ Google Scholar ] [ CrossRef ]
- DeMuro, J.P.; Botros, D.G.; Wirkowski, E.; Hanna, A.F. Use of dexmedetomidine for the treatment of alcohol withdrawal syndrome in critically ill patients: A retrospective case series. J. Anesth. 2012 , 26 , 601–605. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Rayner, S.G.; Weinert, C.R.; Peng, H.; Jepsen, S.; Broccard, A.F. Dexmedetomidine as adjunct treatment for severe alcohol withdrawal in the ICU. Ann. Intensive Care 2012 , 2 , 12. [ Google Scholar ] [ CrossRef ]
- Frazee, E.N.; Personett, H.A.; Leung, J.G.; Nelson, S.; Dierkhising, R.A.; Bauer, P.R. Influence of dexmedetomidine therapy on the management of severe alcohol withdrawal syndrome in critically ill patients. J. Crit. Care 2014 , 29 , 298–302. [ Google Scholar ] [ CrossRef ]
- Polintan, E.T.T.; Danganan, L.M.L.; Cruz, N.S.; Macapagal, S.C.; Catahay, J.A.; Patarroyo-Aponte, G.; Azmaiparashvili, Z.; Lo, K.B. Adjunctive Dexmedetomidine in Alcohol Withdrawal Syndrome: A Systematic Review and Meta-analysis of Retrospective Cohort Studies and Randomized Controlled Trials. Ann. Pharmacother. 2022 , 57 , 696–705. [ Google Scholar ] [ CrossRef ]
- Fiore, M.; Torretta, G.; Passavanti, M.B.; Sansone, P.; Pace, M.C.; Alfieri, A.; Aurilio, C.; Simeon, V.; Chiodini, P.; Pota, V. Dexmedetomidine as adjunctive therapy for the treatment of alcohol withdrawal syndrome: A systematic review protocol. JBI Database Syst. Rev. Implement. Rep. 2019 , 17 , 2159–2164. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021 , 372 , n71. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Sterne, J.A.C.; Savović, J.; Page, M.J.; Elbers, R.G.; Blencowe, N.S.; Boutron, I.; Cates, C.J.; Cheng, H.-Y.; Corbett, M.S.; Eldridge, S.M.; et al. RoB 2: A revised tool for assessing risk of bias in randomised trials. BMJ 2019 , 366 , l4898. [ Google Scholar ] [ CrossRef ]
- Wells, G.A.; Shea, B.; O’Connell, D.; Peterson, J.; Welch, V.; Losos, M.; Tugwell, P. The Newcastle-Ottawa Scale (NOS) for Assessing the Quality of Nonrandomised Studies in Meta-Analyses ; Ottawa Hospital Research Institute: Ottawa, ON, USA, 2000. [ Google Scholar ]
- Mantel, N.; Haenszel, W. Statistical aspects of the analysis of data from retrospective studies of disease. J. Natl. Cancer Inst. 1959 , 22 , 719–748. [ Google Scholar ]
- Hedges, L.V.; Vevea, J.L. Estimating Effect Size under Publication Bias: Small Sample Properties and Robustness of a Random Effects Selection Model. J. Educ. Behav. Stat. 1996 , 21 , 299–332. [ Google Scholar ] [ CrossRef ]
- Paule, R.C.; Mandel, J. Consensus Values and Weighting Factors. J. Res. Natl. Bur. Stand. 1982 , 87 , 377–385. [ Google Scholar ] [ CrossRef ]
Click here to enlarge figure
| Author (Published Year) [Ref.] | Setting | Study Design | Control Group | Time Spam | N. Patients | Outcome(s) |
|---|---|---|---|---|---|---|
| Crispo, A.L. (2014) [ ] | ED | RC | BZD | 2011–2012 | 122 | TI + B + H |
| Bielka, K. (2015) [ ] | ED | RCT | BZD | NS | 134 | TI + B + H |
| VanderWeide, L.A. (2016) [ ] | Mixed | RC | BZD | 2008–2012 | 84 | TI + B + H |
| Lizotte, R.J. (2014) [ ] | ED | RC | BZD + P | 2010–2013 | 82 | TI + B + H |
| Love, K. (2020) [ ] | ICU | RC | BZD + P | 2015–2018 | 53 | TI + B + H |
| Collier, T.E. (2022) [ ] | ICU | RC | BZD | 2015–2018 | 110 | TI + B |
| Mueller, S. (2014) [ ] | ED | RCT | BZD | 2009–2012 | 48 | B + H |
| Ludtke, K.A. (2015) [ ] | ED | RC | BZD + P | 2002–2009 | 64 | TI |
| Wong, A. (2015) [ ] | Mixed | RC | BZD + P | 2009–2012 | 258 | TI |
| Study | Ref. | R | D | Mi | Me | S | O |
|---|---|---|---|---|---|---|---|
| Bielka, K. | [ ] | + | − | + | + | + | + |
| Mueller, S. | [ ] | + | + | − | + | + | + |
| Study | Ref. | Selection | Comparability | Outcome |
|---|---|---|---|---|
| Crispo, A.L. | [ ] | *** | * | *** |
| Lizotte, R.J. | [ ] | *** | ** | ** |
| VanderWeide, L.A. | [ ] | ** | * | ** |
| Ludtke, K.A. | [ ] | *** | * | *** |
| Wong, A. | [ ] | *** | ** | *** |
| Love, K. | [ ] | *** | ** | *** |
| Collier, T.E. | [ ] | *** | ** | ** |
| Participants | Intervention | Comparison | Outcomes | Study Design |
|---|---|---|---|---|
| Adult patients in any setting with alcohol withdrawal syndrome | Dexmedetomidine as adjunctive therapy to standard of care | Standard of care | Primary outcomes: Tracheal intubation Secondary outcomes: (a) Hypotension (b) Bradycardia | Randomized controlled trials and observational studies (including cohort and case-control studies) |
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Fiore, M.; Alfieri, A.; Torretta, G.; Passavanti, M.B.; Sansone, P.; Pota, V.; Simeon, V.; Chiodini, P.; Corrente, A.; Pace, M.C. Dexmedetomidine as Adjunctive Therapy for the Treatment of Alcohol Withdrawal Syndrome: A Systematic Review and Meta-Analysis. Pharmaceuticals 2024 , 17 , 1125. https://doi.org/10.3390/ph17091125
Fiore M, Alfieri A, Torretta G, Passavanti MB, Sansone P, Pota V, Simeon V, Chiodini P, Corrente A, Pace MC. Dexmedetomidine as Adjunctive Therapy for the Treatment of Alcohol Withdrawal Syndrome: A Systematic Review and Meta-Analysis. Pharmaceuticals . 2024; 17(9):1125. https://doi.org/10.3390/ph17091125
Fiore, Marco, Aniello Alfieri, Giacomo Torretta, Maria Beatrice Passavanti, Pasquale Sansone, Vincenzo Pota, Vittorio Simeon, Paolo Chiodini, Antonio Corrente, and Maria Caterina Pace. 2024. "Dexmedetomidine as Adjunctive Therapy for the Treatment of Alcohol Withdrawal Syndrome: A Systematic Review and Meta-Analysis" Pharmaceuticals 17, no. 9: 1125. https://doi.org/10.3390/ph17091125
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
Securing data and preserving privacy in cloud IoT-based technologies an analysis of assessing threats and developing effective safeguard
- Open access
- Published: 27 August 2024
- Volume 57 , article number 269 , ( 2024 )
Cite this article
You have full access to this open access article

- Mayank Pathak 1 ,
- Kamta Nath Mishra 1 &
- Satya Prakash Singh 1
651 Accesses
7 Altmetric
Explore all metrics
The Internet of Things (IoT) is a powerful technology adopted in various industries. Applications of the IoT aim to enhance automation, productivity, and user comfort in a cloud and distributive computing environment. Cloud computing automatically stores and analyzes the large amounts of data generated by IoT-based applications. Cloud computing has become a crucial component of the information age through easier data administration and storage. Currently, government agencies, commercial enterprises, and end users are rapidly migrating their data to cloud environments. This may require end-user authentication, greater safety, and data recovery in the event of an attack. A few issues were discovered by authors after analysis and assessments of various aspects of the published research papers. The research analysis reveals that the existing methods need to be further improved to address the contemporary dangers related to data security and privacy. Based on the research reports, it can be stated that safe end-to-end data transmission in a cloud-IoT environment requires modifications and advancements in the design of reliable protocols. Upcoming technologies like blockchain, machine learning, fog, and edge computing mitigate data over the cloud to some level. The study provides a thorough analysis of security threats including their categorization, and potential countermeasures to safeguard our cloud-IoT data. Additionally, the authors have summarized cutting-edge approaches like machine learning and blockchain technologies being used in the data security privacy areas. Further, this paper discusses the existing problems related to data privacy and security in the cloud-IoT environment in today’s world and their possible future directions.
Similar content being viewed by others
Cloud and Big Data Security System’s Review Principles: A Decisive Investigation

A survey on boosting IoT security and privacy through blockchain

Security of IoT-Cloud Systems Based Machine Learning
Explore related subjects.
- Artificial Intelligence
Avoid common mistakes on your manuscript.
1 Introduction
The speedy development of technology and Internet of Things (IoT)-based devices in organizations and enterprises give rise to progressive increases in various types of data. IoT has become a vital part of human life and it can be sensed in our day-to-day activities. It was said by Kumar et al. ( 2019 ) that IoT is a revolutionary approach that has changed numerous aspects of human life. It makes our lives easy and secure by handling various applications of smart city societies including pollution control , smart transportation , smart industries , smart home security systems , smart water supply , and many more systems. The small amount of data accumulates and gives rise to Big Data which is stored, processed, and analyzed by a set of technologies. Big Data is a large volume of data generated by IoT sensors , servers , social media , and medical equipment, etc . Cloud computing is internet-based computing that enables inexpensive, reliable, easy, simple, and convenient accessibility to the resource (Albugmi et al. 2016 ). Cloud computing provides service, and reduces infrastructure maintenance overheads. Apart from this it also provides better performance to the end users and flexibility for storing data over the cloud. However, storing highly confidential Big Data obtained from IoT devices , medical data , and server data over the cloud may pose threats to attackers. Therefore, data security is a most important concern when a large or bulk of confidential data is to be stored in the cloud (Sumithra and Parameswari 2022 ).
Cyber attacks target IoT devices that impact stakeholders, and they may damage physical systems, m-health, and economic systems severely. Earlier events show that IoT devices hold numerous vulnerabilities. Many manufacturers struggle to protect IoT devices from vulnerabilities (Schiller et al. 2022a ). Cloud computing integrates distributed computing, grid computing, and utility computing to establish a shared virtual resource pool (Sun 2019 ). There are privacy and security issues in these cases because the owners have no control over the information and tasks carried out on the platform. Various privacy protection methods have been introduced such as encryption , access control , cryptography , and digital signature but they are not strong enough, as a result, attackers easily break through the security wall and harm the data over the cloud.
The authors of the research papers reviewed various methods and suggested some measures and directions to protect the data in cloud computing and edge computing environments (Ravi Kumar et al. 2018 ; Zhang et al. 2018 ). Through this study, the author found that data privacy , data remoteness , data leakage , and data segregation are crucial problems that may exist. The survey paper (Hong-Yen and Jiankun 2019 ) addressed modern privacy and preserving models to focus on numerous privacy-interrelated frameworks to be implemented in practice.
As a contribution, the current paper aims to accomplish the following objectives:
To examine existing security frameworks , standards , and techniques that incorporate different standards across multiple areas of cloud-IoT technologies.
To explore and discuss open-ended challenges in a Cloud-IoT-based environment concerning securities and privacy.
To present and discuss the classification of challenges in Cloud-IoT environments after evaluating the performance of existing literature. It also provides solutions for the identified open-ended challenges and addresses future security concerns related to Cloud-IoT technologies.
The following are the Research Questions ( RQs ) that the researchers tried to investigate through the current research paper:
RQ 1 : To Investigate how IoT , Big Data , and Cloud computing technologies are interconnected, and how security can be a major concern when data is stored in a cloud environment.
RQ 2 : What are the security objectives for the data security and privacy domain?
RQ 3 : What are the privacy concerns for end-users in cloud-IoT-based environments?
RQ 4 : What is the role of edge computing in enhancing privacy in a cloud-IoT environment?
RQ 5 : What are vulnerabilities that exist in the cloud-IoT infrastructure?
RQ 6 : What are the current research trends and areas of focus?
RQ 7 : What are Advancements in security threat detection and avoidance ?
RQ 8 : How machine learning can be a useful tool in detecting vulnerabilities within a cloud-IoT environment?
RQ 9 : How can blockchain technology be an effective measure of data security and privacies?
RQ 10 : What are Current Issues in Data Security and Privacy?
Regarding the remaining portion of the document, Sect. 2 describes the methodology of this research work. Section 3 discusses the characteristics of a research paper and explains how the current paper differs from others. Section 4 talks about security goals in the Cloud-IoT environment. Section 5 discusses the taxonomy related to Cloud-IoT environment which includes Big Data and IoT along with its applications in various domains. Section 6 is a comprehensive study of various attacks in the Cloud-IoT environment. Section 7 (A) explores the study of various research trends through Table 1 . Section 7 (B) describes attack vectors and mitigation strategies through Table 2 . Section 8 presents an in-depth analysis of digital forensics. Section 9 talks about the machine learning and Blockchain technologies-based approaches used for threat detection and recovery. Section 10 covers the current challenges in data security and privacy, and it provides a brief description of possible solutions listed in Table 3 . Further, this section highlights the research gaps identified by the author in Table 4 . Conclusions and future research work are discussed in Sect. 11 .
2 Methodology: a systematic approach
The methodology is the systematic approach that is used by the author to conduct research, analyze the data, and frame conclusions. The methodology section covers the boundary area of methods and approaches that are followed by the author to write the current research paper. The methodology of this research paper is as follows: To examine IoT security challenges and threats author searched numerous kinds of literature on IoT security. For this keyword IoT, Cloud-IoT security was used for standard survey papers that were published in reputed journals like IEEE, Elsevier, Springer, and many more. After completing this task, the author examined numerous techniques and methodologies presented in those survey papers critically analyzed the facts, and algorithms, and selected a set of relevant topics that is important from a security perspective, provided with the help of the author’s individual experience in the sphere of security. In addition to this, the author introduced various standard approaches that are recognized in the sphere of security for protection against threats. At last, the author utilized Internet-based search techniques to find the most appropriate security products. The Methodology of the current paper is divided into three standard stages as follows.
Phase 1 Identification of the study area, formulation of the research questions, sampling, and establishing the primary search approach or standards.
Phase 2 Using the search strategy or criterion about existing literature, carrying out keyword searches, Boolean searches involving the combination of keywords and phrases with the operators “AND”, and “OR”, and database searches, assessing the results, and formulating selection criteria.
Phase 3 Finding and evaluating approved literature, articles, papers, websites, and web documents by the chosen primary research topic.
Figure 1 shows the distribution of references over the year. The figure portrays which year the researcher’s paper was selected to prepare the current paper. The author selected the previous research paper from year 2016 to 2024, a recently published paper. The author reviewed the paper which includes published journal and conference papers. The author searched, examined, and analyzed the paper was included in the references section of the manuscript.
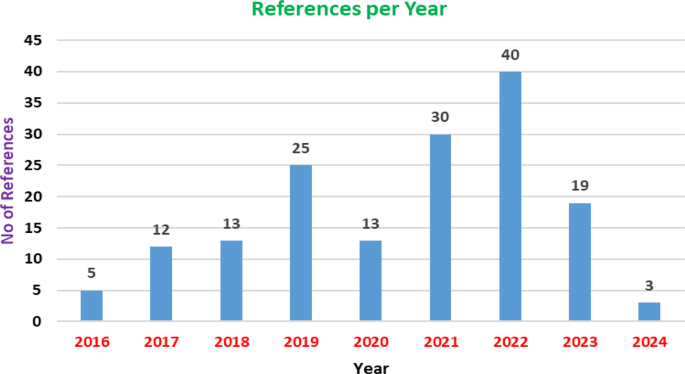
Reference timeline
2.1 Inclusion/exclusion criteria
The inclusion and exclusion criteria aim to identify the research studies that correspond with the questions under investigation. The primary studies were identified using the inclusion criteria that we are presenting. The exclusion criteria were left out since they represent the negative version of the inclusion criteria that were specified.
Inclusion Criteria
IC 1 : Publications released on and after the year 2016.
IC 2 : Publications that have been published in peer-reviewed journals, conferences, workshops, etc.
IC 3 : English-language articles published.
IC 4 : Articles that are required to contain an abstract and title.
IC 5 : Publication that specifically addresses the subject topic such as data security, privacies encryption decryption, machine learning, blockchain, or research problems.
IC 6 : Research with subject-specific keywords included.
IC 7 : Systematic reviews, theoretical analysis, and empirical study.
Exclusion Criteria
EX 1 : Articles that are loosely connected to the research question or do not answer it.
EX 2 : Articles whose complete text cannot be accessed.
EX 3 : Articles not available in English.
EX 4 : Articles that were released almost ten years ago.
EX 5 : Studies with poor ratings or serious methodological errors.
EX 6 : Articles that don’t explicitly address privacy and data security concerns is excluded.
EX 7 : To prevent prejudice from incorporating the same study more than once, remove duplicate publications.
2.2 Algorithms, tools, and techniques Implemented
Alogrithm 1 : RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Cryptography), and AES (Advanced Encryption Standard) are a few examples of the particular encryption techniques used in the studies.
Alogrithm 2 : Determine which machine learning techniques—such as anomaly detection methods (e.g., k-means clustering, isolation forests)—are utilized to detect data breaches or to ensure data security.
Tool 1 : To manage and organize references, use programs like Scispace, Citation Gecko, and Open Knowledge Map.
Tool 2 : To create visual representations of the data in MS Excel (graph).
Tool 3 : To check Grammar and Spelling Grammarly software tools are used.
Tool 4 : To draw the picture tools such as Paint, Smart Draw, and Origin-Lab are used.
Tool 5 : iThenticate is used for Plagiarism detection.
Techniques for Search
Technique 1 : Use Boolean operators and specified keywords to search IEEE Xplore, Scopus, and Google Scholar. The following query is an example: “data security” AND “privacies” AND (encryption OR data protection) AND “2016–2024”.
3 Advancing IoT, Big Data, and cloud integration: novelty in current research
In the rapidly evolving landscape of technology, the convergence of the IoT, Big Data, and Cloud computing stands at the forefront of innovation. Each domain, when studied individually, offers significant advancements and benefits. However, the integration of these technologies opens up unprecedented possibilities, presenting both opportunities and challenges. This research work provides the novel aspects of combining IoT , Big Data , and Cloud computing . Further, the paper highlights the transformative impact on various industries and emerging security concerns. This study aims to uncover new insights and propose solutions to ensure the safe and efficient deployment of integrated systems by exploring how these technologies interact. The major contributions of the current research paper are as follows:
Integration of IoT, Big Data, and Cloud Computing : The paper examines the combined effects and security threats of integrating IoT, Big Data, and Cloud computing.
Role Analysis : It offers an in-depth analysis of how IoT, Big Data, and Cloud storage work together.
Data Flow : The paper explores the process where data generated from IoT devices becomes Big Data and is subsequently stored in the Cloud.
Security Threats : It highlights the potential security threats during the transmission and storage of data.
Proposed Protections : The authors propose standard approaches to protect against potential attacks that could compromise the data.
Digital Forensics : The paper discusses digital forensics as a method to preserve and analyze digital data post-attack, aiding in tracing the attacker’s footprint and identifying patterns and trends.
Recent Data Security Technologies : In this research work, the authors addressed new technologies that have the potential to significantly reduce threats in cloud-IoT environments.
Research Focus : Authors determine the researcher’s field of expertise methodically.
4 Security goals in Cloud-IoT environments: a comprehensive overview
Security in Cloud-IoT environments is paramount due to the interconnected nature of devices and the vast amount of sensitive data they generate and process. Ensuring the confidentiality, integrity, and availability of data and services has become a major challenge as cloud computing and IoT devices become more integrated into everyday life and vital infrastructure. In an ever-changing digital ecosystem, this comprehensive overview seeks to explore the major security objectives, difficulties, and tactics that are crucial for protecting Cloud-IoT environments.
Figure 2 shows security objectives in a cloud environment. To guarantee the confidentiality, integrity, availability, and general security of data, applications, and resources hosted in the cloud, security objectives for a cloud environment are essential. These goals assist businesses in defining their security objectives and directing the application of suitable security solutions. For the confidentiality, integrity, and availability of data and services hosted in the cloud, security objectives for the environment are crucial. These goals aid organizations in developing a framework for putting security measures in place and in defining their security objectives. To respond to changing threats and keep a solid security posture in the cloud, it is essential to regularly assess and update security goals and procedures.
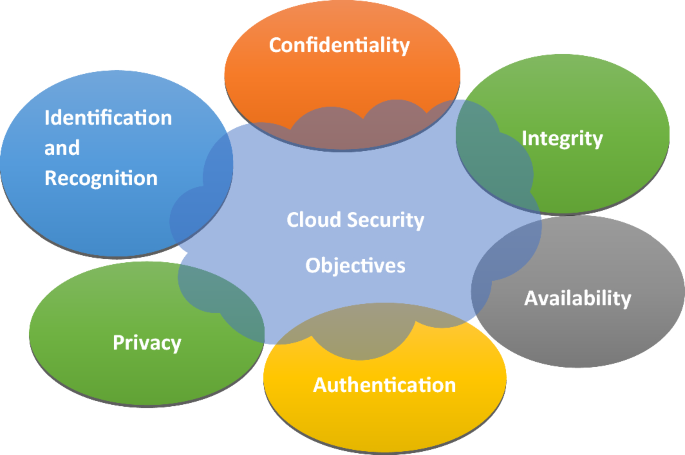
Security objective in cloud environment
Confidentiality Confidentiality refers to safeguarding or protecting critical data from unauthorized access. The information will only be revealed or accessible to those persons who are authorized (Schiller et al. 2022a ).
Identification and Recognition Identification is a unique way to provide attributes to users or devices to differentiate from other users. Recognition is related to the validation of the claimed identity. When a user gives a password, it matches with the saved password and identifies an individual (Schiller et al. 2022a ).
Privac: To safeguard the privacy of individual data, security measures are implemented. It also ensures that data must be responsibly handled. It involves protecting personnel information (Schiller et al. 2022a ).
Authentication: The authentication measures procedure involves confirming the identities of individuals and protecting against unauthorized access. It involves the user providing a username and password (Schiller et al. 2022a ).
Availability Availability refers to the accessibility and usage of data when required by an authenticated person. It involves maintaining availability includes protecting against denial of service, downtime, and disruptions that can hamper the availability of data (Schiller et al. 2022a ).
Integrity Integrity ensures that data should be consistent, accurate, and unchangeable throughout its lifecycle. It also ensures the trustworthiness of the data (Schiller et al. 2022a ).
Case studies that demonstrate how these security goals are implemented in practice are described below:
Estonia’s e-Residency Program: e-Residents receive a government-issued digital ID that is stored on a blockchain. This ID allows them to securely sign documents, access Estonian e-services, and run a business remotely.
MediLedger in Pharmaceutical Supply Chain: MediLedger uses blockchain, a decentralized ledger, to ensure data integrity and transparency.
Civic’s blockchain-based identity verification: It allows users to create and verify digital identities. Further, Enigma uses secure multi-party computation ( sMPC ) on the blockchain to ensure that data can be shared and analyzed without being exposed.
5 Taxonomy of Cloud-IoT environment
In the rapidly growing landscape of the Cloud-IoT environment, understanding the taxonomy is significant for navigating the complexities of connected devices and realizing their full potential in the swift diversification of the Cloud-IoT ecosystem.
5.1 The relationship between IoT, Big Data, and cloud computing
There is a strong synergistic relationship between Cloud Computing, Big Data, and the IoT, with each technology augmenting the other’s capabilities. IoT enables data collection which is uploaded to the cloud for storage and processing. These bulk data are accumulated in the cloud and form a large volume of data known as Big Data. Big Data tools and techniques are applied to these bulk data for processing and scrutiny of data on the cloud. Real-time monitoring and analysis are made possible by the convergence of cloud computing, Big Data, and IoT. This makes it possible to respond and act quickly, which optimizes processes, boosts productivity, and enhances user experiences.
Figure 3 illustrates the relationship between the IoT devices that are placed at remote locations. Data is generated from IoT devices which are stored and analysed on the cloud using Big Data tools. Finally, after processing data on the cloud decision is made. IoT, Big Data, and cloud computing work together to create a potent trio that propels efficiency and innovation in a wide range of sectors, including manufacturing, agriculture, smart cities, and healthcare.
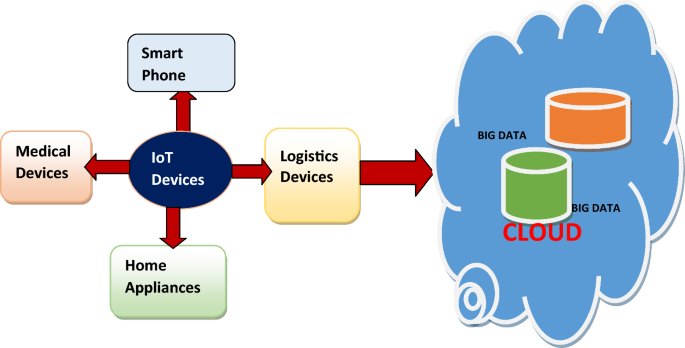
Relationship between IoT, Big Data, and cloud computing
5.1.1 Understanding the dynamics of Big Data
Big Data in a few years come out as an ideal that has provided an enormous amount of data and provided a chance to enhance and refine decision-making applications. Big Data offers great value and has been considered as being a driving force behind economic growth and technological innovation (Dutkiewicz et al. 2022 ). Machines and humans both contribute to data through online records, closed-circuit television streaming, and other means. Social media and smartphones create enormous amounts of data every minute (Ram Mohan et al. 2018 ). Big Data is a large amount of data that is fast and complex. These data are not easy to process using conventional methods. Today Giant Companies substantial portion of the value advanced from data generated by the company which is continually examined to produce better and advanced products. A prime example of Big Data is the New York Stock Exchange, which creates one terabyte of fresh trade data daily. Big Data characteristics are defined by the 4 V’s i.e. Volume, Variety, Velocity, and Veracity which is shown in the figure below. Big Data involves three main actions integration, managing, and analysis.
Figure 4 A and B illustrate the essential 4 V’s i.e. Variety, Volume Velocity, and Veracity of Big Data through 4 blocks. Volume block represents the size of data that grows exponentially such as Peta byte, Exa byte, etc. It represents how much information is present. The volume of data is increasing exponentially. Velocity block shows that data is streaming into the server for analysis and the outcome is only useful if the delay is short. It is used to portray how fast information can be available. Data must be generated quickly and should also be processed rapidly. For example, a healthcare monitoring system in which sensors record the activities that occur in our body and if an abnormal situation occurs needs a quick reaction. Variety blocks represent, a variety of data and various formats, types, and structures of data that exist such as sensor data, PDF, photo, video, social media data, time series, etc. The veracity block ensures that data should be consistent, relevant, and complete in itself. Hence, the error can be minimized accurate results can be produced and decisions can be taken through analysis of the result.
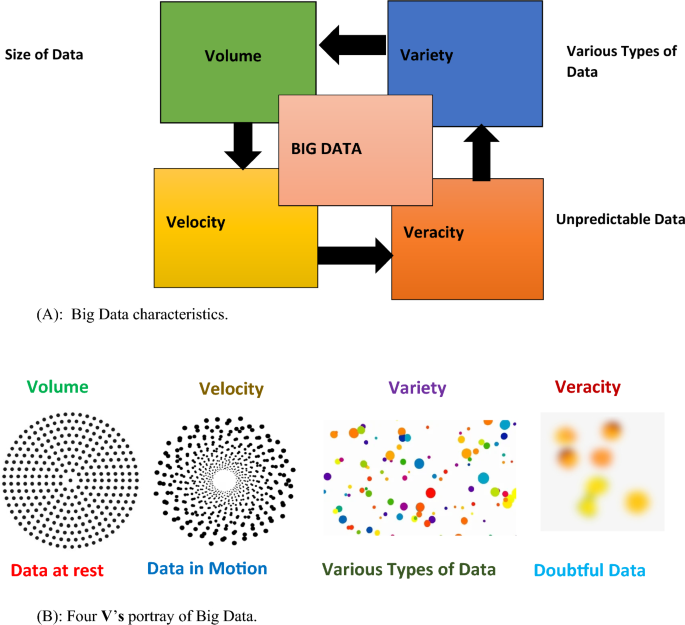
A Big Data characteristics. B Four V’s portray of Big Data
Apart from its several advantages Big Data faces security challenges as well such as attackers can damage or steal information where a large volume of data is stored such as cloud and fog. An attacker can steal data and he/she can attempt to study and analyze data and thereafter can change the outcome of the result accordingly. Therefore special protection and privacy of data such as cryptographic defense mechanisms should be provided so that data can be kept safe and secure (Kaaniche and Laurent 2017 ). The healthcare industry is one of the most promising areas where Big Data may be used to effect change. Large-scale medical data holds great promise for bettering patient outcomes, anticipating epidemics, gaining insightful knowledge, preventing avoidable diseases, lowering healthcare costs, and enhancing overall quality of life. To address security and privacy threats in healthcare, the author has provided some suggested strategies and approaches that have been documented in the literature, while also outlining their drawbacks (Abouelmehdi et al. 2018 ).
5.1.2 Connecting the world: the evolution and impact of the Internet of Things
The development of the Internet of Things has revolutionized the Internet market around the world. The Internet of Things is a device that when connected to the Internet transmits, receives, and stores data over the cloud. The Internet of Things is embedded with several devices such as sensors, physical devices, and software to control the devices. IoT can be device can include anything that contains a UID (Unique Identification Number) that can be used to in identify uniquely over the internet. IoT devices have several benefits such as high efficiency, providing more business opportunities, high productivity, increased mobility, and many more. Apart from the above-mentioned benefits, IoT devices can also be deployed to monitor tool execution and find and diagnose the issues before any major break happens in the functioning of the device, also in addition it reduces maintenance costs and thereby increases the throughput. IoT devices can able to gather large volumes of data beyond any human can think of it. As the world is developing data is considered to be an oil for the development of any country, so to cope with new challenges IoT devices should also be made smarter than traditional devices which can able to guide and make decisions. To achieve such objectives IoT devices should be accompanied by machine learning and artificial intelligence technology to enhance the performance of the device and to make sense of collected data.
Figure 5 illustrates the key components of IoT devices. The components are the building blocks of IoT which is shown in the diagram. These “DGCAU” components collectively facilitate the working of the IoT devices. Each component is significant in terms of productivity, data collection, monitoring, and connectivity. In Fig. 5 ‘D’ stands for IoT Device. IoT devices are those which are such as medical equipment, smart meters, home security systems, smart lights, etc. which are used to collect data. The second ‘G’ stands for Gateway which is similar to a centralized hub that is used to interconnect IoT devices and sensors to the cloud. Advanced gateway facilitates data flow in both directions between IoT devices and the cloud. ‘C’ indicates the cloud aids in the storage of data and simultaneously analyzing data. Rapid processing and strong control mechanisms enable cloud-enabled IoT devices to minimize the risk of attack. User identities and data are protected by strict authentication methods, encryption tools, and biometric authentication in Internet of Things devices. ‘A’ signifies the Analysis of data that was stored in the cloud to determine the outcome. Analysis tool studies large amounts of data and produces useful information, which is helpful in decision-making. The last component ‘U’ represents the user interface or UI module that facilitates the user to administer the IoT device with which they are interacting. it is generally a graphical user interface that includes a display screen, mouse, keyboard, etc.
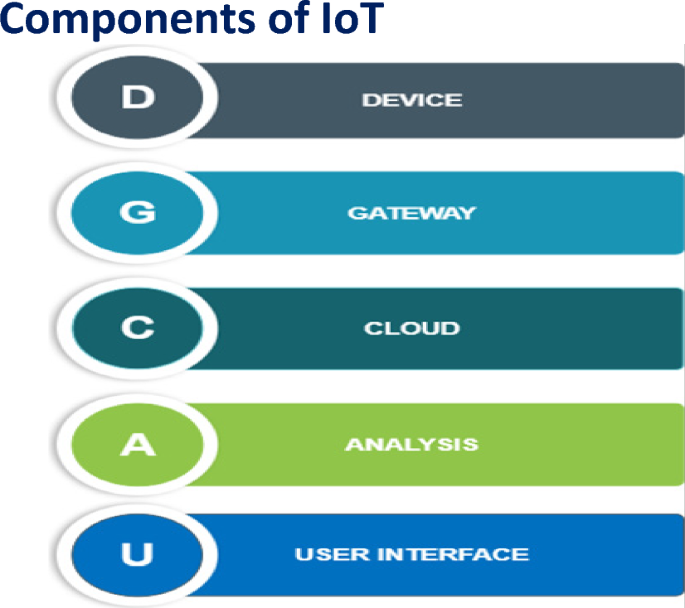
Key components of the Internet of Things
Figure 6 shows the various applications of the IoT which are technology paradigms used to interconnect the devices with the Internet, collect data, share data, transmit data, and act upon data. IoT has enormous application in day-to-day life therefore enabling us to perform our work widely and conveniently . Smart Lighting IoT can be used to operate the light remotely through a smartphone. Transportation IoT is used to track vehicles and goods in real-time. IoT finds application in health which enables doctors to monitor the patients remotely. In Logistics IoT helps to keep track of goods and vehicle devices. IoT is useful for smart framing because IoT sensors can monitor, measure, and track soil moisture, nutrients needed for crop fertilization, and irrigation needs. IoT devices used in retail monitor the department’s real-time inventory level and stock and forward orders when a product is discovered to be out of stock. With features like motion sensors, doorbell cameras, and video surveillance , smart home security systems employ the Internet of Things to monitor and secure houses. IoT is used by smart grids to increase the effectiveness and dependability of electricity delivery. Water quality indicators like pH, turbidity, chlorine levels, and pollutants are continuously monitored by IoT sensors. Smart meters with IoT capabilities allow for real-time monitoring of utility consumption. IoT equipment on autonomous vehicles processes sensor data in real time. This entails reading and assessing the environment to make deft choices regarding safety, navigation, and vehicle control. Wearable gadgets gather information on activities, health, and other topics before sending it for analysis to smartphones or the cloud for processing.
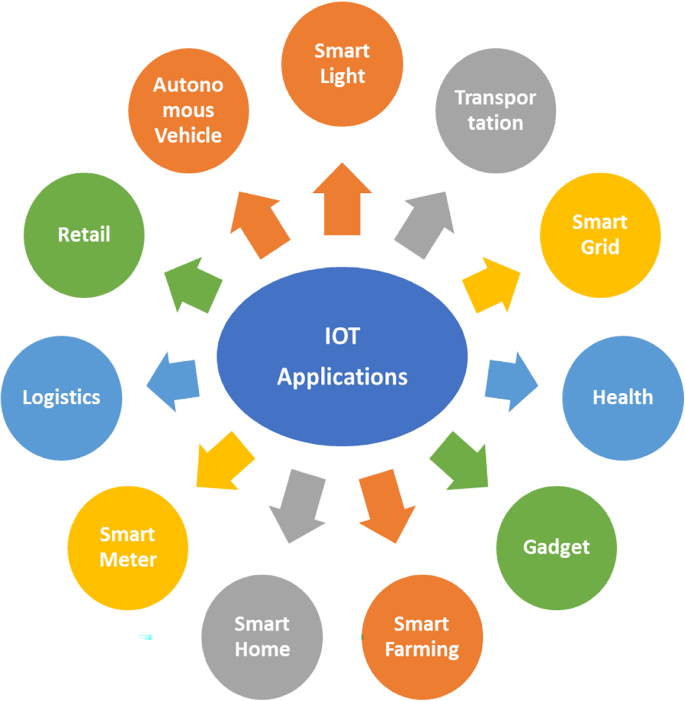
Internet of Things applications
Apart from the benefits of IoT devices in day-to-day life, IoT devices suffer security threats as well. The rapid growth of IoT devices has revolutionized how we interact with technology. As the number of IoT devices increases the security concern also increases simultaneously. The author addresses the issue of sharing sensitive data securely for designated recipients in the context of the Blockchain Internet of Things (B-IoT) (Yin et al. 2022 ). The author has scrutinized the security flaws in computer systems based on cloud, blockchain, IoT, and fog computing (Mishra et al. 2022 ; Yao 2022 ; Abdulkader 2022 ). Security challenges and threats in IoT and cloud environments addressed by various authors are presented in the papers (Pandey et al. 2023 ; Ray and Dutta 2020 ; Bedi et al. 2021 ). Cloud Computing and IoT Using Attribute-Based Encryption approaches are developed by authors found to be very effective in the security domain (Mihailescu et al. 2022 ; Henze et al. 2017 ). The author presents D-CAM, a solution for achieving distributed configuration, authorization, and management across borders between IoT networks (Simsek 2023 ). The study presented by the author is a novel handshake protocol for the broker-based publish/subscribe paradigm in the Internet of Things that offers key exchange-based authentication, authorization, and access control (Shin and Kwon 2020 ; Stergiou et al. 2018 ).The goal of a systematic literature review (SLR) paper is to examine the body of research on cloud computing security, risks, and difficulties that are presented by authors (Wang 2021 ). The primary issue in the cloud environment has been confirmed to be data access, despite the security measures being deemed dependable (Javid et al. 2020 ; Gai et al. 2021 ; Shukla 2022 ). We suggested an effective data access control method that uses optimal homomorphic encryption (HE) to get around this issue (Gnana Sophia et al. 2023 ). The paper highlights the edge computing security and privacy requirements (Yahuza et al. 2020 ). Multiple encryption techniques are presented by the authors which are significant in protecting privacy and data security (Sharma et al. 2019 ; Silva et al. 2018 ; Bertino 2016 ). The author proposes a distributed machine learning-oriented data integrity verification scheme (DML-DIV) to ensure the integrity of training data (Zhao and Jiang 2020 ). The researcher introduced an identity-based (ID-based) RDIC protocol including security against a malicious cloud server which is presented in the paper (Yu et al. 2017 ; Sookhak et al. 2018 ). The authors studied various security challenges concerning IoT devices, Big Data generated by IoT devices, and cloud and presented them in the paper (Akmal et al. 2021 ; Awaysheh et al. 2022 ; Tang 2020 ; Shi 2018 ).
5.2 Navigating the cloud: exploring the world of cloud computing
Cloud Computing refers to Internet-based computing, where shared resources data, software, and information are to the customer and devices on demand. The term “cloud” used to appear on the Internet. Huge memory space and inexpensive, high-performance computing are made possible by the cloud computing paradigm. Users can get cost savings and productivity benefits to manage projects and develop collaborations by moving their local data management system to cloud storage and utilizing cloud-based services. Information and knowledge extraction is greatly aided by computing infrastructure, particularly cloud computing. The services for cloud computing are provided using the network, generally the Internet. The characteristics of cloud computing include broad network access, on-demand service, rapid elasticity, and many more. With the help of the cloud, numerous services are accessible to clients. Broadly there are three types of services offered that enable the client to use software, platform, and infrastructure. Several types of cloud can be subscribed to by anyone as per the requirement of an individual or any organization. These include private cloud, public cloud, and hybrid cloud. Private cloud solely owned by any business houses. In this type of cloud infrastructure software is preserved on a private network and hardware and software entirely belong to the organization. Public clouds are commonly cloud services that are allotted to various subscribers. Third-party owned and operated the cloud resource.
The public cloud is mostly used for online office applications, testing, development, etc. A hybrid cloud is a combination of public and private clouds, which is implemented by a couple of interrelated organizations. Common types of cloud services are presented through the 3-layer architecture of Cloud Services in Fig. 7 and each one is discussed.
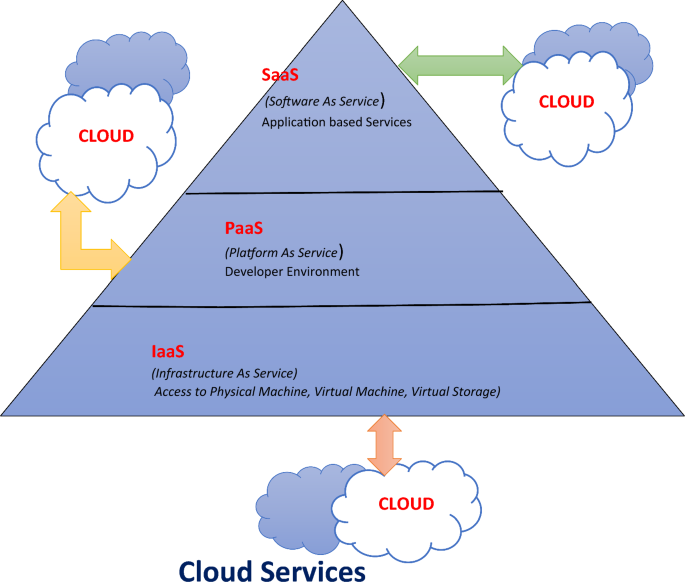
3-Layer architecture of cloud services
Figure 7 exhibits the different types of cloud and services provided by the cloud. The figure conveys the three-layer architecture of the cloud. IaaS makes virtualized computing resources available via the internet, enabling customers to pay-as-you-go access and manage the essential parts of the infrastructure. These resources often include storage, networking, virtual machines, and other things. Platform as a Service (PaaS) is a cloud computing architecture that offers developers a platform and environment to create, deploy, and manage applications. PaaS provides a variety of tools and services that speed up and improve the efficiency of the application development process. A cloud computing approach called Software as a Service (SaaS) allows users to access software programs online. SaaS has many benefits, including affordability, scalability, and accessibility.
Because crucial data is processed and stored on the cloud, for instance in Internet of Things applications, it also poses security and privacy issues (Alouffi et al. 2021 ; Hamzah Amlak and Kraidi Al-Saedi 2023 ; Yu et al. 2022 ). Cloud security is an important area where authors have tried to find the best possible solution through their research they have highlighted the challenges of possible solutions to the problem through finding and investigation in the paper (Gupta et al. 2022 ; Chaowei et al. 2017 ; Wang et al. 2021 ).
To ensure the integrity of data kept in the cloud, the author’s study proposes an effective public auditing technique that makes use of Third third-party auditor (TPA) (Reddy 2018 ; Hiremath and Kunte 2017 ; Yan and Gui 2021 ). The author proposes an efficient certificate-based data integrity auditing protocol for cloud-assisted WBANs (wireless body area networks (Li and Zhang 2022 ). The author proposed a secure architecture by associating DNA cryptography, HMAC, and a third-party auditor to provide security and privacy (Kumar 2021 ; Duan et al. 2019 ). Adversaries are always coming up with new ways to get access to users’ devices and data through developing technologies like the cloud, edge, and IoT. The author discussed various attacks along with security solutions (Pawlicki et al. 2023 ). The paper highlights the research challenges and directions concerning cyber security to build a comprehensive security model for Electronic health records (Chenthara et al. 2019 ; Hou et al. 2020 ; Ishaq et al. 2021 ; Jusak et al. 2022 ). The author mentioned the research and analysis of privacy-preserving data mining (PPDM) and classified using various approaches for data modification in the research paper (Binjubeir et al. 2020 ).
Even with all the benefits mentioned, there are security and privacy issues while using cloud computing (Nanda et al. 2020 ; Himeur et al. 2022 ). The issue of data security and privacy for Big Data is complicated by the use of cloud computing for Big Data management, storage, and applications. Since cloud services are typically offered on a common infrastructure, there is always potential for new attacks, both internal and external, such as password theft or application programming interface (API) flaws. The author has proposed a software architecture model by using approaches like hardware security extensions (Intel SGX) and homomorphic encryption. To improve data security in large data cloud environments and defend against threats, a virtualization design and related tactics are suggested by the author. The TID (Token Identification) model developed by the author provides security to the data. The user has various access rights as a client. The authentication access token establishes a connection with the user account after the user logs into the cloud network. The researchers have developed the Remote Data Checking (RDC) technique, which uses the sampling technique to evaluate the integrity of data that is outsourced across remote servers. Authors developed the techniques for remote data auditing that are very beneficial in ensuring the integrity and dependability of the data that is outsourced. Data, auditing, monitoring, and output these elements are all included in the DAMO taxonomy. The author in his paper offers a unique security-by-design framework for the implementation of BD (Big Data) frameworks via cloud computing (Big Cloud) (Ye et al. 2021 ). Various data security issues in the Big Data cloud computing environment are addressed by the authors in his paper. Various methods for safeguarding privacy and data security in public clouds are covered in the article (Jain et al. 2016 ). A multi-cloud architecture with privacy and data security enabled is suggested by the author. To increase user security on SNg (Social Networking) by utilizing techniques that can give data about BD technology (Big Data) greater privacy. This approach is described by the author in the paper along with various metrics and usage-related outcomes. The author examines financial risk analysis and related regulatory studies using blockchain and Big Data technologies. A secure cloud environment can be achieved by using a hybrid cryptographic system (HCS), which combines the advantages of symmetric and asymmetric encryption.
Figure 8 shows a hierarchical structure created to handle and process data and applications efficiently depending on how close they are to the user or the source of the data. “Hierarchical edge computing” refers to the interplay between these three layers, cloud, fog, and edge. The Cloud Layer is a centralized data processing center that provides abundant computing and storage capacity for handling and storing enormous volumes of data as well as running sophisticated applications. The growths of the Internet and its associated ideas, such as edge computing, cloud computing, and the Internet of Things, have had a permanent impact. The cloud layer is a highly scalable data center that is perfect for managing large-scale applications and services because they can extend horizontally to manage increased workloads.
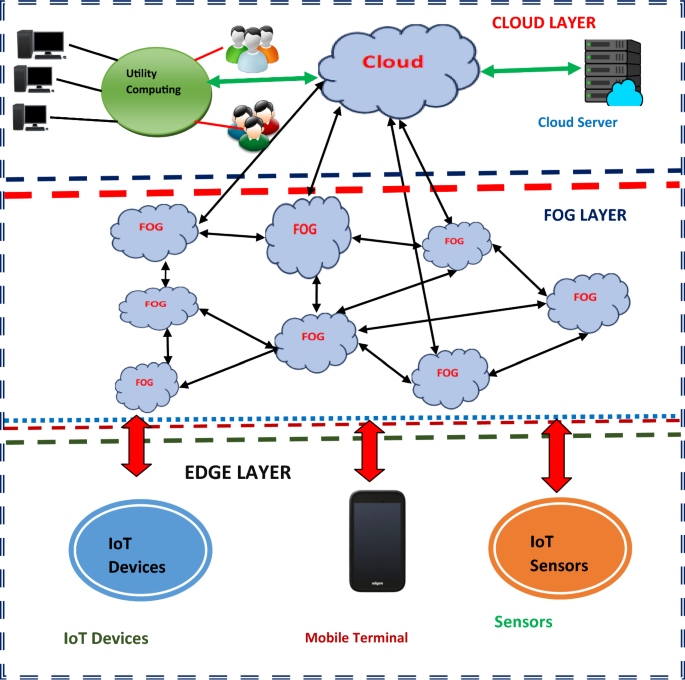
Hierarchical edge computing
The fog Layer is an intermediate layer after the cloud layer which spreads and distributes processing responsibilities among several local servers or devices, which can be very useful for IoT applications with many data sources. Fog computing is ideal for latency-sensitive applications that demand quick responses. Virtual components called cloudlets are employed in fog computing. Fog computing has emerged as a promising paradigm in overcoming the growing challenges (e.g., low latency, location awareness, and geographic distribution) arising from many real-world IoT applications, by extending the cloud to the network edge. To facilitate data offloading and computation, these virtual computers offer a micro data centre close to mobile devices (Lu et al. 2020 ). Fog computing offers new insights into the extension of cloud computing systems by procuring services to the edges of the network. It shortens the time it takes for data to go to the cloud and back by processing it closer to the source. The edge layer, which is frequently located adjacent to IoT medical devices themselves (Muzammal et al. 2018 ), is the one that is nearest to the data source or end users. A promising paradigm that expands on cloud computing capabilities is edge computing. It processes data instantly, allowing for extremely quick replies devices, sensor devices, and industrial machinery, mobile terminals are examples of edge devices that can function autonomously and make decisions in the present without relying on a central cloud infrastructure (Ghaffar et al. 2020 ; Jiang et al. 2016 ). Big Data applications are a risk for cyber security assaults, as these attacks directly affect applications utilized across several sectors, such as Big Data analytics. The authors presented a novel data encryption approach, which is known as Dynamic Data Encryption Strategy (D2ES) to protect and safeguard the data which proves promising in cloud computing. Encrypted data can be obtained by cryptography methods, enabling secure communication links within the networking system. Researchers suggested the blockchain-based Shamir threshold cryptography solution for IIoT (Industrial Internet of Things) data protection. An improved data security in mobile edge computing, the Fine-Grained Access Control mechanism (FGAC) is suggested to guarantee data security during data access (Ahmed et al. 2021 ).To analyze and investigate the data reduction at the fog level, researchers attempted to create a model. This researcher has successfully applied methods including artificial intelligence, principal component analysis (PCA), and the Naïve Bayesian classifier for data reduction.
6 Exploring the complex landscape of Cloud-IoT threats: an in-depth analysis
Security concerns are growing along with the integration of Cloud Computing and the IoT. Numerous dangers and vulnerabilities that might compromise the availability, confidentiality, and integrity of data and services are brought about by the junction of these two technologies. We examine the subtleties, possible effects, and vital necessity of strong security measures to protect against changing hazards in interconnected environments as we delve into the complex nature of Cloud-IoT security concerns in this analysis.
Figure 9 illustrates the numerous types of attacks that can take place in the cloud. These Attacks can harm the cloud service provider as well as cloud customers. The attacker is an individual who attempts to use a cloud infrastructure, platform, or service’s vulnerabilities or flaws for nefarious reasons in the world of cloud computing. Because they frequently house significant data and offer computational resources that may be used for a variety of purposes, such as launching cyber-attacks, stealing confidential information, or causing disruption, cloud systems are very alluring targets for attackers. For different purposes, including data theft, service interruption, or resource exploitation, attackers target cloud environments. To breach cloud systems, attackers use a range of methods and tactics. These attack methods can include insider threats, sniffer attacks password change SQL-Ingestion, Eavesdropping, malware, distributed denial-of-service (DDoS) attacks, phishing, and more (Basit et al. 2021 ; Ullah et al. 2019 ; Jahromi et al. 2021 ).
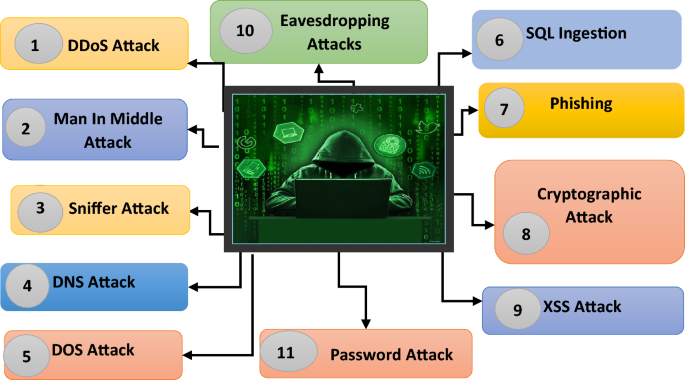
Threats in cloud computing environment
DDOS Attack A distributed denial-of-service attack aims to disrupt regular network operations by flooding the network with traffic. Denial-of-service attacks aim to prevent end users from accessing the network.
Man-in-Middle Attack In a man-in-middle attack, the attacker generally modifies the conversation between the two parties. In a man-in-the-middle attack, attackers generally eavesdrop on sensitive information and alter the conversation. The integrity and security of sensitive data are seriously threatened by MitM attacks.
Sniffer Attack It is an attack in which an unauthorized person intercepts and gains control over network traffic. The goal is to capture and examine the data when it passes over the network.
DNS Attack The domain name system attacks the domain name system, which is responsible for converting human name readable to IP address. DNS attacks have the potential to affect the DNS infrastructure’s availability, integrity, and confidentiality, which could cause interruptions to internet services.
DOS Attack A Denial of Service (DoS) assault involves the exploitation of a single source, typically a compromised device or computer, to overwhelm a target’s resources and cause a loss of service.
SQL Ingestion In SQL (Structure Query Language Ingestion), attackers ingest harmful code inside the parameters of a web application. The main goal of attackers is to manipulate SQL databases. In this type of attack, the attacker gains the advantage of bad input, which enables the attacker to execute the SQL command.
Phishing Attack In Phishing attackers use some trick to expose delicate information, for example, username, personal information, password, and credit card details. Phishing attacks sometimes use the personas of reliable companies, banks, or websites to trick people into doing things that could jeopardize their security.
Cryptographic Attacks Cryptography is important to ensure confidentiality and integrity and authenticate the user. The attacker exploits vulnerability or weakness in the existing system. Attackers compromise the security of cryptographic systems.
XSS Attacks Cross-site scripting (XSS) is one of the serious attacks that occur when vulnerable code which is in the form of a script is injected into the web page of the user. The objective of the attacker is to steal sensitive information about the user by running the scripting code in the user’s browse.
Eavesdropping Attacks Eavesdropping is a kind of attack in which attacker unauthorized person tries to listen to or sniff the conversation between two people and steal information. In this type of attack, the attacker even manipulates the information.
Password Change Request Interception Attack The assailant attempts to intercept legitimate users’ password changes. Interception of this kind could happen during a browser-server conversation.
7 Exploring research trends and areas of focus
As technology continues to evolve at a rapid pace, researchers and academics are continually exploring new trends and areas of focus within their respective fields. To keep ahead of new difficulties, seize opportunities, and encourage innovation, this investigation is essential. We explore the current research trends and areas of attention in a variety of disciplines in this overview, offering insight into the cutting-edge subjects that are influencing the direction of technological and scientific advancement. After scrutinizing the number of published research papers we came across various domains in which researchers have worked and proposed various security frameworks.
Table 1 represents the research work and focus of various researchers in field security. From the table above it can be concluded that researcher have focused on Cloud Computing and their finding are more concentrated on Cloud security and the Internet of Things. The researcher primarily focused on the development of security algorithms to protect the data from being damaged or corrupted by cyber attackers. Through study, it was found that researchers have developed innovative techniques by making use of machine learning techniques, and blockchain technology to safeguard data developed for the Internet of Things.
Cryptography is another eminent way to protect our data. Researchers have created algorithms to encrypt and decrypt data prominently so that data can be safely transmitted over the network. A method like PSEBVC: Provably Secure ECC and Biometric Based Authentication Framework is developed by the author as a countermeasure for attacks.
In the digital landscape, the risks of cyber-attacks are growing enormously which is becoming a challenge for both organizations and individuals. A comprehensive examination of attack vectors and mitigation strategies is essential for understanding and effectively countering these attacks (Wylde et al. 2022a , b ). Through an analysis of numerous attack pathways and related mitigation techniques including artificial intelligence-based solutions discussed in paper (Al Hamid et al. 2017 ; Abed and Anupam 2022 ). This research paper aims to offer important insights on how to enhance security and defend against cyber threats in a constantly changing security environment. The objective of this analysis is to provide individuals and organizations with the necessary knowledge and tools to improve their digital security and minimize risks in the constantly changing threat landscape. To do this, each attack mechanism is thoroughly examined, and appropriate remedies are explored through Table 2 .
Table 2 is a complete description of the investigation of the several research papers related to security threats that exist, various categories of attackers that occur on the cloud, and countermeasures that can be taken to prevent attacks summarized in the Table by the author. The table shows how attacks affect the data and what standard approaches were developed by researchers to protect data.
8 Unveiling the intricacies of digital forensics in Cloud-IoT environments
Digital Forensics is a branch of forensic science that concentrates on recovery of data, analysis of data and exhibit the digital evidence that is found on electronic devices. The IoT Forensics can be identified as part of Digital Forensics. The objective of IoT Forensics is to explore digital information in an authorized manner. IoT forensics data can be accumulated through IoT devices, sensors, networks, and cloud. There are some differences between security, IoT, and forensics. The protection against physical and logical security threats is provided by IoT security adopts multiple methods to protect from threats and minimize attacks (Unal et al. 2018 ). Forensics examines the data present in the devices and recreates the happenings by utilizing investigative methods to preserve and analyze digital data. Post-mortem examinations are the main focus of forensics i.e. discovering shortcomings that emerged from the event. Forensic experts obtain digital proof throughout the actual event with the help of standard approaches used in forensic analyses of physical proofs of electronic data to determine and reframe the events by storing and analysis of digital information using different methods of investigation. Some authors have presented detailed studies to investigate the forensic issues in cloud computing and provide possible solutions, and guidelines, including existing case studies (Morioka and Sharbaf 2016 ; Al-Dhaqm et al. 2021 ). The paper offers an enhanced blockchain-based IoT digital forensics architecture that builds the Blockchain’s Merkle tree using the fuzzy hash in addition to the traditional hash for authentication (Mahrous et al. 2021 ). Authors Almutairi and Moulahi ( 2023 ) trained models locally using federated learning on data stored on the IoT devices using a dataset created to simulate attacks in the IoT environment. In order to make the blockchain lightweight, the authors next carried out aggregation via blockchain by gathering the parameters from the IoT gateway (Almutairi and Moulahi 2023 ).
The IoT has revolutionized various sectors through seamless device interactions, yet it has introduced significant security and privacy challenges. Traditional security measures often fall short due to IoT’s distinct characteristics like heterogeneity and resource limitations. Danish Javed et al. ( 2024a ) explored the synergy of quantum computing, federated learning, and 6G networks to bolster IoT security. Quantum computing enhanced encryption, while federated learning preserved data privacy by keeping training data on local devices. Leveraging 6G’s high-speed, low-latency capabilities allows for secure, real-time data processing among IoT devices. The study also reviewed recent advancements, proposed a framework for integrating these technologies, and discussed future directions for IoT security. Recent innovations in network communication have revolutionized the industrial sector with automatic communication through the Industrial Internet of Things (IIoT) . Despite its benefits, the increased connectivity and use of low-power devices in IIoT heighten vulnerability to attacks, and its diverse nature complicates centralized threat detection. To tackle this, authors Javed et al. ( 2023 ) proposed a fog-based Augmented Intelligence (IA) defense mechanism that uses GRU and BiLSTM deep learning classifiers for anomaly detection and secure communication. This framework (Cu-GRU-BiLSTM), which achieved up to 99.91% accuracy, surpassed existing threat detection methods, proving its effectiveness for securing IIoT environments (Javeed et al. 2023 ).
Further, the hybrid approach proposed by Danish Javed et al. ( 2024b ) enhances intrusion detection in federated learning (FL) for IoT by addressing existing limitations. Here, CNNs identify local intrusion patterns by extracting spatial features, while BiLSTM captures sequential patterns and temporal dependencies. Using a zero-trust model, data stays on local devices, and only the learned weights are shared with the centralized FL server. The server then combines updates to improve the global model’s accuracy. Tests on CICIDS2017 and Edge-IIoTset datasets show this method outperforms centralized and federated deep learning-based IDS.
9 Advancements in security threat detection and avoidance
With the constant advancement in sophistication of cyber attacks, enterprises, and individuals alike are obliged to use innovative methods and technologies to detect, prevent, and mitigate potential security breaches. Threat detection is seeing tremendous breakthroughs, enabling defenders to keep one step ahead of malicious actors. These advancements include machine learning algorithms and behavior analysis methodologies. This ongoing change emphasizes how crucial it is to take preventative action to protect sensitive data and maintain digital trust in an environment where dangers are becoming more complicated.
9.1 Harnessing the power of machine learning
Machine learning is a subset of artificial intelligence (AI) that focuses on developing models and algorithms that enable computers to learn from data and make decisions or predictions without having to be explicitly programmed to do so. As a result, machine learning algorithms are beneficial when dealing with vast amounts of data since, after being trained on the data (Ali et al. 2020 ), the trained model uses its learning experience to present precise outcomes on new data. Data generated by IoT devices may suffer from threats (Safaei Yaraziz et al. 2023 ). Today Machine Learning proves to be one of the strongest tools to identify threats and maintain the integrity of data in transmission. The foundation of machine learning is the algorithms that are used to train the models. The first step in using machine learning to address a problem is gathering data. Next come tasks like data preparation, data analysis, training, testing, and eventually deploying the model for real-world application. Two types of ML problems can be solved by supervised machine learning algorithms: regression and classification. Classification is used to solve problems with binary target variables ( yes / no ), while Regression ML algorithms are used to address problems of similar nature when the target variable is continuous. A phishing attack has become one of the most prominent attacks faced by internet users, and governments. The attacker(s) transmits URL(s) to the intended victims via text messaging, social networking, or spam messages. They do this by mimicking the behavior of authentic websites when creating website pages. Malware attack during data in transit is a common type of attacks that can manipulate the data and damage the data. To prevent such attacks ML model can be one of the tools to identify such attacks and prevent them to such extents. Machine Learning algorithms have been used to build several intrusion detection systems, improving the systems’ ability to identify threats and enabling uninterrupted business operations (Pathak et al. 2023 ). Despite many benefits that SDN(Software-Defined Networking) offers such as offer nimble and adaptable network growth, malicious attacks that can eventually prevent network services are unavoidable (Unal et al. 2018 ). Machine learning has been used in several studies to detect distributed denial of service (DDoS) threats in SDN (Software-Defined Networking) environments (Morioka and Sharbaf 2016 ). ML models are being trained on numerous datasets to build models that can detect cloud attacks with elevated accuracy. Various classifier is implemented in the ML model to identify attacks such as SVM, Decision tree, K-NN (K-Nearest Neighbour), Convolutional Neural Networks (CNNs), Recurrent Neural Networks (RNNs), random forests, and many more. The use of random forest and K-NN classification approaches enables malware detection method proofs to be 99.7% accuracy and 99.9% in several cases (Abed and Anupam 2022 ; Morioka and Sharbaf 2016 ). These classifiers can be used with different feature engineering and feature selection strategies to create machine learning models that effectively handle certain security issues and enhance overall cyber security posture.
Figure 10 represents security threat detection using machine learning algorithms and models. The automatic detection of potential security threats and abnormalities within a file system using machine learning techniques uses a predictive model to identify the threat and classifies it as a malware file or harmless file over the system. Data breaches and other security problems can be prevented because of their ability to assist enterprises in detecting and responding to threats more quickly and effectively. In this process, it involves two important stages. The first stage is the Training stage where the model is being trained using different files. Files are sent as input to train the model. Numerous machine learning algorithms, such as decision trees, random forests, support vector machines (SVM), neural networks, and others, can be used for training the model. After the model is trained, then comes to the security stage where an unknown file is given to the model for analysis the file. For the detection of security threats, supervised learning techniques like classification and regression are frequently used. The machine learning model generates notifications for security professionals to investigate when it spots a potential security danger or abnormality. Automated responses to lessen or control the crisis may also be triggered based on how serious the threat is. Deep learning approach is used to detect pirated software and malware-infected files across the IoT network. Using color picture visualization, the deep CNN is utilized to identify harmful infections in Internet of Things networks. Secure video transmission over the cloud is discussed in the paper (Hossain et al. 2018 ). Researchers have developed Holistic Big Data Integrated Artificial Intelligent Modelling (HBDIAIM) to provide and improve privacy and security in data management (Chen et al. 2021 ). The previously developed model falls short in providing adequate data privacy and security, keeping this shortcoming in mind author (Yazdinejad et al. 2024a ) developed an Auditable Privacy-Preserving Federated Learning (AP2FL) model tailored for electronics in healthcare. AP2FL model provides secure training and aggregation processes on the server side as well as the client side. Thereby protecting and minimizing the risk of data leakage. Researchers primarily focus on Machine learning-based threat detection models to address the challenges within Consumer IoT. Using Federation Learning (FL) techniques data privacy in Consumer IoT is maintained (Namakshenas et al. 2024 ). The author suggests an approach to attack detection that makes use of deep learning (DL) algorithms to identify false data injection (FDI) assaults (Sakhnini et al. 2023 ). In the research paper, the author utilizes federated learning to automatically search for threats in blockchain-based IIoT (Industrial Internet of Things) networks using a threat-hunting framework we call block hunter (Yazdinejad et al. 2022 ).
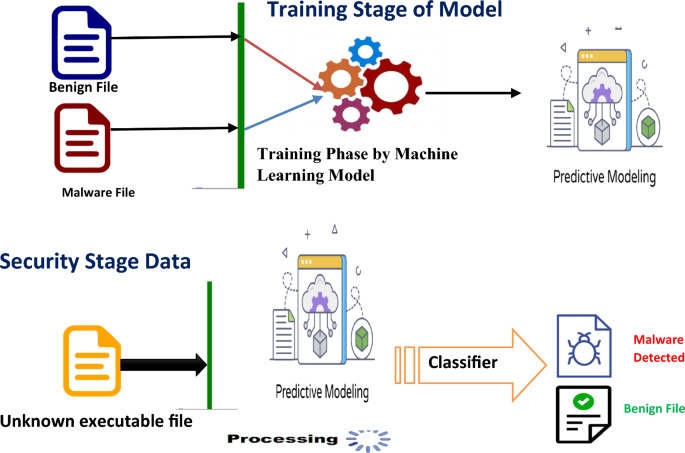
Security threat detection using machine learning technique
Real-life applications of machine learning in malware detection
AT&T Uses machine learning to protect networks and find malware that targets telecom infrastructure.
Mayo Clinic A healthcare organization that implements machine learning techniques to safeguard patient data from malware attacks and unauthorized access.
Bank of America Employs AI and machine learning to improve cyber security safeguards, identifying malware and averting breaches in data.
Cylance A cyber security firm that heavily relies on machine learning to identify and eradicate malware. To identify threats instantly, its algorithm is trained on an extensive dataset of both malicious and benign files.
Amazon Web Services (AWS) AWS uses machine learning techniques to identify threats, examining the logs and network traffic.
Symantec An American consumer-based software company that employs machine learning techniques to identify and categorize malware.
National Security Agency (NSA) To improve national cyber security, the National Security Agency (NSA) uses cutting-edge machine learning algorithms to identify and analyze malware.
9.2 Unlocking the power of blockchain: a cutting-edge safeguard technique for enhanced security in the digital landscape
Blockchain is an emerging decentralized technology that securely stores and authenticates transactions across a network of computers. Its decentralized and open structure makes it a viable option for many companies looking to improve digital security, efficiency, and trust. Although cloud computing is becoming more and more popular for processing and storing data, security, and privacy are still big issues because of the possibility of hostile assaults on wireless and mobile communication networks. Data transfer privacy and system security are improved by using blockchain technology. To put it briefly, a blockchain is auditable, can function as a distributed ledger with digitally signed data, and allows changes to be tracked back to the original data to ensure security. This demonstrates that the security of data may be guaranteed by blockchain technology (Safaei Yaraziz et al. 2023 ). The suggested IAS protocol is developed on top of blockchain technology to guarantee the security and authenticity of data transmission in cloud computing. A potential solution to the security and privacy problems in the Internet of Things is blockchain technology (Williams et al. 2022 ; Waheed et al. 2020 ). For every transaction including proper authentication, data can pass through the blockchain distributed ledger thanks to blockchain technology, which does away with the idea of an IoT central server. Blockchain technology could provide a more effective answer to the issues that IoT systems confront. Transactional privacy, decentralization, the immutability of data, non-repudiation, transparency, pseudonymity, and traceability, as well as integrity, authorization, system transparency, and fault tolerance, are the primary security features of blockchain technology. The Smart contact is verified, put into use, and then shared as a Distributed Ledger Technology (DLT) over a Pier-to-Pier (P2P) network as a function of blockchain (Wylde et al. 2022b ). The authors created and put into use smart, secure fuzzy blockchain architecture. This framework makes use of a unique fuzzy DL model, improved adaptive neuro-fuzzy inference system (ANFIS)-based attack detection, fuzzy matching (FM), and fuzzy control system (FCS) for network attack detection (Yazdinejad et al. 2023 ).
Figure 11 illustrates the specification of blockchain technology concerning cloud environment. Blockchain is a distributed ledger across a peer-to-peer network. Blockchain features can help cloud services reach their full potential and address the many problems that arise. A collection of connected building blocks that are coupled and arranged in an appropriate linear sequence is used to keep a detailed record of all transactions. Decentralization, Security, transparency, availability, traceability, and many more are the essential features of blockchain technology which is highlighted by the figure presented by the author.
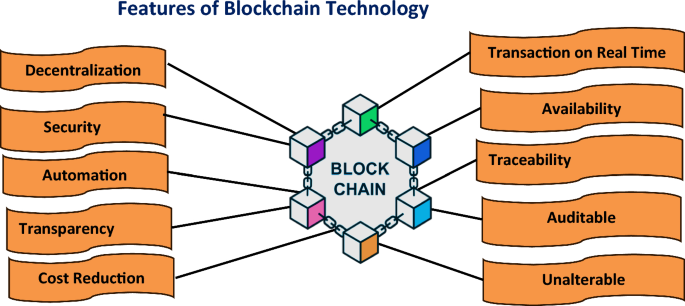
Specifications of blockchain technology
Decentralization Decentralization in blockchain technologies refers to the dividing of control and decision-making across the network users instead of concentrating on the centralized entity. It addresses the limitations of a centralized system in which security is compromised.
Security The network architecture of blockchain technology provides security by minimizing the risk of failure. The allocated characteristics of blockchain strengthen the security. Attacks on any nodes are less likely to put the entire network at risk.
Automation An intelligent system automates the carrying out of the consensus, and removes the requirement of human intervention. Smart contact enhances transaction efficiency. It automatically implements the terms and conditions of the agreement whenever conditions or terms are fulfilled.
Transparency The transactions made on blockchain appeared to every participant over the network. The method not only provides trust and security to the data but also promotes accountability which helps to gain the faith of the user.
Cost Reduction In conventional systems, the settlement of financial transactions might take several days, causing delays and capital lockups. Blockchain eliminates the need for drawn-out clearing and settlement procedures by enabling very immediate transaction settlement.
Transaction in Real Time Transactions in real time can be made over the network. Real-time transaction implements techniques like Proof-of-stake to attain quick acknowledgment of transactions. This technique permits fast agreement among nodes on the validity of transactions.
Availability Transaction availability guarantees a user’s ability to communicate with the network and complete transactions dependably. Availability may still be impacted by network maintenance, upgrades, and sporadic problems.
Traceability Traceability features of blockchain enable to provide of transparent transactions. The transaction can be can be traced by the user. Blockchain is helpful in industries where the origin, transportation, and ownership of assets need to be accurately recorded and validated because of its traceability capabilities.
Auditable Real-time transaction auditing is made possible by the blockchain ledger’s transparency and immutability. At any time, participants can check the transaction history.
Unalterable The ability of blockchain to keep a safe and impenetrable record of transactions is one of its unchangeable features. Once information is posted to the blockchain, it is impossible to change, guaranteeing the information’s integrity and immutability.
Figure 12 portrays the basic components of blockchain. These components work in agreement to form a secure ledger system. Blockchain technology comprises those elements that work in agreement to formulate a secure and decentralized ledger. Supply chain management, decentralized applications, voting systems, healthcare, and property registration are the major applications of technology. Each component plays an important role in blockchain functioning.
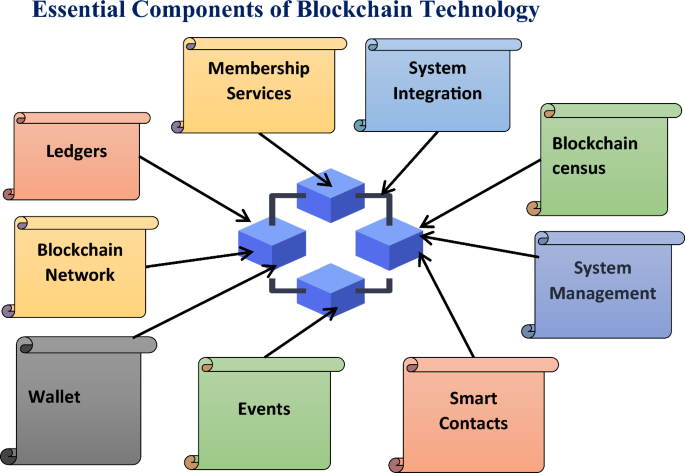
Basic building blocks for blockchain
Ledgers Ledgers in blockchain technology are used to maintain transparency of the record in transactions. Every node contains a replica of the complete ledger, protecting it from being altered or any kind of fraud. The ledger with the help of a chain of blocks carries out transactions; blocks represent every transaction in ledgers.
Blockchain Network In a Blockchain network, the user is referred to as nodes. All the users collectively validate the transaction and record the transaction in a synchronized manner. Blocks are depositors for a cluster of transactions. Blocks contain a timestamp, which is of location of preciously occurred transactions and a cryptographic has for the current blocks.
Wallet Blockchain technology wallets are tools that let users manage and store funds safely. It enables users to access the public and private keys, facilitating the blockchain’s ability to transfer and receive crypto-currency. There are two types of wallets Hot Wallets: Easy for frequent transactions and internet-connected. Cold wallets are offline and thought to be safer for storing money over time.
Events Events are essential for improving the automation, transparency, and usability of blockchain systems. They give decentralized networks a way to communicate and update in real time. The execution of smart contracts or modifications to the ledger’s current state is frequently linked to blockchain events.
Smart Contacts The blockchain records the complete history of smart contract execution, making it transparent and auditable. It has numerous applications such as in supply chain, finance, etc. Based on predetermined criteria, smart contracts carry out actions.
System Management Blockchain technology’s system management characteristics include a variety of operations and procedures meant to guarantee the safety, effectiveness, and appropriate operation of the blockchain network. These characteristics are essential to preserving the dependability and integrity of decentralized systems.
Blockchain Census The blockchain’s consensus techniques, like Proof of Work (PoW) and Proof of Stake (PoS), help make the system resistant to censorship. By requiring a distributed agreement from all network users, these mechanisms make it more difficult for one party to control or restrict transactions.
System Integration Establishing seamless connectivity between different blockchain networks and between blockchain technology and traditional systems is the aim of blockchain system integration. The successful communication and information sharing between diverse systems is greatly dependent upon standards, protocols, and APIs (Application Programming Interfaces).
Membership Services Membership services features of blockchain technology a functions and features for a member or participant management in a blockchain network. It is used to manage access control, rights, and user identity on the network. The elements of the blockchain ecosystem enhance its overall security, governance, and usefulness.
Figure 13 shows the internal workings of the blockchain technology which is used to perform any kind of transaction over the cloud securely. The figure above is a step-by-step explanation of how the transaction takes place over the cloud. In step 1 , first of all, the transaction is generated by any one of the users and request is the directed to the server for processing further. In step 2 , the server after receiving the transaction request creates a block that can appear for the transaction. Next step i.e. step 3 a chain or interconnect block is created using algorithms to authenticate the user and ensure that the request is being made by the authenticated user. Further, in step 4 , this block is distributed to other users or groups of users to grant permission for the transaction to happen. Once the group of users grants permission the transaction or block will be successfully added to the existing blocks that are shown in step 5 in the above figure. If any user disapproves or denies it, then the block will not be added to the existing chain. The modification that has taken place is permanent and cannot be modified further. Therefore, it ensures data security in the cloud environment.
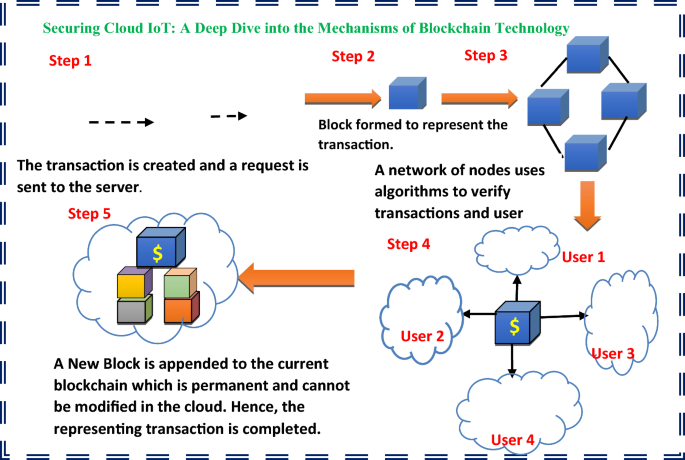
Functioning of blockchain technology in Cloud IoT systems
Real-World Applications of Blockchain Technology in Enhancing Security and Data Protection is as follows:
Walmart Walmart one of the retail companies collaborated with IBM to implement blockchain technology to track the movement of products, maintain food safety, and minimizes the possibility of contamination.
MedRec MedRec is an MIT-developed blockchain-based electronic medical record system that gives individuals more control over their health information while maintaining confidentiality and privacy.Allows for real-time transactions and decentralized energy management by utilizing blockchain to increase the security and efficiency of energy distribution.
Ripple Ripples operates in the financial sector. It uses blockchain techniques to protect the data and enables real-time secure payment.
Follow My Vote Follow My Vote creates a safe, open, and verifiable online voting system using blockchain technology.
uPort uPort is a blockchain-based self-governing identity platform that empowers people to take control of their online personas while improving security and privacy.
10 Unveiling the challenges: addressing current issues in data security and privacy within the Cloud IoT environment
10.1 open ended problems.
The open-ended problems and primary issues about data security and privacy in cloud IoT systems are summarized in Table 3 . Table 3 also provides targeted solutions to address each challenge, thereby ensuring a robust and secure cloud-IoT ecosystem.
10.2 Research gaps
The research gaps of data security and privacy preservation in cloud-IoT technologies are described in Table 4 .
11 Conclusions
The IoT is on the verge of substantial expansion, necessitating secure data transfer and robust cloud storage solutions. As IoT devices become more widespread, the need for enhanced cloud security is critical. Current methods, while helpful, do not fully address modern threats, thus requiring the development of more advanced protective systems. Manufacturers can improve security by creating products grounded in a detailed assessment of IoT security risks and objectives. Effective measures include the implementation of strong authentication methods like One Time Password (OTP) features and robust cryptographic systems. While Machine Learning (ML) is widely used for data protection in various sectors, it faces challenges such as scalability issues with small data sets. Integrating ML with homomorphic encryption shows promise but needs further development. The evolving sophistication of hackers compels reliance on ML and AI for defense strategies. Additionally, blockchain technology, supported by platforms like Ethereum and Hyper-ledger Fabric, offers considerable potential for enhancing security, though more research is necessary to standardize these techniques.
The authors recommend three key solutions:
Develop new security standards and frameworks for cloud-based and IoT devices to tackle modern security challenges.
Create more efficient ML models for real-time attack prediction.
Design robust privacy protection protocols for blockchain technology to safeguard sensitive data.
The authors encountered several limitations during their research, including restricted access to relevant literature, challenges in avoiding plagiarism, difficulties in summarizing a large body of research, integrating information logically, and keeping up with the latest studies.
Data availability
The data and material used in this paper are appropriately referred to and described in this paper.
Code availability
The source code/custom code/software application will be provided when required.
Abdulkader ZA (2022) Cloud data security mechanism using the lightweight cryptography. Optik 271:170084
Article Google Scholar
Abdulsalam YS, Hedabou M (2021) Decentralized data integrity scheme for preserving privacy in cloud computing. In 2021 International conference on security, pattern analysis, and cybernetics (SPAC), Chengdu, China, pp 607–612
Abed AK, Anupam A (2022) Review of security issues in the Internet of Things and artificial intelligence-driven solutions. Internet Technol Lett. https://doi.org/10.1002/spy2.285
Abouelmehdi K, Beni-Hessane A, Khaloufi H (2018) Big healthcare data: preserving security and privacy. J Big Data 5:1
Ahmed W et al (2021) Security in next generation mobile payment systems: a comprehensive survey. IEEE Access 9:115932–115950
Ahmad W, Rasool A, Javed AR, Baker T, Jalil Z (2022) Cyber security in IoT-based cloud computing: a comprehensive survey. Electronics 11:16
Akmal M, Syangtan B, Alchouemi A (2021) Enhancing the security of data in cloud computing environments using Remote Data Auditing. In: 2021 IEEE 6th International conference on innovative technology in intelligent system and industrial applications (CITISIA), Sydney, Australia, pp 1–10
Alabdulatif A, Thilakarathne NN, Kalinaki K (2023) A novel cloud enabled access control model for preserving the security and privacy of medical Big Data. Electronics 12:2646
Albugmi A, Alassafi MO, Walters R, Wills G (2016) Data security in cloud computing. 2016 Fifth International conference on future generation communication technologies (FGCT), London, UK, pp. 55–59
Al-Dhaqm A et al (2021) Digital forensics subdomains: the state of the art and future directions. IEEE Access 9:152476–152502
Al Hamid HA, Rahman SMM, Hossain MS, Almogren A, Alamri A (2017) A security model for preserving the privacy of medical Big Data in a healthcare cloud using a fog computing facility with pairing-based cryptography. IEEE Access 5:22313–22328
Ali J, Roh BH, Lee B, Oh J, Adil M (2020) A machine learning framework for prevention of software-defined networking controller from DDoS attacks and dimensionality reduction of Big Data. In: 2020 International conference on information and communication technology convergence (ICTC), Jeju, Korea (South), pp 515–519
Almutairi W, Moulahi T (2023) Joining federated learning to blockchain for digital forensics in IoT. Computers 12:157
Alnaim AK, Alwakeel AM (2023) Machine-learning-based IoT–edge computing healthcare solutions. Electron MDPI 12:1027
Google Scholar
Alouffi B, Hasnain M, Alharbi A, Alosaimi W, Alyami H, Ayaz M (2021) A systematic literature review on cloud computing security: threats and mitigation strategies. IEEE Access 9:57792–57807
Alrasheed SH, Aiedalhariri M, Adubaykhi SA, El Khediri S (2022) Cloud computing security and challenges: issues, threats, and solutions. In: 2022 5th Conference on cloud and Internet of Things (CIoT), Marrakech, Morocco, pp 166–172
Alzoubi YI, Ahmad AAA, Jaradat A (2021) Fog computing security and privacy issues, open challenges, and blockchain solution: an overview. Int J Electr Comput Eng (IJECE) 11(6):5081–5088
Andrew J, Karthikeyan J (2019) Privacy-preserving Internet of Things: techniques and applications. Int J Eng Adv Technol (IJEAT) 8(6):3229
Arora A, Khanna A, Rastogi A, Agarwal A (2017) Cloud security ecosystem for data security and privacy. In: 2017 7th International conference on cloud computing, data science & engineering - confluence, Noida, India, IEEE, pp 288–292
Atiewi S, Al-Rahayfeh AA, Almiani M, Yussof S, Alfandi O, Abugabah A, Jararweh Y (2020) Scalable and secure Big Data IoT system based on multifactor authentication and lightweight cryptography. IEEE Access 8:113498–113511
Awaysheh FM, Aladwan MN, Alazab M, Alawadi S, Cabaleiro JC, Pena TF (2022) Security by design for Big Data frameworks over cloud computing. IEEE Trans Eng Manage 69(6):3676–3693
Ayofe Azeez NA, Vyver CVD (2019) Security and privacy issues in e-health cloud-based system: a comprehensive content analysis. Egyptian Inform J 20(2):97–108
Basit A, Zafar M, Liu X et al (2021) A comprehensive survey of AI-enabled phishing attacks detection techniques. Telecommun Syst 76:139–154
Bedi RK, Singh J, Gupta SK (2021) An efficient and secure privacy-preserving multi-cloud storage framework for mobile devices. Int J Comput Appl 43:1–11
Bertino E (2016) Big Data security and privacy. In: 2016 IEEE International conference on Big Data (Big Data), Washington, DC, USA, pp 3–3
Binjubeir M, Ahmed AA, Ismail MAB, Sadiq AS, Khurram Khan M (2020) Comprehensive survey on Big Data privacy protection. IEEE Access 8:20067–20079
Butpheng C, Yeh K-H, Xiong H (2020) Security and privacy in IoT-cloud-based e-health systems—a comprehensive review. Symmetry MDPI 12:1191
Campos EM, Saura PF, González-Vidal A, Hernández-Ramos JL, Bernabé JB, Baldini G, Skarmeta A (2022) Evaluating federated learning for intrusion detection in Internet of Things: review and challenges. Comput Netw 203:108661
Cha SC, Hsu TY, Xiang Y, Yeh K-H (2019) Privacy enhancing technologies in the Internet of Things: perspectives and challenges. IEEE Internet Things J 6(2):2159–2187
Chaowei Y, Qunying H, Zhenlong L, Kai L, Fei H (2017) Big Data and cloud computing: innovation opportunities and challenges. Int J Digit Earth. https://doi.org/10.1080/17538947.2016.1239771
Chen J, Ramanathan L, Alazab M (2021) Holistic Big Data integrated artificial intelligent modelling to improve privacy and security in data management of smart cities. Microprocess Microsyst 81:103722
Chen Q, Wu L, Jiang C (2022) ES-PPDA: an efficient and secure privacy-protected data aggregation scheme in the IoT with an edge-based XaaS architecture. J Cloud Comp 11:20
Chenthara S, Ahmed K, Wang H, Whittaker F (2019) Security and privacy-preserving challenges of e-health solutions in cloud computing. IEEE Access 7:74361–74382
Choudhury T, Gupta A, Pradhan S, Kumar P, Rathore YS (2017) Privacy and security of Cloud-Based Internet of Things (IoT). In: 2017 3rd International conference on computational intelligence and networks (CINE), Odisha, India, pp 40–45
Duan H, Zheng Y, Wang C, Yuan X (2019) Treasure collection on foggy islands: building secure network archives for Internet of Things. IEEE Internet Things J 6(2):2637–2650
Dutkiewicz L et al (2022) Privacy-preserving techniques for trustworthy data sharing: opportunities and challenges for future research. In: Curry E, Scerri S, Tuikka T (eds) Data spaces. Springer, Cham
Gai K, Qiu M, Zhao H (2021) Privacy-preserving data encryption strategy for Big Data in mobile cloud computing. IEEE Transact Big Data 7(4):678–688
Ghaffar Z, Ahmed S, Mahmood K, Islam SH, Hassan MM, Fortino G (2020) An improved authentication scheme for remote data access and sharing over cloud storage in cyber-physical-social-systems. IEEE Access 8:47144–47160
Gnana Sophia S, Thanammal KK, Sujatha SS (2023) Secure storage and accessing the data in the cloud using optimized homomorphic encryption. J Control Decision. https://doi.org/10.1080/23307706.2022.2078436
Gupta I, Singh AK, Lee C-N, Buyya R (2022) Cloud computing research center, secure data storage and sharing techniques for data protection in cloud environments: a systematic review, analysis, and future directions. IEEE Access. https://doi.org/10.1109/ACCESS.2022.3188110
Hamzah Amlak GM, Kraidi Al-Saedi KH (2023) Data mining techniques for cloud privacy preservation. Int J Intell Syst Appl Eng 11(6s):246–256
Hassija V, Chamola V, Saxena V, Jain D, Goyal P, Sikdar B (2019) A survey on IoT security: application areas, security threats, and solution architectures. IEEE Access 7:82721–82743
Henze M, Wolters B, Matzutt R, Zimmermann T, Wehrle K (2017) Distributed configuration, authorization and management in the cloud-based Internet of Things. 2017 IEEE Trustcom/BigDataSE/ICESS, Sydney, NSW, Australia, pp 185–192
Himeur Y, Sohail SS, Bensaali F, Amira A, Alazab M (2022) Latest trends of security and privacy in recommender systems: a comprehensive review and future perspectives. Comput Secur 118:102746
Hiremath S, Kunte S (2017) A novel data auditing approach to achieve data privacy and data integrity in cloud computing. In: 2017 International conference on electrical, electronics, communication, computer, and optimization techniques (ICEECCOT), Mysuru, India, pp 306–310
Hong-Yen T, Jiankun H (2019) Privacy-preserving Big Data analytics a comprehensive survey. J Parallel Distribut Comput 134:207–218
Hossain MS, Muhammad G, Abdul W, Song B, Gupta BB (2018) Cloud-assisted secure video transmission and sharing framework for smart cities. Futur Gener Comput Syst 83:596–606
Hou Y, Garg S, Hui L, Jayakody DNK, Jin R, Hossain MS (2020) A data security enhanced access control mechanism in mobile edge computing. IEEE Access 8:136119–136130
Hurrah NN, Parah SA, Sheikh JA, Al-Turjman F, Muhammad K (2019) Secure data transmission framework for confidentiality in IoTs. Ad Hoc Netw 95:101989
Ishaq A, Qadeer B, Shah MA, Bari N (2021) A comparative study on securing electronic health records (EHR) in cloud computing. In: 2021 26th International conference on automation and computing (ICAC), Portsmouth, United Kingdom, pp 1–7
Jahromi AN, Karimipour H, Dehghantanha A, Choo K-KR (2021) Toward detection and attribution of cyber-attacks in iot-enabled cyber-physical systems. IEEE Internet Things J 8(17):13712–13722
Jain SK, Kesswani N (2023) A noise-based privacy-preserving model for the Internet of Things. Complex Intell Syst 9:3655–3679
Jain P, Gyanchandani M, Khare N (2016) Big Data privacy: a technological perspective and review. J Big Data 3:25
Jain P, Gyanchandani M, Khare N (2019) Enhanced secured map reduce layer for Big Data privacy and security. J Big Data 6:30
Javeed D, Gao T, Saeed MS, Khan MT (2023) FOG-Empowered augmented-intelligence-based proactive defensive mechanism for IoT-enabled smart industries. IEEE Internet Things J 10(21):18599–18608. https://doi.org/10.1109/JIOT.2023.3288563
Javeed D, Saeed MS, Ahmad I, Adil M, Kumar P, Najmul Islam AKM (2024a) Quantum-empowered federated learning and 6G wireless networks for IoT security: Concept, challenges and future directions. Futur Gener Comput Syst 160:577–597. https://doi.org/10.1016/j.future.2024.06.023
Javeed D, Saeed MS, Adil M, Kumar P, Jolfaei A (2024b) A federated learning-based zero trust intrusion detection system for Internet of Things. Ad Hoc Netw 162:103540. https://doi.org/10.1016/j.adhoc.2024.103540
Javid T, Faris M, Beenish H, Fahad M (2020) Cybersecurity and data privacy in the cloudlet for preliminary healthcare Big Data analytics. In: 2020 International Conference on Computing and Information Technology (ICCIT-1441), Tabuk, Saudi Arabia, pp 1–4
Jeong J, Joo JWJ, Lee Y, Son Y (2019) Secure cloud storage service using bloom filters for the Internet of Things. IEEE Access 7:60897–60907
Jiang Q, Kumar N, Ma J, Shen J, He D, Chilamkurti N (2016) A privacy-aware two-factor authentication protocol based on elliptic curve cryptography for wireless sensor networks. Int J Network Mgmt. https://doi.org/10.1002/nem.1937
Jusak J, Mahmoud SS, Laurens R, Alsulami M, Fang Q (2022) A new approach for secure cloud-based electronic health record and its experimental testbed. IEEE Access 10:1082–1095
Kaaniche N, Laurent M (2017) Data security and privacy preservation in cloud storage environments based on cryptographic mechanisms. Comput Commun 111:120–141
Kabir AA, Elmedany M, Sharif W, Saeed M (2023) Securing IoT devices against emerging security threats: challenges and mitigation techniques. J Cyber Secur Technol. https://doi.org/10.1080/23742917.2023.2228053
Karie NM, Sahri NM, Yang W, Valli C, Kebande VR (2021) A review of security standards and frameworks for IoT-based smart environments. IEEE Access 9:121975–121995
Kaur K, Syed A, Mohammad A, Halgamuge MN (2017) Review: an evaluation of major threats in cloud computing associated with Big Data. In: 2017 IEEE 2nd International conference on Big Data analysis (ICBDA), Beijing, China, pp 368–372
Khan S, Parkinson S, Qin Y (2017) Fog computing security: a review of current applications and security solutions. J Cloud Comp 6:19
Khan HK, Pradhan R, Chandavarkar BR (2021) Hybrid cryptography for cloud computing. In: 2021 2nd International conference for emerging technology (INCET), Belagavi, India, pp 1–5
Krishnaraj N, Sangeetha S (2022) A study of data privacy in Internet of Things using privacy preserving techniques with its management. Int J Eng Trends Technol 70(3):54–65
Kumar S, Tiwari P, Zymbler M (2019) Internet of Things is a revolutionary approach for future technology enhancement: a review. J Big Data 6:111
Kumar A (2021) Framework for data security using DNA cryptography and HMAC technique in cloud computing. In: 2021 Second International conference on electronics and sustainable communication systems (ICESC), Coimbatore, India, pp 898-903
Kumar V, Alameemi AMA, Kumari A, Ahmad M, Falah MW, Abd El-Latif AA (2022) PSEBVC: provably secure ECC and biometric based authentication framework using smartphone for vehicular cloud environment. IEEE Access 10:84776–84789
Kumar A, Khan SB, Pandey SK et al (2023) Development of a cloud-assisted classification technique for the preservation of secure data storage in smart cities. J Cloud Comp 12:92
Li Y, Zhang F (2022) An efficient certificate-based data integrity auditing protocol for cloud-assisted WBANs. IEEE Internet Things J 9(13):11513–11523
Lin J, Yu W, Zhang N, Yang X, Zhang H, Zhao W (2017) A survey on Internet of Things: architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J 4(5):1125–1142
Loai AT, Gokay S (2021) Reconsidering Big Data security and privacy in cloud and mobile cloud systems. J King Saud Univ Comput Inform Sci 33(7):810–819
Lone AN, Mustajab S, Alam M (2023) A comprehensive study on cybersecurity challenges and opportunities in the IoT world. Secur Privacy 6:e318
Lu X, Pan Z, Xian H (2020) An efficient and secure data sharing scheme for mobile devices in cloud computing. J Cloud Comp 9:60
Mahfoudhi S, Frehat M, Moulahi T (2019) Enhancing cloud of things performance by avoiding unnecessary data through artificial intelligence tools. In: 2019 15th International wireless communications & mobile computing conference (IWCMC), Tangier, Morocco, pp 1463–1467
Mahrous WA, Farouk M, Darwish SM (2021) An enhanced blockchain-based IoT digital forensics architecture using fuzzy hash. IEEE Access 9:151327–151336
Majeed A, Khan S, Hwang SO (2022) Toward privacy preservation using clustering based anonymization: recent advances and future research outlook. IEEE Access 10:53066–53097
Mei R, Yan HB, He Y, Wang Q, Zhu S, Wen W (2022). Considerations on evaluation of practical cloud data protection. CONCERT 2022. In: Communications in computer and information science, vol 1699. Springer, Singapore
Mihailescu MI, Nita SL, Asalomia BL, Rogobete MG, Racuciu C (2022) Customized authorization process for cloud computing and IoT using attribute-based encryption. In: 2022 14th International conference on electronics, computers and artificial intelligence (ECAI), IEEE Ploiesti, Romania, pp 1–4
Mishra JK, Janarthanan MC (2023) Cloud computing security: machine and deep learning models analysis. Macromol Symp 407:2100521
Mishra K, Bhattacharjee V, Saket S et al (2022) Cloud and Big Data security system’s review principles: a decisive investigation. Wireless Pers Commun 126:1013–1050
Mishra A, Jabar TS, Alzoubi YI, Mishra KN (2023) Enhancing privacy-preserving mechanisms in cloud storage: a novel conceptual framework. Concurr Computat Pract Exper. https://doi.org/10.1002/cpe.7831
Moqurrab SA, Tariq N, Anjum A et al (2022) A Deep learning-based privacy-preserving model for smart healthcare in Internet of medical things using fog computing. Wireless Pers Commun 126:2379–2401
Morioka E, Sharbaf MS (2016) Digital forensics research on cloud computing: An investigation of cloud forensics solutions. In: 2016 IEEE symposium on technologies for homeland security (HST), Waltham, MA, USA, pp 1–6
Moulahi T, El Khediri S, Ullah Khan R, Zidi S (2021) A fog computing data reduction level to enhance the cloud of things performance. Int J Commun Syst 34(9):e4812
Muzammal SM et al (2018) Counter measuring conceivable security threats on smart healthcare devices. IEEE Access 6:20722–20733
Nadian-Ghomsheh A, Farahani B, Kavian M (2021) A hierarchical privacy-preserving IoT architecture for vision-based hand rehabilitation assessment. Multimed Tools Appl 80:31357–31380
Namakshenas D, Yazdinejad A, Dehghantanha A, Srivastava G (2024) Federated quantum-based privacy-preserving threat detection model for consumer Internet of Things. IEEE Trans Consum Electron. https://doi.org/10.1109/TCE.2024.3377550
Nanda P, He X, Yang LT (2020) Security, trust and privacy in cyber (STPCyber): future trends and challenges. Futur Gener Comput Syst 109:446–449
Nasiraee H, Ashouri-Talouki M (2022) Privacy-preserving distributed data access control for CloudIoT. IEEE Trans Dependable Secure Comput 19(4):2476–2487
Navin Prasad S, Rekha C (2023) Blockchain-based IAS protocol to enhance security and privacy in cloud computing. Measur Sens 28:100813
Niu L, Wang F, Li J, Han T, Liu D (2019) Development of agricultural Internet of Things monitoring system combining cloud computing and WeChat technology. In: 2019 IEEE 8th Joint international information technology and artificial intelligence conference (ITAIC), Chongqing, China, pp 1457–1460
Ogunniye G, Kokciyan N (2023) A survey on understanding and representing privacy requirements in the Internet-of-Things. J Art Intell Res 76:163–192
Pandey NK, Kumar K, Saini G et al (2023) Security issues and challenges in a cloud of things-based applications for industrial automation. Ann Oper Res. https://doi.org/10.1007/s10479-023-05285-7
Pathak M, Mishra KN, Singh SP, Mishra A (2023) An automated smart centralised vehicle security system for controlling the vehicle thefts/hacking using IOT and facial recognition. In: 2023 International conference on computational intelligence and knowledge economy (ICCIKE), Dubai, United Arab Emirates, pp 516–521
Pawlicki M, Pawlicka A, Kozik R, Choraś M (2023) The survey and meta-analysis of the attacks, transgressions, countermeasures, and security aspects common to the Cloud Edge and IoT. Neurocomputing 551:126533
Pioli L, Dorneles CF, de Macedo DDJ et al (2022) An overview of data reduction solutions at the edge of IoT systems: a systematic mapping of the literature. Computing 104:1867–1889
Quach S, Thaichon P, Martin KD et al (2022) Digital technologies: tensions in privacy and data. J of the Acad Mark Sci 50:1299–1323
Rachit BS, Ragiri PR (2021) Security trends in Internet of Things: a survey. SN Appl Sci 3:121
Radoglou Grammatikis PI, Sarigiannidis PG, Moscholios ID (2019) Securing the Internet of Things: challenges, threats and solutions. Internet of Things 5:41–70
Rahman SMM, Hossain MA, Hassan MM, Alamri A, Alghamdi A, Pathan M (2016) Secure privacy vault design for distributed multimedia surveillance system. Futur Gener Comput Syst 55:344–352
Ram Mohan P, Murali Krishna S, Siva Kumar AP (2018) Privacy preservation techniques in Big Data analytics: a survey. J Big Data 5:33
Ravi Kumar P, Herbert Raj P, Jelciana P (2018) Exploring data security issues and solutions in cloud computing. Procedia Comput Sci 125:691–697
Ray SM, Dutta S (2020) Big Data security issues from the perspective of IoT and cloud computing: a review. Recent Adv Comput Sci Commun. https://doi.org/10.2174/2666255813666200224092717
Reddy Y (2018) Big Data security in cloud environment. In: 2018 IEEE 4th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International conference on high performance and smart computing, (HPSC) and IEEE international conference on intelligent data and security (IDS), Omaha, NE, USA, pp 100–106
Rejin PR, Paul RD, Alavi AH (2019) Verification of data integrity and co-operative loss recovery for secure data storage in cloud computing. Cogent Eng. https://doi.org/10.1080/23311916.2019.1654694
Rodríguez E, Otero B, Canal R (2023) A survey of machine and deep learning methods for privacy protection in the Internet of Things. Sensors 23:1252
Roslin Dayana K, Shobha Rani P (2023) Secure cloud data storage solution with better data accessibility and time efficiency. Automatika J Control Measur Electron Comput Commun 64(4):751–758
Sadhu PK, Yanambaka VP, Abdelgawad A (2022) Internet of Things: security and solutions survey. MDPI Sens 22:7433
Safaei Yaraziz M et al (2023) Recent trends towards privacy-preservation in the Internet of Things, its challenges and future directions. IET Circuits Devices Syst 17(2):53–61
Sakhnini J et al (2023) A generalizable deep neural network method for detecting attacks in industrial cyber-physical systems. IEEE Syst J 17(4):5152–5160
Sarwar K, Yongchareon S, Jian Yu, Rehman SU (2021) A survey on privacy preservation in fog-enabled Internet of Things. ACM Comput Surv 55(1):2
Schiller E, Andy A, Jara F, Jonathan S, Michael Z, Burkhard S (2022a) Landscape of IoT security. Comput Sci Rev 44:100467
Schiller E, Aidoo A, Fuhrer J, Stahl J, Ziörjen M, Stiller B (2022b) Landscape of IoT security. Comput Sci Rev Internet Things 44:100467
Selvarajan S, Srivastava G, Khadidos AO et al (2023) An artificial intelligence lightweight blockchain security model for security and privacy in IIoT systems. J Cloud Comp 12:38
Sharma Y, Gupta H and Khatri S. K. (2019) A Security Model for the Enhancement of Data Privacy in Cloud Computing. 2019 Amity international conference on artificial intelligence (AICAI), Dubai, United Arab Emirates, IEEE, pp 898–902
Shi Y (2018) Data security and privacy protection in public cloud. In 2018 IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, pp 4812–4819
Shin S, Kwon T (2020) A privacy-preserving authentication, authorization, and key agreement scheme for wireless sensor networks in 5G-integrated Internet of Things. IEEE Access 8:67555–67571
Shukla RS (2022) IoT based designing of secure data storage system in distributed cloud system with Big Data using cryptography algorithm. In: 2022 11th International conference on system modeling & advancement in research trends (SMART), Moradabad, India, pp 264-270
Sicari S, Rizzardi A, Coen-Porisini A (2022) Insights into security and privacy towards fog computing evolution. Comput Secur 120:102822
Silva LV, Barbosa P, Marinho R (2018) Security and privacy aware data aggregation on cloud computing. J Internet Serv Appl 9:6
Simsek I (2023) Zero-knowledge and identity-based authentication, authorization, access control, and key exchange for publish/subscribe in Internet of Things. In: 2023 6th conference on cloud and Internet of Things (CIoT), Lisbon, Portugal, pp 47–54
Singh N, Singh AK (2018) Data privacy protection mechanisms in cloud. Data Sci Eng 3:24–39
Sookhak M, Yu FR, Zomaya AY (2018) Auditing Big Data storage in cloud computing using divide and conquer tables. IEEE Trans Parallel Distrib Syst 29(5):999–1012
Stergiou C, Psannis KE, Xifilidis T, Plageras AP, Gupta BB (2018) Security and privacy of Big Data for social networking services in the cloud. IEEE INFOCOM 2018—IEEE conference on computer communications workshops (INFOCOM WKSHPS), Honolulu, HI, USA, pp 438–443
Sumithra R, Parameswari R (2022) Data privacy and data protection security algorithms for Big Data in the cloud. Int J Health Sci 6(S2):7613–7621
Sun PJ (2019) Privacy protection and data security in cloud computing: a survey, challenges, and solutions. IEEE Access 7:147420–147452
Tahirkheli AI, Shiraz M, Hayat B, Idrees M, Sajid A, Ullah R, Ayub N, Kim K-I (2021) A survey on modern cloud computing security over smart city networks: threats, vulnerabilities, consequences, countermeasures, and challenges. Electronics 10:1811
Tang Z (2020) A preliminary study on data security technology in Big Data cloud computing environment. In: 2020 International conference on Big Data & artificial intelligence & software engineering (ICBASE) IEEE, Bangkok, Thailand, pp 27–30
Thabit F, Alhomdy S, Jagtap S (2021) A new data security algorithm for cloud computing based on genetics techniques and logical-mathematical functions. Int J Intell Netw Sci Direct 2:18–33
Tian Y, Kaleemullah MM, Rodhaan MA, Song B, Al-Dhelaan A, Ma T (2019) A privacy-preserving location service for cloud-of-things system. J Parallel Distrib Comput 123:215–222
Ullah F et al (2019) Cyber security threats detection in Internet of Things using deep learning approach. IEEE Access 7:124379–124389
Unal E, Sen-Baidya S, Hewett R (2018) Towards prediction of security attacks on software defined networks: a Big Data analytic approach. In: 2018 IEEE International conference on Big Data (Big Data), Seattle, WA, USA, pp 4582–4588
Waheed N, He X, Ikram M, Usman M, Hashmi SS, Usman M (2020) Security and privacy in IoT using machine learning and blockchain: threats and countermeasures. ACM Comput Surv 53(6):122
Wang H (2021) Research on risk and supervision of financial Big Data application based on cloud computing. In: 2021 IEEE International conference on advances in electrical engineering and computer applications (AEECA), Dalian, China, pp 507–510
Wang F, Wang H, Xue L (2021) Research on data security in Big Data cloud computing environment. In: 2021 IEEE 5th advanced information technology, electronic and automation control conference (IAEAC), Chongqing, China, pp 1446–1450
Wang Y, Ni K, Wang X, Zhu J (2022) Design of automatic weather monitoring and forecasting system based on Internet of Things and Big Data. In: 2022 International conference on sustainable computing and data communication systems (ICSCDS), Erode, India, pp 979–982
Wazid M, Das AK, Hussain R, Succi G, Rodrigues JJPC (2019) Authentication in cloud-driven IoT-based Big Data environment: survey and outlook. J Syst Architect 97:185–196
Williams P, Dutta IK, Daoud H, Bayoumi M (2022) A survey on security in the Internet of Things with a focus on the impact of emerging technologies. Internet Things 19:100564
Wylde V, Rawindaran N, Lawrence J et al (2022a) Cybersecurity, data privacy, and blockchain: a review. SN Comput Sci 3:127
Wylde V, Rawindaran N, Lawrence J, Balasubramanian R, Prakash E, Jayal A, Khan I, Hewage C, Platts J (2022b) Cybersecurity, data privacy, and blockchain: a review. SN Comput Sci 3:127
Xiao Y, Jia Y, Liu C, Cheng X, Yu J, Lv W (2019) Edge computing security: state of the art and challenges. Proc IEEE 107(8):1608–1631
Xie Q, Zhang C, Jia X (2023) Security-aware and efficient data deduplication for edge-assisted cloud storage systems. IEEE Trans Serv Comput 16(03):2191–2202
Yahuza M et al (2020) Systematic review on security and privacy requirements in edge computing: state of the art and future research opportunities. IEEE Access 8:76541–76567
Yan H, Gui W (2021) Efficient identity-based public integrity auditing of shared data in cloud storage with user privacy preserving. IEEE Access 9:45822–45831
Yao H (2022) Data storage security system based on cloud computing. In: 2022 IEEE 2nd International conference on electronic technology, communication and information (ICETCI), Changchun, China, pp 1220–1223
Yazdinejad A, Dehghantanha A, Parizi RM, Hammoudeh M, Karimipour H, Srivastava G (2022) Block hunter: federated learning for cyber threat hunting in blockchain-based IIoT networks. IEEE Trans Industr Inf 18(11):8356–8366
Yazdinejad A, Dehghantanha A, Parizi RM, Srivastava G, Karimipour H (2023) Secure intelligent fuzzy blockchain framework: effective threat detection in IoT networks. Comput Ind 144:2023
Yazdinejad A, Dehghantanha A, Srivastava G (2024a) AP2FL: auditable privacy-preserving federated learning framework for electronics in healthcare. IEEE Trans Consum Electron 70(1):2527–2535
Yazdinejad A, Dehghantanha A, Srivastava G, Karimipour H, Parizi RM (2024b) Hybrid privacy-preserving federated learning against irregular users in next-generation Internet of Things. J Syst Architect 148:103088
Ye C, Cao W, Chen S (2021) Security challenges of blockchain in Internet of Things: systematic literature review. Trans Emerging Tel Tech 32:e4177
Yin H, Chen E, Zhu Y, Zhao C, Feng R, Yau SS (2022) Attribute-based private data sharing with script-driven programmable ciphertext and decentralized key management in blockchain Internet of Things. IEEE Internet Things J 9(13):10625–10639
Yu Y et al (2017) Identity-based remote data integrity checking with perfect data privacy preserving for cloud storage. IEEE Trans Inf Forensics Secur 12(4):767–778
Yu K et al (2022) A blockchain-based shamir’s threshold cryptography scheme for data protection in industrial Internet of Things settings. IEEE Internet Things J 9(11):8154–8167
Zaman S et al (2021) Security threats and artificial intelligence based countermeasures for Internet of Things networks: a comprehensive survey. IEEE Access 9:94668–94690
Zarandi MA, Dara Rozita A, Evan F (2020) A survey of machine learning-based solutions to protect privacy in the Internet of Things. Comput Secur 96:101921
Zhang J, Chen B, Zhao Y, Cheng X, Hu F (2018) Data security and privacy-preserving in edge computing paradigm: survey and open issues. IEEE Access 6:18209–18237
Zhang W, Jin S (2020) Research and application of data privacy protection technology in cloud computing environment based on attribute encryption. In: 2020 IEEE International conference on power, intelligent computing and systems (ICPICS), Shenyang, China, pp 994–996
Zhao X-P, Jiang R (2020) Distributed machine learning oriented data integrity verification scheme in cloud computing environment. IEEE Access 8:26372–26384
Zhou J, Cao Z, Dong X, Vasilakos AV (2017) Security and privacy for cloud-based IoT: challenges. IEEE Commun Mag 55(1):26–33
Zhu H et al (2019) A secure and efficient data integrity verification scheme for Cloud-IoT based on short signature. IEEE Access 7:90036–90044
Download references
Author information
Authors and affiliations.
Department of Computer Science & Engineering, Birla Institute of Technology, Jharkhand, India
Mayank Pathak, Kamta Nath Mishra & Satya Prakash Singh
You can also search for this author in PubMed Google Scholar
Contributions
Mayank Pathak, Kamta Nath Mishra and Satya Prakash Singh have equally contributed in writing this paper after having various discussions.
Corresponding author
Correspondence to Kamta Nath Mishra .
Ethics declarations
Conflicts of interest.
Being the corresponding author I declare that there is no conflict of interest with any person or organization for this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Pathak, M., Mishra, K.N. & Singh, S.P. Securing data and preserving privacy in cloud IoT-based technologies an analysis of assessing threats and developing effective safeguard. Artif Intell Rev 57 , 269 (2024). https://doi.org/10.1007/s10462-024-10908-x
Download citation
Accepted : 06 August 2024
Published : 27 August 2024
DOI : https://doi.org/10.1007/s10462-024-10908-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Blockchain technologies
- Cloud computing
- Data breach
- Data securities
- Digital forensic
- Fog computing
- Internet of Things
- Machine learning
- Privacy protection
- Find a journal
- Publish with us
- Track your research

IMAGES
VIDEO
COMMENTS
Table of contents. Step 1: Reading the text and identifying literary devices. Step 2: Coming up with a thesis. Step 3: Writing a title and introduction. Step 4: Writing the body of the essay. Step 5: Writing a conclusion. Other interesting articles.
Peer Review Instructions—Literary Analysis. For peer review, you will write comments on your peers' essays in two ways: 1) comments throughout the body of the essay in the form of specific questions, concrete suggestions, and corrections of grammar and MLA documentation, and 2) a concluding paragraph at the end of the essay (either at the bottom or on a separate sheet of paper) in which ...
5. Has the writer integrated quotes into the text appropriately? If not, note spots where the writer needs to do more. 6. Did the writer strike an effective balance between providing context for the evidence and plot summary? (Remember, an effective literary analysis does not rely on plot summary.) 7.
Literary analysis looks critically at a work of fiction in order to understand how the parts contribute to the whole. When analyzing a novel or short story, you'll need to consider elements such as the context, setting, characters, plot, literary devices, and themes. Remember that a literary analysis isn't merely a summary or review, but ...
As a reviewer . . . Step 1: First, read your peer's rhetorical analysis two times: once to get an overview of the paper, and a second time to provide constructive criticism for the author to use when revising his/her paper. Step 2: Answer the following questions. Question 1: Does the draft include an introduction that presents the topic and ...
Think about structuring your review like an inverted pyramid. Put the most important information at the top, followed by details and examples in the center, and any additional points at the very bottom. Here's how your outline might look: 1. Summary of the research and your overall impression. In your own words, summarize what the manuscript ...
According to a literary analysis essay definition, it is a written examination and interpretation of a literary work, typically dissecting its elements such as plot, characters, themes, and symbolism. Going beyond summarization, this type of essay delves into the intricacies of a text, aiming to uncover deeper meanings, explore the author's ...
LITERARY PEER REVIEW Amber Huett and Dr. Robert T. Koch, Jr. June 2011 UNA Center for Writing Excellence 1 Peer review is a vital component of workshop activity. Here are some guidelines we can use in our responses. 1. Remember that we are critiquing texts, not people or ideologies. When we speak about a text, let's use
You should have a complete analysis of your article with examples of the rhetorical elements as well as an evaluation of the overall article. Complete Peer Editing. This is worth 20 points. You will select two (2) papers. Write the names of your colleagues on the Discussion posting so that I know whose work you will review. I will look at their ...
HANDOUT 2: PEER REVIEW WORKSHEET. Switch papers with your partner. You will take turns reading each other's papers out loud; this is the procedure that. s followed in the writing center. Your roles as reader/consultant and listene. /consultee are equally important. Therefore, here are some guidelines to fol.
Use Peer Review to help students build strong literary analysis essay components. During Peer Review, students write a specific component of their essays (like their thesis statements) and then give and receive anonymous feedback from classmates to improve their writing. You can use Peer Review to help students focus on one part of their essays.
Peer review is a process in which you share your writing with other people and other people share their writing with you. The goal is to improve the quality of everyone's work. While you might not have ever completed peer review in a classroom setting, you've probably read over a friend's writing assignment or had a friend, parent, or ...
Peer Review. 1. Critical Analysis. 15. What stylistic techniques does the student discuss (for example, sentence length, repetition, lists, figurative language, use of quotation marks or italics)? 16. At some point during the essay, does the student discuss tone, audience, purpose, publication date, and point of view?
The most common types are: Single-blind review. Double-blind review. Triple-blind review. Collaborative review. Open review. Relatedly, peer assessment is a process where your peers provide you with feedback on something you've written, based on a set of criteria or benchmarks from an instructor.
When you are tasked with locating a literary criticism, most often this is due to a class assignment in your literature or English class.To first understand your task, you must understand what a literary criticism is and how it is used.. A literary criticism is an in-depth analysis of a literary work such as a poem, novel, short story, or play. A literary criticism is usually in the form of an ...
PEER REVIEW: Literary Analysis Essay. Student Reviewing (who is completing this sheet): Crystal Baker. Peer Being Reviewed (who wrote the paper) Holden Banks. For the section below, you cannot just write "yes" or "no." You must answer with complete sentences for the benefit of your peer.
1. Read and analyze the text. In order to understand how to start a literary analysis essay, you need to realize the importance of strong research. Before you begin writing your essay, make sure to thoroughly go through your text and take detailed notes. Observe and note the words used by the author, the structure and tone of the piece, the ...
Writing a literature review requires a range of skills to gather, sort, evaluate and summarise peer-reviewed published data into a relevant and informative unbiased narrative. Digital access to research papers, academic texts, review articles, reference databases and public data sets are all sources of information that are available to enrich ...
In short, this pattern of commenting encourages reviewers to 1. describe what they are reading and understanding from the text, 2. evaluate how well the text is working based on the rubric, assignment sheet, or class material, and 3. suggest next steps for improvement. Putting these three moves together in a comment helps your partner ...
The purposes of peer review of a literacy analysis essay are:. To find areas for improvement in the essay; To find out if the essay is engaging for readers; What is peer review? Peer review refers to the evaluation of a literary work by experts that is intended to improve the quality and validity of the writings.. The purpose of peer review is to properly analyze the essay and make necessary ...
Peer Review and Feedback form for a Text / Literary Analysis Response Essay. by. ELA Lab. 5.0. (2) $1.25. Word Document File. Included here is a Peer-Review Assignment where students swap Text/Literary Analysis essays and provide constructive criticism. Guidance is given on which components to grade via short prompts.
The questions that might be asked during a peer review of a literary analysis essay are options B and C.. What is a literary analysis essay? A literary analysis essay is a type of academic writing that examines a specific literary work, such as a novel, play, or poem, and analyzes various aspects of the work, including its themes, characters, plot, symbolism, and literary devices used by the ...
Children with intersex variations continue to be subject to elective, irreversible, "sex-normalising" surgical interventions, despite multiple human rights and legislative bodies calling for their prohibition. Our systematic review aims to understand how medical literature reports rationales for "sex-normalising" surgical interventions conducted in childhood, and how they are ...
The primary focus of the research studies (excluding the 11 narrative reviews and 2 policy documents) were classified as describing structure (n = 8, 14%); process (n = 21,36.8%) or outcomes (n = 29, 49.2%).The structure of acute care was described in seven studies out of eight studies (n = 7/8 87.5%) whilst neurosurgery structures were described in one out of eight studies (12.5%).
The articles included in the scoping review were from Japan (6), Austria (1), the Netherlands (2), and the United States (1). Nine papers were in English, and one was in German [].The article in German [] was initially translated by Google Translate, and the translation was reviewed by a research associate fluent in German.Of the ten papers, six focused on group homes (GH) in Japan, [2, 22,23 ...
Nudges are approaches that direct individuals to perform particular courses of action to meet a pre-determined goal, without coercion. Previous literature has explored the design of nudge and its impact on users' behavior in several domains and contexts. Still, scarce and fragmented knowledge about the design approaches, ethical considerations, and theoretical grounds have been presented by ...
Current approaches to gas path analysis are extended by incorporating EO data. The analytical approach is presented in combination with a literature review. The literature review covers the following topics: flight trajectory modeling, EO/environmental condition data, as well as engine performance, condition, and deterioration modeling.
The impacts of climate change (CC) are intensifying and becoming more widespread. Greenhouse gas emissions (GHGs) significantly contribute to CC and are primarily generated by transportation—a dominant segment of supply chains. City logistics is responsible for a significant portion of GHGs, as conventional vehicles are the primary mode of transportation in logistical operations. Nonetheless ...
Alcohol withdrawal syndrome (AWS) is defined as the cessation or reduction in heavy and prolonged alcohol use within several hours to a few days of cessation. The recommended first-line therapy for AWS ranging from mild to severe or complicated remains benzodiazepines; in cases where benzodiazepines are not adequate in controlling persistent autonomic hyperactivity or anxiety, dexmedetomidine ...
The Internet of Things (IoT) is a powerful technology adopted in various industries. Applications of the IoT aim to enhance automation, productivity, and user comfort in a cloud and distributive computing environment. Cloud computing automatically stores and analyzes the large amounts of data generated by IoT-based applications. Cloud computing has become a crucial component of the information ...